Phishing is the most prominent form of cyber-attack, regularly prompting email recipients into disclosing their personal information, …
How To Recall An Email In Outlook
Independent research shows that 91% of organizations have experienced outbound email security incidents in their Microsoft 365 environments. …
Humans Will Give AI Anything If You Make It Sound Cool Enough

There's a beautiful moment happening right now, and by "beautiful" I mean "horrifying in that can't-look-away-from-the-car-crash sense”.
AI-Assisted Social Engineering Attacks Continue to Rise

Social engineering remained the top initial access vector for cyberattacks in 2025, with increasing assistance from AI tools, according to a …
How To Recall An Email In Gmail

People accidentally send emails to the wrong recipients every day. The impact of these incidents can be relatively minor if there is no …
Report: AI-Driven Fraud Surged by 1200% in December 2025

AI-driven fraud attacks spiked by more than 1200% in December 2025, according to a new report by Pindrop Security. Threat actors are using AI …
Your Password Needs To Be 25 Characters or Longer Due to AI and Quantum Attacks

Prior to my further research into AI and quantum for my latest book, How AI and Quantum Impact Cyber Threats and Defenses, I had pretty solid …
Warning: Attackers Are Using DKIM Replay Attacks to Bypass Security Filters

Cybercriminals are abusing legitimate invoices and dispute notifications from popular services to send scam emails that bypass security …
Welcome to the Blur: Designing Security That Works With, Not Against, AI Adoption

There's a moment in every security professional's career when they realise the game has fundamentally changed. Mine came last Tuesday at 3:47 …
CyberheistNews Vol 16 #07 Uncovering the Sophisticated Phishing Campaign Bypassing M365 MFA

CyberheistNews Vol 16 #07 | February 17th, 2026 Uncovering the Sophisticated Phishing Campaign Bypassing M365 MFA …
North Korean Hackers Target Job Seekers With Phony Interviews

North Korean hackers continue to target software developers via social engineering attacks, according to researchers at Recorded Future.
New Book! How AI and Quantum Impact Cyber Threats and Defenses

I am excited to announce my latest book, How AI and Quantum Impact Cyber Threats and Defenses: Shaping Your Cyber Defense Strategies.
Voice Phishing Kits Give Threat Actors Real-Time Control Over Attacks

Researchers at Okta warn that a series of phishing kits have emerged that are designed to help threat actors launch sophisticated voice …
Uncovering the Sophisticated Phishing Campaign Bypassing M365 MFA

Lead Analysts: Jeewan Singh Jalal, Prabhakaran Ravichandhiran and Anand Bodke KnowBe4 Threat Labs has detected a sophisticated phishing …
Love in the Age of AI - Why 2026 Romance Scams are Almost Impossible to Spot

Valentine’s Day is usually a time for flowers and candlelight, but in recent years the digital dating landscape has shifted from a place of …
‘Digital Mindfulness’ Is Your Best Defense this Safer Internet Day

If you look back just a couple of years, the digital landscape looks almost unrecognizable. We’ve moved from AI being a cool new tool to it …
Your KnowBe4 Fresh Compliance Plus Content Updates | January 2026
-1.png)
The first requirements set forth for the EU AI Act start this month (February). Luckily, this regulation starts with some of the easiest …
New Malware Kit Promises Guaranteed Publication in the Chrome Web Store

A new malware-as-a-service (MaaS) kit called “Stanley” is offering users guaranteed publication in the Chrome Web Store, bypassing Google’s …
Your KnowBe4 Fresh Content Updates from January 2026
.png)
We are very excited that 2025 broke all of our records for usage and quality ratings of our content on the platform! Our 2025 records were…
Attackers Can Use LLMs to Generate Phishing Pages in Real Time

Researchers at Palo Alto Networks’ Unit 42 warn of a proof-of-concept (PoC) attack technique in which threat actors could use AI tools to …
The Phishing-as-a-Service Economy is Thriving

Commodity phishing platforms are now a central component of the cybercriminal economy, according to researchers at Flare. These platforms …
Report: One in Ten UK Companies Wouldn’t Survive a Major Cyberattack

A new survey by Vodafone Business found that more than 10% of companies in the UK would likely go out of business if they were hit by a major …
14.1 Million Reasons Your SEG and Email Security Tech is Failing

In the relentless growth of the phishing landscape, technical advances like AI have made attack methods two-pronged. They target technical …
Warning: A LinkedIn Phishing Campaign is Targeting Executives

A phishing campaign is abusing LinkedIn private messages to target executives and IT workers, according to researchers at ReliaQuest. The …
CyberheistNews Vol 16 #05 [Heads Up] New “Fancy” QR Codes Are Making Quishing More Dangerous

CyberheistNews Vol 16 #05 | February 3rd, 2026 [Heads Up] New “Fancy” QR Codes Are Making Quishing More Dangerous QR …
Starting the Year with Cyber Intention: Human-Centric Insights from the Global Cybersecurity Outlook 2026

One of my first intentional “to-dos” this year has been spending time with the World Economic Forum’s Global Cybersecurity Outlook 2026, a …
KnowBe4 Urges Action: Take Control of Your Data this Data Privacy Week

With organizations collecting and storing massive amounts of personal data these days, much of which people share freely, we need to become …
Warning: “Fancy” QR Codes Are Making Quishing More Dangerous

Scammers are increasingly using visually stylized QR codes to deliver phishing links, Help Net Security reports. QR code phishing (quishing) …
Report: 4 in 10 Employees Have Never Received Cybersecurity Training

Forty percent of employees have never received cybersecurity training, according to a new report from Yubico. That number rises to nearly …
New Phishing Campaign Spreads Via LinkedIn Comments

A widespread phishing campaign is targeting LinkedIn users by posting comments on users’ posts, BleepingComputer reports. Threat actors are …
AI Literacy Training: From Best Practice to Legal Requirement Under the New EU AI Act

For those of you who are like me, when I first heard about the new EU AI Act, I had flashbacks to the implementation of the General Data …
The Skeleton Key: How Attackers Weaponize Trusted RMM Tools for Backdoor Access

Lead Analysts: Jeewan Singh Jalal, Prabhakaran Ravichandhiran and Anand Bodke KnowBe4 Threat Labs recently examined a sophisticated …
Preventing Data Breaches Before They Happen: Why Outbound Email Security Can't Be Ignored

While organizations invest heavily in stopping threats from entering their networks, a critical vulnerability often goes underprotected: …
AI-Assisted Social Engineering is a Growing Concern

A survey by the World Economic Forum (WEF) found that 47% of organizations cite the advancement of adversarial capabilities as their top …
Report: Scammers Stole $17 Billion Worth of Crypto Last Year

Scammers stole an estimated $17 billion worth of cryptocurrency in 2025, according to a new report from Chainalysis. Notably, the report …
Threat Actors Exploit Misconfigurations to Spoof Internal Emails

Attackers are increasingly abusing network misconfigurations to send spoofed phishing emails, according to researchers at Microsoft. This …
Report: Microsoft Was the Most Impersonated Brand in Q4 2025

Microsoft was the most commonly impersonated brand in phishing attacks during the fourth quarter of 2025, according to researchers at Guardio.…
Phishing Campaign Abuses Google’s Infrastructure to Bypass Defenses

Researchers at RavenMail warn that a major phishing campaign targeted more than 3,000 organizations last month, primarily in the manufacturing…
AI Deepfakes Are Impersonating Religious Figures to Solicit Donations

WIRED reports that deepfake attacks are impersonating pastors and other religious figures in order to scam congregations.
Your KnowBe4 Fresh Compliance Plus Content Updates from December 2025
-1.png)
“Gave me good things to consider that I had not thought about as we move forward and AI becomes a part of our work processes!” …
ConsentFix Attacks Fake Cloudflare Prompts

ClickFix attacks have been around for decades; only the name is new. ClickFix attacks use social engineering to trick users into clicking on …
Your KnowBe4 Fresh Content Updates from December 2025
.png)
“It was really good. I liked that it covered a lot of important subjects, focused on how to spot red flags, and used an AI deepfake …
Phishing Campaign Targets WhatsApp Accounts

Researchers at Gen warn that a phishing campaign is attempting to trick users into linking malicious devices to their WhatsApp accounts.
Defending Against Modern Email Threats With Layered, AI-Driven Security

Email has been the backbone of business communication for decades and as such, it remains the attacker’s favorite doorway into an organization.
North Korean Threat Actor Spreads Malware via QR Codes

The North Korean threat actor “Kimsuky” is using QR codes to trick users into installing malicious mobile apps, according to security …
When Seeing Isn’t Believing: AI Images, Breaking News and the New Misinformation Playbook

In the early hours following reports of a U.S. military operation involving Venezuela, social media feeds were flooded with dramatic images …
Amazon Warns of Fraudulent North Korean Job Applicants

Amazon has blocked more than 1,800 suspected North Korean applicants from joining the company since April 2024, TechRadar reports. Amazon’s …
New ConsentFix Technique Tricks Users Into Handing Over OAuth Tokens

Researchers at Push Security have observed a new variant of the ClickFix attack that combines “OAuth consent phishing with a ClickFix-style …
Most Parked Domains Lead Users to Scams or Malware

Over 90% of parked domains now direct users to malicious content, compared to less than 5% a decade ago, according to researchers at Infoblox.
New BlackForce Phishing Kit Bypasses Multifactor Authentication

Zscaler has published a report on a new phishing kit dubbed “BlackForce” that uses Man-in-the-Browser (MitB) attacks to steal credentials and …
81% of Small Businesses Sustained a Cyber Incident Over the Past Year

Eighty-one percent of small businesses suffered a security or data breach over the past year, and 38% of these businesses were forced to raise…
Be Careful of That Warrant for Your Arrest

A popular phone call/voicemail scam (i.e., vishing) involves someone calling you, claiming to be law enforcement with a warrant for your …
Unmasking the Deepfake Threat: A Game-Changer for Reducing Human Risk

Today, anyone can find a picture of absolutely anybody and it is also not difficult to find a sample of their voice. By combining these it is …
WeChat Phishing Attacks a Growing Threat Outside China

Lead analysts: Cameron Sweeney, Lucy Gee, Louis Tiley, James Dyer “Super-app” WeChat offers a wealth of functionality—from instant messaging, …
Mexico Unveils Its First National Cybersecurity Plan: A New Era of Digital Resilience

Mexico has taken a major step toward strengthening its digital defenses with the official unveiling of its first National Cybersecurity Plan, …
Phishing Campaign Targets Executives With Phony Awards

A phishing campaign is targeting executives with phony offers for awards, according to researchers at Trustwave SpiderLabs. The attackers …
Warning: Phishing Attacks Abuse Free Cloudflare Pages

Malwarebytes warns that threat actors are abusing the free Cloudflare Pages service to host phishing portals, helping the phishing sites avoid…
Your KnowBe4 Compliance Plus Fresh Content Updates from November 2025
-1.png)
"Good information. Everyone who owns a computer should do this training across the country. It should be mandatory!” "Wow, I had no …
Deepfake Training: A Strategic Advantage Against Emerging Threats

Deepfake attacks have become more compelling and realistic than ever before.
North Korean Job Invitation

A friend of mine, John D., received this outreach on Threads (see below). At first, he thought it was the standard fake employer scam, but it …
Fresh Content Updates from November 2025
.png)
"Good information. Everyone who owns a computer should do this training across the country. It should be mandatory!” "Wow, I had no …
Social Engineering Campaign Targets Microsoft Teams Users
.jpg)
Researchers at CyberProof warn that threat actors are launching phishing attacks via Microsoft Teams' “Chat with Anyone” feature, which lets …
Report: Phishing Has Surged 400% Year-Over-Year

Researchers at SpyCloud have observed a 400% year-over-year increase in successful phishing attacks, with a disproportionate number of attacks…
Warning: Phishing Campaign Leveraging Evilginx Targets U.S. Universities

Threat actors are using the open-source phishing framework Evilginx to target universities across the United States, according to researchers …
Notorious Cybercrime Group is Now Targeting Zendesk Users

ReliaQuest warns that the cybercriminal collective “Scattered Lapsus$ Hunters” appears to be using social engineering attacks to target …
Malicious AI Tools Assist in Phishing and Ransomware Attacks

Researchers at Palo Alto Networks’ Unit 42 are tracking two new malicious AI tools, WormGPT 4 and KawaiiGPT, that allow threat actors to craft…
KnowBe4 Earns Multiple 2026 Buyer's Choice Awards from TrustRadius

KnowBe4 is proud to announce that three of its leading security products — Security Awareness Training, PhishER/PhishER Plus and Compliance …
Report: Sophisticated Fraud Attacks Are on the Rise

Sophisticated online fraud techniques are growing more accessible to unskilled attackers, driven by AI tools and fraud-as-a-service platforms,…
The Ghost in the Machine: How a Multi-Stage Phishing Campaign Evades Security to Steal Microsoft 365 Credentials

Lead Analysts: Jeewan Singh Jalal, Prabhakaran Ravichandhiran and Anand Bodke Since November 3, 2025, KnowBe4 Threat Labs has been monitoring …
New Criminal Toolkit Abuses Browser Push Notifications

A new criminal platform called “Matrix Push C2” is using browser notifications to launch social engineering attacks, according to researchers …
KnowBe4 Is a Leader In the Gartner® Magic Quadrant™ for Email Security For the Second Consecutive Year
.png)
Following its launch in 2024, Gartner® has now published the second Magic Quadrant™ for Email Security —and KnowBe4 is delighted to once again…
Scammers Are Exploiting the Holiday Shopping Season

Users should be particularly wary of holiday-themed scams over the next few weeks, according to researchers at Malwarebytes. “Mobile-first …
Phishing Campaign Uses Fake Party Invites to Deliver Remote Access Tools

A large phishing campaign is using phony seasonal party invites to trick users into installing remote management and monitoring (RMM) tools, …
One-Size-Fits-All Security Training Fits Nobody

Here's a curious thing about people, sometimes we crave the familiar, and sometimes we demand the novel.
Blurred Chats, Bigger Risks

Think about your digital spaces. You’ve got your corporate email, which we all treat a bit like a high-security bank vault. We approach it …
EMEA Finance and Banking: A Sector Under Siege
.jpg)
The finance and banking sector across Europe, the Middle East, and Africa (EMEA) faces extraordinary cybersecurity challenges, according to …
UK’s New Cyber Security and Resilience Bill: What Does It Mean For Critical Infrastructure Organisations?

In recent weeks, the UK government has announced the introduction of its new Cyber Security and Resilience Bill.
What Happens When Cybercriminals Compromise a Sportswear Giant?

Lead analysts: Louis Tiley, Lucy Gee and James Dyer Between 1:48pm ET on October 29 and 6:53pm ET on October 30, 2025, KnowBe4 threat analysts…
Report: Deepfake Attacks Are on the Rise

A new report from Entrust warns of an increase in deepfake attacks, which now account for one in five biometric fraud attempts. Additionally, …
Be Prepared: Mobile Phishing Expected to Surge Fourfold During the Holiday Season

Users and organizations should be prepared for a surge in phishing attacks over the next several weeks, as attackers take advantage of the …
Report: Ransomware Attacks Surged Globally in October

Ransomware attacks spiked in October 2025, with more than 700 organizations sustaining attacks, according to a new report from Cyfirma.
How KnowBe4 Uses AI Efficiently to Get the Best Results

Using the right tool for the job is always better. Anyone who does DIY projects around the home knows how using the right tool can …
Warning: New Phishing Kit Targets Italian Entities

A new phishing kit is impersonating the Italian IT and web services provider Aruba, according to researchers at Group-IB. The kit is designed …
New Android Malware Platform Targets Bank Accounts

Researchers at Zimperium are tracking a new malware-as-a-service platform designed to target Android phones with banking Trojans. The …
2025 Cybersecurity Awareness Month by the Numbers

Organizations rely on KnowBe4 to educate millions of people each month on security awareness and compliance topics, and every October, during …
Your KnowBe4 Compliance Plus Fresh Content Updates from October 2025
.png)
We’re thrilled to announce KnowBe4 Studios, uniting our world-class creative teams under one powerful brand for our Compliance Plus library. …
Tycoon 2FA Phishing Kit Grows More Sophisticated

Cybereason warns that the Tycoon 2FA phishing kit continues to receive upgrades, allowing unskilled cybercriminals to launch sophisticated …
Warning: ClickFix Attacks are Growing More Sophisticated

Researchers at Push Security warn of an extremely convincing ClickFix attack posing as a Cloudflare verification check. ClickFix is a social …
Quantum Route Redirect: Anonymous Tool Streamlining Global Phishing Attack

Lead Analysts: Jeewan Singh Jalal, Prabhakaran Ravichandhiran and Anand Bodke KnowBe4 Threat Labs has uncovered an emerging advanced phishing …
Africa is Being Targeted by a Surge in AI-Fueled Phishing Attacks

AI-fueled cyberattacks are increasingly targeting entities across Africa, according to Robert Lemos at Dark Reading. Lemos cites two recent …
Warning: Malicious Apps Are Impersonating AI Tools

Researchers at Appknox warn that malicious apps are impersonating popular AI tools like ChatGPT and DALL-E to trick users into installing …
Phishing Emails Use Invisible Hyphens to Avoid Detection

A phishing campaign is using invisible characters to evade security filters, according to Jan Kopriva at the SANS Internet Storm Center.
Introducing KnowBe4 Studios | Fresh Content Updates from October 2025
.png)
We’re thrilled to announce KnowBe4 Studios, uniting our world-class creative teams under one powerful brand. Leveraging the latest AI …
Microsoft Help Desk Phishing Attempt

I received this email the other day to my personal email account. It is a “Security Alert” from “Microsoft Helpdesk.” Oh, my!
LastPass Phishing Campaign Informs Users of Phony Death Notifications

A phishing campaign is targeting LastPass users with phony notifications informing users that someone has notified the company of the user’s …
New Study Warns of AI-Driven Extortion Attacks
.jpg)
A study from Malwarebytes has found that one in three mobile users has been targeted by an extortion scam, and one in five of these users has …
Human Error is Still a Top Contributor to Cyberattacks

Human error remains the primary exploitation vector in mobile security incidents, according to Verizon’s latest Mobile Security Index (MSI).
The Rapid Advancement of Malicious AI Is Changing Cyberdefense Forevermore

AI maturation is leading to more malicious hacking attacks.
Report: AI Poisoning Attacks Are Easier Than Previously Thought
.jpg)
Attackers can more easily introduce malicious data into AI models than previously thought, according to a new study from Antropic. Poisoned AI…
UN Convention Against Cybercrime Is a Huge Win!

One of the biggest reasons why cybercrime is so bad — and is increasing each year —is that so much of it is committed by foreign nationals who…
When a “Contact Us” Form Becomes “Contact a Cybercriminal”

Lead Analysts: Lucy Gee and James Dyer Cybercriminals want their payday. Unfortunately for the targets of phishing (and the organizations they…
Report: Organizations Are Struggling to Keep Up With AI-Powered Attacks

76% of organizations are struggling to keep up with the sophistication of AI-powered attacks, according to CrowdStrike’s latest State of …
Insider Risk, Ethical Walls and the Future of Data Governance in Financial Services

In the complex ecosystem of financial services, some of the greatest threats come from within. While cybersecurity for financial institutions …
The Human-AI Partnership: Securing the New Dual-Front of Business Risk

The integration of artificial intelligence into the modern workplace represents a paradigm shift in productivity and innovation.
Is It Or Is It Not an HP Scam?

These days it can be hard to tell if something is or isn’t a scam.
Report: More Than Half of Adults Encountered a Scam Last Year
.jpg)
Researchers at Bitdefender warn that scams are seeing a steady increase globally. Citing a recent report from the Global Anti-Scam Alliance …
[Cyber Security Awareness Month] Doppelgänger Promotes Incident Hiding: Why Saying Something When You See Something Is So Important
.png)
It can happen to the best of us. This story happened a decade ago, when I was working at a Fortune 10 company. “Smartest” is subjective, but …
Minimizing liability is not the same as security: Lessons from Recent Airport Cyber Disruptions
.jpg)
In late September 2025, several European airports reported significant delays and flight cancellations due to disruptions with their check-in …
Phishing Campaign Impersonates Google Careers Recruiters

A phishing campaign is impersonating Google Careers to target job seekers, according to researchers at Sublime Security.
Phishing Campaign Impersonates Password Managers

A phishing campaign is impersonating LastPass and Bitwarden with phony breach notifications, BleepingComputer reports.
Minimizing liability is not the same as security: Lessons learned from Collin's Aerospace cyberattack
.jpg)
In late September 2025, several European airports reported significant delays and flight cancellations due to issues with their check-in and …
Attackers Abuse Grok to Spread Phishing Links

Threat actors are abusing X’s generative AI bot Grok to spread phishing links, according to researchers at ESET. The attackers achieve this by…
Building Trust in the Digital Age: How Financial Services Can Balance Security and Speed

In the high-stakes world of financial services, trust is the cornerstone of every client relationship. But here's the challenge that keeps …
Alert: Watch Out For Phishing Attacks in the Wake of the AWS Outage
.jpg)
Cybernews warns that threat actors will likely take advantage of the recent AWS outage to launch phishing attacks against affected users.
Half of Young People in the UK Cite Non-Consensual Deepfakes as a Top Fear

A new survey found that 50% of UK residents aged 16 to 34 cite deepfake nudes as their top worry related to AI technology, SecurityBrief …
[Cybersecurity Awareness Month]: Keeping Enkryptor at Bay: How We All Can Help Beat Back Ransomware

Ransomware is the gift that keeps on giving… and taking.
Phishing Remains the Top Initial Access Vector in Cyberattacks Across Europe
.jpg)
Phishing was the initial access vector for 60% of cyberattacks across Europe between July 2024 and June 2025, according to the European Union …
We Need to Teach Our AIs to Securely Code

I have been writing about the need to better train our programmers in secure coding practices for decades, most recently here and here.
Protect Yourself From Voice Phishing Attacks Targeting Salesforce Instances

Google’s Mandiant has published guidance on defending against an ongoing wave of social engineering attacks targeting organizations’ …
The Compliance Catch-22: How Financial Institutions Can Master Data Governance and Regulatory Risk

The financial services industry operates in one of the most heavily regulated environments in the business world. With sensitive client data …
A Surge in Text Message Scams Targets Younger Americans

A new report warns of a significant spike in SMS phishing (smishing) scams targeting younger Americans between 18 and 29 years old.
Warning: Job Scams Surge by More than 1000%

Job-related scams surged by more than one thousand percent between May and July 2025, according to new research from McAfee.
[Cybersecurity Awareness Month] The Rise of Dr. Deepfake: Combatting Social Engineering’s Newest Weapon

Deepfakes are easier to create than ever and are being used to attack organizations, families and individuals.
The Engine Room: Powering Your Human Risk Management Strategy with Intelligent Tech

We’ve come a long way. We’ve deconstructed the problem, explored the complexity of humans, and laid out a strategic framework and a practical …
Report: North Korea Expands Its Remote Employment Schemes

North Korea’s fraudulent IT worker schemes have expanded to target nearly every industry that hires remote employees, according to researchers…
The Hidden Cybersecurity Threat: Securing the Human-AI Relationship

The conversation about AI in cybersecurity is missing the point. While the industry has been focused on the emergence of AI-generated phishing…
A TikTok for Deepfakes? OpenAI Could Be Making It a Reality

OpenAI, the people behind ChatGPT, have launched an updated AI video- and audio-generation system with fascinating, and terrifying, …
Multitasking Employees Are Particularly Vulnerable to Phishing Attacks
.jpg)
Employees who multitask are significantly more vulnerable to phishing attacks, according to a study from the University at Albany published in…
If You Have Not Realized It, Vishing Is Really Taking Off

Fighting voice-based phishing needs to be a big part of your human risk management (HRM) plan.
Securing the Human-AI Boundary: Why the Future of Cybersecurity Must Train People and AI Agents

The cybersecurity landscape is undergoing its most dramatic transformation since the dawn of the internet.
Cyber Risk Still #1: Why AI Is Raising the Stakes - and the Opportunities
.jpg)
If you’re wondering what keeps business leaders up at night, the latest Aon Global Risk Management Survey has a clear answer: cyber attacks …
New Phishing Campaign Uses AI Tools to Evade Detection

Microsoft warns that a recent phishing campaign used AI technology to obfuscate its payload and evade security filters.
Security Leaders Cite AI-Driven Phishing Attacks as a Top Concern

A new report has found that nearly 40% of security leaders believe their organizations are least prepared for phishing and other social …
[Cybersecurity Awareness Month] Watch Out for the Cyberpunks: Outsmarting Social Engineering in Retro Arcade Style

October marks Cybersecurity Awareness Month, a perfect reminder that while technology evolves, the greatest threat to organizations often …
Your KnowBe4 Compliance Plus Fresh Content Updates from September 2025
Check out the September updates in Compliance Plus so you can stay on top of featured compliance training content.
The DEEP Matrix: Your Map to a Unified Defense

Welcome back. We have our DEEP framework which was explored in the previous blog post, and discussed in depth in our most recent human risk …
North Korean Hackers Target Job Seekers With Social Engineering Tricks

A North Korean threat actor dubbed “DeceptiveDevelopment” is using various social engineering techniques to target job seekers, according to …
Report: Deepfake Attacks Have Targeted Nearly Two-Thirds of Organizations

A survey by Gartner found that 62% of organizations have been hit by a deepfake attack in the past twelve months, Infosecurity Magazine …
Your KnowBe4 Fresh Content Updates from September 2025
.png)
Check out the 44 new pieces of training content added in September, alongside the always fresh content update highlights, new features and …
Why KB4-CON EMEA 2025 Should Be Your Must-Attend Cybersecurity Conference This October

As cyber threats continue to evolve at breakneck speed, staying ahead of the curve isn't just important, it's essential.
Building Trust in AI: KnowBe4's Journey Toward ISO 42001 Certification

At KnowBe4, everything we do is built on a foundation of innovation and trust. As we bring more artificial intelligence (AI) into our human …
Get Your Game On! 3 Ways to Use the 2025 Cybersecurity Awareness Month Resource Kit

The calendar has flipped into October, so now it’s time to let the Cybersecurity Awareness Month games begin!
Going DEEP: A Simple Framework for a Complex Problem

In our previous blog post, we discussed the behavioral science behind why people click on malicious links.
The 3 Biggest Email Security Challenges Facing Legal Organizations

Law firms really are under constant pressure to meet tight deadlines, maintain client confidentiality and protect privileged communications.
The Behavioral Science Behind the Click

Welcome back. In our last blog post, we talked about the great divide between tech-focused and people-focused security.
New AI-Driven Phishing Platform Automates Attack Campaigns

Researchers at Varonis warn of a new phishing automation platform called “SpamGPT” that “combines the power of generative AI with a full suite…
Attackers Use AI Development Tools to Craft Phony CAPTCHA Pages
Attackers are abusing AI-powered development platforms like Lovable, Netlify and Vercel to create and host captcha challenge websites as part …
Attackers Abuse Google’s AppSheet to Send Phishing Emails
Hackread reports that attackers are abusing Google’s AppSheet platform to send phishing emails.
Why Your Security Strategy Needs a Human Upgrade

Let’s be brutally honest. For years, our industry has been locked in a civil war. In one camp, the technologists have been building higher …
North Korean Hackers Target Job Seekers With ClickFix Attacks
.jpg)
North Korean hackers behind the “Contagious Interview” campaign are using the ClickFix social engineering tactic to target job seekers with …
AI-Assisted Phishing Attacks Are an Increasingly Serious Threat

AI-assisted phishing attacks pose a significant and increasing threat to organizations, according to Matt Weidman, partner and vice president…
Protecting AI Agents Will Be Status Quo

Protecting humans means protecting the tools humans use.
Report: AI-Powered Phishing Fuels Ransomware Losses

AI-powered social engineering attacks are significantly more successful than traditional attacks, according to a new report from cyber risk …
Phishing Campaign Abuses iCloud Calendar Invites

Attackers are abusing iCloud Calendar invites to send phishing messages that pose as PayPal notifications, BleepingComputer reports. Since the…
FBI Issues Guidance for Avoiding Deepfake Scams

The FBI and the American Bankers Association (ABA) have issued a joint advisory warning of the growing threat posed by AI-generated deepfake …
PayPal Scam From PayPal

One of the most common human risk management recommendations is for users to hover over URL links of unexpected messages to see if the …
Report: Shadow AI Poses an Increasing Risk to Organizations

The use of “shadow AI” is an increasing security risk within organizations, according to a new report from Netskope.
"Yep, I got pwned. Sorry everyone, very embarrassing."
.jpg)
In essence, that is the disclosure and notification message that the open-source developer "qix" sent to the world when he was social …
Smishing Campaign Targets California Taxpayers With Phony Refund Offers

The State of California’s Franchise Tax Board (FTB) has warned of an ongoing SMS phishing (smishing) campaign targeting residents, …
Advanced Educational Competition – Ask Your Employees To Submit Their Best Phishing

I occasionally get human risk management (HRM) administrators asking me to help them with ideas of “contests” to better educate their …
Warning: New Spear Phishing Campaign Targets Executives

Researchers at Stripe warn of a wave of spear phishing attacks targeting C-suite employees and senior leadership across a wide range of …
Hospitals Need to Prepare for AI-Powered Phishing Attacks

Healthcare organizations need to be prepared for an increase in AI-assisted phishing attacks, according to Zack Martin, Senior Policy Advisor …
A Warrant Is Out for Your Arrest

A super common voice phone call phishing scam (i.e., vishing) is when the scammer calls you and pretends to be a law enforcement official with…
Report: AI Can Now Automate Entire Attack Chains

Threat actors can now use AI tools to automate entire attack operations, according to a new report from Anthropic.
Beyond the Audit Box: Building Security That Works in the Real World

Many years ago, a friend of mine worked as a security director at a firm and had what they called an “audit box.” It was a pre-prepared box …
Your KnowBe4 Compliance Plus Fresh Content Updates from August 2025

Check out the August updates in Compliance Plus so you can stay on top of featured compliance training content.
One of the Biggest Mysteries in Cybersecurity: Why Don’t We Teach or Demand Secure

“The problem is much, much worse than most people acknowledge.” One of the biggest enduring mysteries for me in cybersecurity is why most …
Your KnowBe4 Fresh Content Updates from August 2025

Check out the 19 new pieces of training content added in August, alongside the always fresh content update highlights, new features and events.
New Phishing Kit Bypasses MFA to Steal Microsoft 365 Credentials

Attackers are using a newly discovered phishing-as-a-service (PhaaS) platform dubbed “Salty 2FA” to target a wide range of industries across …
Report: Cybercriminals are Hiring Social Engineering Talent

ReliaQuest has published a report on the cybercriminal recruitment ecosystem, finding that fluent English speakers with social engineering …
Back to School: Cybersecurity Education for All Ages

It’s that exhilarating time of year again! Summer is winding down, and the back-to-school season is in full swing—a truly fantastic time to …
Threat Actors Are Increasingly Abusing Generative AI Tools for Phishing

Cybercriminals are increasingly abusing AI-assisted website generators to quickly craft convincing phishing sites, according to researchers at…
The Technical Sophistication Behind the "Free" Gift Scam: Evading Detection

Below is an example of a sophisticated survey scam phishing email that KnowBe4’s Threat Lab team has been monitoring as discussed in “The …
The Hidden Cost of "Free" Gifts: How Survey Scams Are Evolving to Steal Financial Data

You've probably seen them: enticing online offers for free products from brands you trust, like a Yeti beach chair from Costco or an emergency…
Phishing Attacks Target Brokerage Accounts to Manipulate Stock Prices

Professional phishing groups are targeting customers of brokerage firms in order to manipulate stock prices, KrebsOnSecurity reports. The …
New Homoglyph Phishing Campaign Impersonates Booking.com

Attackers are using a Japanese Unicode character to replace forward slashes in phishing URLs, BleepingComputer reports.
Warning: Social Engineering is a Growing Threat to the Industrial Sector

Social engineering attacks are a growing threat to operational technology (OT) environments, Industrial Cyber reports.
The Attacker’s Playbook: A Technical Analysis of Quishing and Encrypted SVG Payloads Used in HR Impersonation Phishing Attacks

In this series, we first explored the psychology that makes HR phishing so effective, then showcased the real-world lures attackers use to …
That ‘Urgent Payroll Update’ Email is a Trap: A Look at the Latest HR Phishing Tactics
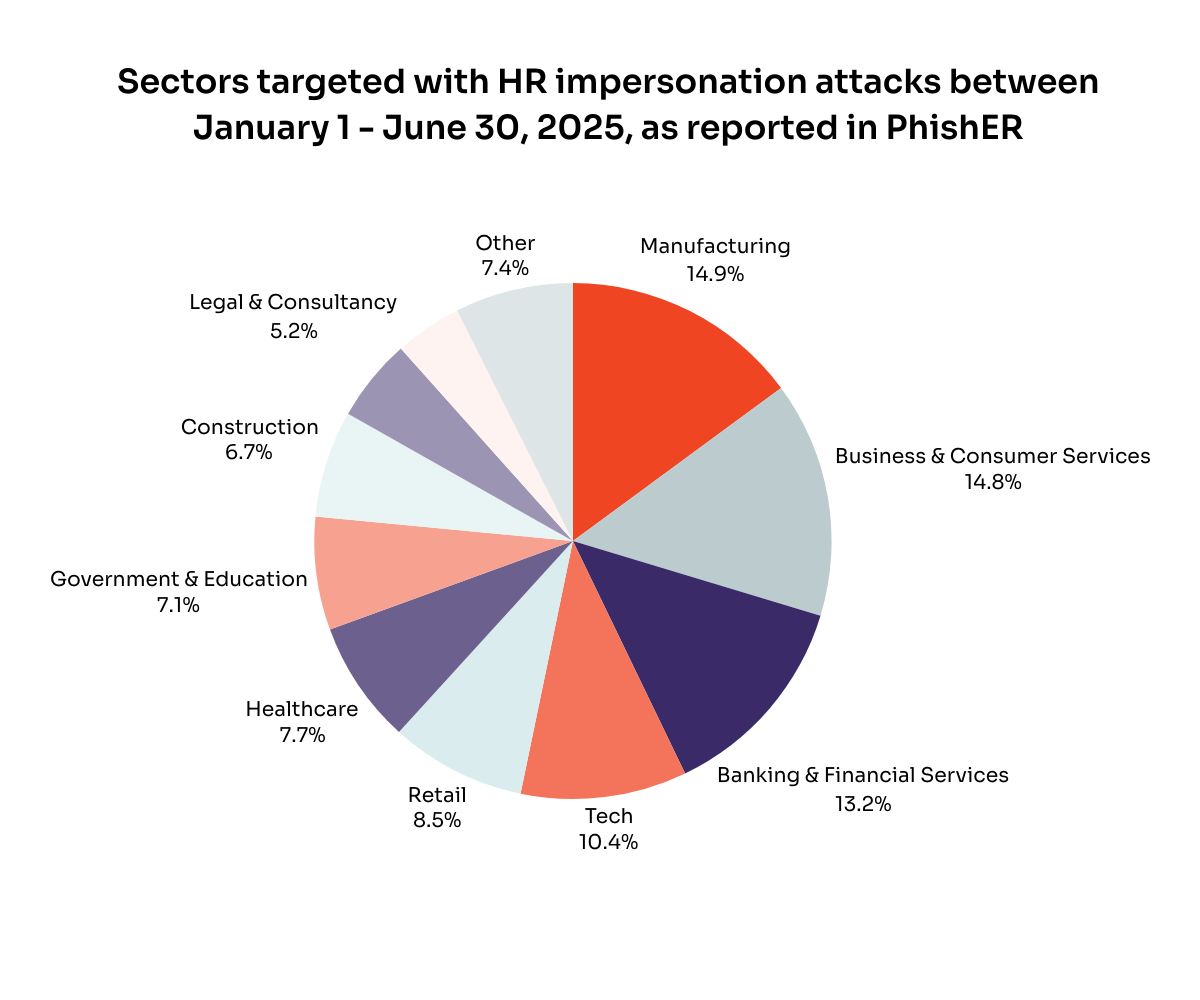
Phishing attacks impersonating HR are on the rise. Between January 1 – March 31, 2025, our Threat Lab team observed an 120%surge in these …
From Human Resources to Human Risk: Why HR is the Perfect Department for Cybercriminals to Impersonate

We all trust HR - or at least we do when we think they’re emailing us! Data from KnowBe4’s HRM+ platform reveals that phishing simulations …
North Korean Threat Actor Delivers Ransomware Via Phishing Emails

The North Korean threat actor ScarCruft has incorporated ransomware into its arsenal, according to researchers at South Korean security firm …
How KnowBe4 Defend Seamlessly Integrates with Microsoft Defender for Office 365 Quarantine—And Why SOC Teams Should Care

Modern Security Operations Centers (SOCs) face a persistent challenge: managing threats across multiple security tools while maintaining operational…
[FREE RESOURCE KIT] Cybersecurity Awareness Month Kit 2025 Now Available

In the never-ending battle against cyber villains, your users are on the front lines.
A Practical Guide to the European Union’s Cybersecurity Funding for SMEs

For any small- to medium-sized enterprise (SME), the cybersecurity landscape can be intimidating. You are informed of a variety of threats, …
Celebrating KnowBe4's 6th Consecutive TrustRadius Tech Cares Award

For the sixth year in a row, we've been honored with the TrustRadius Tech Cares Award!
Beyond the Inbox: How Old-School Mail Scams Are Still Stealing Your Money

In a world so full of digital online scams, it’s hard to remember that scammers abuse our postal mailing systems as well.
Alert: Tech Support Scammers Send Phony Podcast Invites

The Better Business Bureau (BBB) has warned that scammers are targeting high-profile employees and influencers with fake invitations to appear…
Honoring KnowBe4’s 15 Years of Excellence with a New Brand Identity

As I reflect on KnowBe4's incredible journey, I'm filled with both pride for how far we've come and excitement for what’s ahead.
Your KnowBe4 Fresh Content Updates from July 2025

Check out the 36 new pieces of training content added in July, alongside the always fresh content update highlights, new features and events.
Your KnowBe4 Compliance Plus Fresh Content Updates from July 2025

Check out the July updates in Compliance Plus so you can stay on top of featured compliance training content.
FBI Report: Attackers Are Sending Physical Packages with Malicious QR Codes

The FBI has issued an advisory warning that scammers are distributing QR code phishing (quishing) links via unsolicited packages sent by snail…
Anatomy of a Vishing Scam
I hear about a ton of similar-sounding scam calls, where the scammer is pretending to be from a service you use (or used), offering you a …
Social Engineering Attacks Surged in the First Half of 2025

Cybersecurity incidents nearly tripled in the first half of 2025, jumping from 6% in the second half of 2024 to 17% in 2025, according to a …
Beyond Traditional Defenses: Why French Cyber Resilience Needs to Improve

In today's world, cyberattacks are a constant threat. While technical defenses are crucial, people often remain the easiest attack vector for …
Warning: New Phishing Campaign Targets Instagram Users

A phishing campaign is targeting Instagram users with phony notifications about failed login attempts, according to researchers at …
ClickFix Social Engineering is Becoming More Popular

ClickFix attacks have been around for decades; only the name is new.
How Hackers Exploit Microsoft Teams in Social Engineering Attacks

Attackers are using Microsoft Teams calls to trick users into installing the Matanbuchus malware loader, which frequently precedes ransomware …
If You Think Social Engineering Is Bad, It’s Going To Get Worse

There is no other way to say it clearer, social engineering is going to be a lot, lot worse soon and far more successful than it is today. And…
FBI Issues Guidance on Thwarting North Korea’s Fraudulent IT Schemes

The FBI has issued an advisory warning that North Korean IT workers continue to seek fraudulent employment at Western companies.
Malicious Connectors Potentially Impact Hundreds of Millions of Microsoft 365 Users

Most Microsoft 365 users aren’t aware of this recently growing serious email threat vector.
[CASE STUDY] Retail Organization Sees 50-Fold Increase in Phishing Reporting with KnowBe4's Phish Alert Button and Training

A global retail and wholesale company transformed their security posture after implementing KnowBe4's Phish Alert Button (PAB) and security …
Boost Your Browsing Security: Integrate SecurityCoach with Microsoft Edge for Business

Managing the security gap between your technical defenses and user behavior just got easier!
KnowBe4 Named a 2025 Gartner Peer Insights™ Customers’ Choice for Email Security Platforms

KnowBe4 is excited to announce that we have been recognized as an overall Customers’ Choice in the July 2025 Gartner Peer Insights Voice of …
[New Whitepaper] Best Security Practices for AI Prompting and Building Agent Systems

Bob Fabien wrote on X: "While some are still paying over a grand for AI courses, the biggest players are giving away high-value resources at …
Warning: Ransomware Attacks Surged by 63% Last Quarter

Ransomware attacks increased by 63% year-over-year in the second quarter of 2025, with a total of 276 publicly disclosed incidents, according …
Bridging the Gap: Human Risk in African Cybersecurity

Africa's cybersecurity landscape presents a paradox: a widespread belief in preparedness among organisations, although significant blind spots…
New APIsec University Training Modules Now Available in KnowBe4’s Diamond Library

We’re excited to announce the addition of six new training modules from APIsec University, now available at the Diamond Level in KnowBe4’s …
Ransomware Trends in 2025

I’ve been following ransomware since the first one, the AIDS Cop Trojan, was released in December 1989.
Job Seekers Beware: Many People Are Falling for Employment Scams

More than one in ten people who were targeted by job scams this year fell victim, according to a report from Resume.org.
Thousands of Spoofed News Sites Are Pushing Push Investment Fraud Scams

Scammers are using over 17,000 phony news sites to push investment fraud, according to a new report from CTM360.
FTC Advisory: How to Protect Yourself Against Job Scams

The US Federal Trade Commission (FTC) has issued an advisory warning of job scams that impersonate well-known companies with tempting …
The Attack On Browser-Based AI Agents Is Coming

We are working tirelessly on our AI First strategy to better protect both humans and their AI tools.
Digital Factories, Digital Dangers: Why Manufacturing is a Prime Target for Cyberattacks

Digital connectivity is reshaping European manufacturing, driving both efficiency and innovation.
Engineered To Evade: How Phishing Attacks Are Designed To Get Through Your Secure Email Gateway

Getting through secure email gateways (SEGs) is simply the cost of doing business for a cybercriminal. Literally, detection at the perimeter …
AI-Generated Summaries Mistakenly Suggest Phishing Sites

Researchers at Netcraft warn that AI-generated search engine summaries are suggesting phishing sites when users ask them to find legitimate …
Alert: Scattered Spider is Targeting the Aviation Sector

The US FBI and cybersecurity experts are warning that the Scattered Spider extortion gang has shifted its focus to the aviation and …
AI Attacks Are Coming in a Big Way Now!

AI is going to allow better, faster, and more pervasive attacks.
Psychological Contract Breach and the Power of Security Culture - Research Insights

Employees are expected to behave securely, and the definition of “securely” is often written down in a myriad of security policies. Yet, …
What Makes Southeast Asia the “Ground Zero of Cybercrime”?

Author: Bex Bailey Our 2025 Phishing By Industry Benchmarking Report examines why organizations across Asia face some of the highest levels of…
Is your Human Risk Management Program Creating Measurable Change? Find Out with Our Free Program Maturity Assessment

In today's threat landscape, your employees represent both your greatest vulnerability and your strongest defense.
Your KnowBe4 Compliance Plus Fresh Content Updates from June 2025

Check out the June updates in Compliance Plus so you can stay on top of featured compliance training content.
US Tech Executives Cite Cyberattacks as Their Top Concern

A new survey has found that 64% of C-Suite executives in cybersecurity or data center roles view data breaches and ransomware attacks as the …
Your KnowBe4 Fresh Content Updates from June 2025

Check out the 33 new pieces of training content added in June, alongside the always fresh content update highlights, new features and events.
Warning: Scammers are Targeting WhatsApp Users

Researchers at Bitdefender warn of a wave of social engineering attacks targeting WhatsApp accounts.
What Is Human Risk Management?

Cybersecurity has long focused on fortifying networks, securing endpoints and blocking malicious code.
Europol Warns of Social Engineering Attacks

Social engineering remains a primary initial access vector for cybercriminals, according to a new report from Europol.
A Clicking Time Bomb: What To Do About Repeat Clickers

I recently had several conversations about repeat clickers. First with a Forrester analyst and then, shortly after, at KB4-CON Orlando …
FTC States That Scams Cost U.S. Consumers $158.3 Billion in One Year

I am used to repeating some pretty big numbers when talking about the financial impact of cybercrimes. When you look into the data, it is …
Happy 2nd Birthday to Our KnowBe4 Community!

Can it be? Is it true? Two years of KnowBe4 Community!
Warning: Voice Deepfakes Continue to Improve

AI-generated voice deepfakes present an urgent threat to organizations, according to researchers at Pindrop.
Phishing Deep Dive: EU-Affiliated Survey Platform Exploited in Sophisticated Credential Harvesting Campaign

Lead Researchers: James Dyer and Louis Tiley Between May 5 and May 7, 2025, KnowBe4 Threat Lab identified a phishing campaign originating from…
KnowBe4 Collaborates with Microsoft: Strengthening Email Security Through Strategic Integration

In today's rapidly evolving threat landscape, cybercriminals are becoming increasingly sophisticated in their attack methodologies, …
Protect Yourself: Vishing Attacks Are Growing More Sophisticated

Researchers at Google’s Mandiant have published a report on voice phishing (vishing) attacks, noting that these attacks have served as initial…
Google Report Outlines the Latest Scam Trends

Researchers at Google have published a report on the latest scam trends, noting an increase in travel-themed scams targeting people preparing …
Checkups and Checklists: Cyber Risk Isn’t Just a Technical Problem

There are many things in our lives we must prepare for to be ready. For other things, we wing it, or we're not prepared to deal with it at the…
What Is AI?

What is AI really? Throughout this article, I will remove the hype and get to the most honest answer ever.
How to Recognize Fraudulent North Korean Job Applicants

Researchers at Socure warn of an ongoing wave of employment fraud driven by North Korean IT operatives attempting to secure positions at …
How a Fake Cybersecurity Firm Became a Real Threat

Picture this: it's 2021. You're an IT professional, scrolling through LinkedIn, when a message pings. "Bastion Secure," a new cybersecurity …
Human Risk Management: Cybersecurity as a Business Enabler

Reducing human risk in cybersecurity requires a human-first approach that relies on effective training and practice for people to gain …
OpenAI Report Describes AI-Assisted Social Engineering Attacks

OpenAI has published a report looking at AI-enabled malicious activity, noting that threat actors are increasingly using AI tools to assist in…
KnowBe4 Wins Big with 2025 TrustRadius Top Rated Awards

We’re proud to share that KnowBe4 has once again been recognized as a leader in cybersecurity, receiving multiple 2025 TrustRadius Top Rated …
Spear-Phishing Campaign Targets Financial Executives

Researchers at Trellix warn of a spear-phishing campaign that’s targeting CFOs around the world with phony employment offers.
Warning: Crooks Are Using Vishing Attacks to Compromise Salesforce Instances

A criminal threat actor tracked as “UNC6040” is using voice phishing (vishing) attacks to compromise organizations’ Salesforce instances, …
What Are The Key Components Of A Successful Human Risk Management Program?

When it comes to cybersecurity, organizations face an ever-present and often underestimated threat: human risk.
Fake MFA Reset Warning Message

A KnowBe4 co-worker of mine recently got this SMS phishing message (i.e., smish).
Copyright-Themed Phishing Lures Target Europe

A phishing campaign is targeting European countries with lures themed around copyright infringement, researchers at Cybereason warn.
FBI Alert: Extortion Gang Targets Law Firms With Social Engineering Attacks

The FBI is warning that the Silent Ransom Group (SRG) is targeting law firms with IT-themed social engineering attacks and callback phishing …
The Worsening Landscape of Educational Cybersecurity

Last year, KnowBe4's report "Exponential Growth in Cyber Attacks Against Higher Education Institutions" illustrated the growing cyber threats …
New Unrestricted AI Tool Can Assist in Cybercrime

Researchers at Certo warn that a new AI chatbot called “Venice[.]ai” can allow cybercriminals to easily generate phishing messages or malware …
Your KnowBe4 Compliance Plus Fresh Content Updates from May 2025

Check out the May updates in Compliance Plus so you can stay on top of featured compliance training content.
Beyond Credentials: When Every Data Point Becomes a Weapon

You know what's interesting about data breaches? Everyone focuses on credit card numbers and financial data, but the reality is that every …
French Users Targeted by Major Phishing Campaign

Researchers at IBM Security warn that a major phishing campaign is targeting users in France, incorporating leaked personal data to make the …
Your KnowBe4 Fresh Content Updates from May 2025

Check out the 25 new pieces of training content added in May, alongside the always fresh content update highlights, new features and events.
Scammers Exploit Uncertainty Surrounding US Tariffs

Cybersecurity experts are warning that scammers are taking advantage of uncertainty surrounding the U.S. administration’s tariff policies, …
Capital One Customers Targeted By Credential Harvesting Phishing Campaign

The KnowBe4 Threat Lab has identified an active phishing campaign impersonating Capital One.
Threat Actors Are Using AI-Generated Audio to Impersonate U.S. Officials

The FBI is warning that threat actors are impersonating senior US officials in phishing attacks designed to compromise users’ accounts.
If I Had Only 20 Seconds To Teach People How To Avoid Scams

Human risk management involves more than security awareness training, but training is a huge part of the mix.
The Lost Art of Writing Things Down

I was once enrolled in a programming module back at university. We had been given a task, to code something, so we all sat banging out …
Impersonating Meta, Powered by AppSheet: A Rising Phishing Campaign Exploits Trusted Platforms to Evade Detection

Since March 2025, the KnowBe4 Threat Labs team has observed a surge in phishing attacks that exploit Google’s AppSheet platform to launch a …
The Ransomware Threat: Still Alive and Kicking

Many organizations, after a period of relative quiet, might believe the ransomware bubble has burst. The headlines may have shifted, and other…
Phishing Campaign Targets International Students in the US

The FBI has issued an alert on a wave of phishing attacks targeting Middle Eastern students who are studying in the US.
Beware of Coinbase Scams

I got this Coinbase-related scam in my personal inbox last week.
Warning: Phishing Kits Can Auto-Generate Tailored Login Pages

Commodity phishing kits are increasingly serving dynamically generated phishing pages, according to researchers at ESET.
Agentic AI Ransomware Is On Its Way

Agentic AI-enabled ransomware is not here yet, but likely will be very soon. I am talking this year or by 2026.
Email-based Attacks Accounted for Most Cyber Insurance Claims Last Year

Business email compromise (BEC) attacks and funds transfer fraud (FTF) accounted for 60% of cyber insurance claims in 2024, according to a new…
KnowBe4 Leads the Charge Against Cybersecurity Threats with Unmatched AI Capabilities

When it comes to artificial intelligence (AI) and human risk management (HRM), not all AI is created equal.
How to Protect Your Business from Scattered Spider's Latest Attack Methods

Mandiant warns that the Scattered Spider cybercriminal group is using “brazen” social engineering attacks to target large enterprise …
The Clock Is Ticking: Why Phishing Remains The Fastest-Moving Cyber Threat in 2025

Cybersecurity professionals face an increasingly aggressive phishing threat landscape, and the 2025 KnowBe4 Phishing By Industry Benchmarking …
Cybercriminals Use Telegram Bots to Exfiltrate Data In Phishing Kit Campaign

KnowBe4 ThreatLabs has identified and analyzed a sophisticated cross-platform phishing campaign that utilizes Telegram as its primary …
You Are Still Vulnerable to Password Attacks When Using Passkeys

Just because you’re using a passkey doesn’t mean your password is gone.
Phishing Kits Are Growing More Sophisticated; Focused on Bypassing MFA

Researchers at Cisco Talos warn that major phishing kits continue to incorporate features that allow them to bypass multi-factor …
Talos Report: Phishing Attacks Surged in Q1 2025

Phishing was the initial access vector in 50% of attacks during the first quarter of 2025, according to a new report from Cisco Talos.
Warning: Phishing Campaign Impersonates the US Social Security Administration

Researchers at Malwarebytes warn that phishing emails are impersonating the US Social Security Administration (SSA) to trick users into …
Your KnowBe4 Compliance Plus Fresh Content Updates from April 2025

Check out the April updates in Compliance Plus so you can stay on top of featured compliance training content.
Your KnowBe4 Fresh Content Updates from April 2025

Check out the 21 new pieces of training content added in April, alongside the always fresh content update highlights, new features and events.
Exciting Leadership Updates at KnowBe4

To our valued KnowBe4 customers, partners, and community. I wanted to share some exciting developments happening at KnowBe4.
Xfinity Scam Might Explain Similar Scams

Recently, I covered a T-Mobile scam where a friend of mine narrowly avoided losing money. In that scam, the attackers called up pretending to …
Email Remains the Top Attack Vector for Cyberattacks

Email is still the most common attack vector for cyber threats, according to a new report from Barracuda.
Hundreds of Fortune 500 companies have hired North Korean operatives.

Cyberwire wrote: "WIRED has published a report on North Korea's efforts to obtain remote IT positions at foreign companies, noting that these …
Cybercriminals Impersonate DHS Amid Deportation Efforts

Researchers at INKY warn that criminals are impersonating the US Department of Homeland Security to launch phishing scams.
A Sneaky T-Mobile Scam and Lessons That Were Learned

A friend of mine got a call on his phone and he regrettably picked it up. The number was 267-332-3644. The area code is from Bucks County, PA,…
Researchers Warn of Surge in Infostealers Delivered Via Phishing

The number of infostealers delivered via phishing emails increased by 84% last year, according to a new report from IBM’s X-Force researchers.…
What Is Device Code Phishing?

Ever since Microsoft’s initial announcement on February 13, 2025, about a Russian nation-state phishing campaign using "device code phishing,"…
Criminals Exploit the Death of Pope Francis to Launch Scams

Scammers are exploiting the death of Pope Francis to launch social engineering attacks, according to researchers at Check Point.
AJ from The Inside Man Now Coaching Your Users Real-time with Security Coach

Do your users love The Inside Man? See more of beloved character AJ, now in SecurityCoach!
Introducing the KnowBe4 Academy: Your Path to Mastering Human Risk Management

We're thrilled to announce the launch of KnowBe4 Academy—a comprehensive learning ecosystem designed specifically for security administrators,…
Social Engineering Campaign Abuses Zoom to Install Malware

A social engineering campaign is abusing Zoom's remote control feature to take control of victims’ computers and install malware, according to…
Half of Organizations Lack Protection Against Email Spoofing

A new report from Valimail has found that 50% of organizations lack effective protection against email spoofing.
How Organizational Culture Shapes Cyber Defenses

Recently, I received an email at work from a company with whom I've had previous interactions. The email lacked context and contained an …
Breaking the Stigma: 90% of Employees Agree that Phishing Simulations Improve their Security Awareness

According to our independent survey of individuals across the UK, USA, Netherlands, France, Denmark, Sweden, the DACH region, and Africa who …
Warning: Ransomware Remains a Top Threat for SMBs

A new report from Sophos found that ransomware attacks accounted for over 90% of incident response cases involving medium-sized businesses in …
Broken Cyber Windows Theory

Have you ever walked down a street with broken windows, burnt out cars, graffiti and felt a bit uneasy? There's a reason for that, and it's …
Threat Actors Are Increasingly Abusing AI Tools to Help With Scams

Cybercriminals are increasingly using AI tools to assist in malicious activities, according to Microsoft’s latest Cyber Signals report.
Powering Down Vulnerability: Securing the Energy Sector's Supply Chain

The energy sector stands as a critical pillar of our society. From the electricity powering our homes to the fuel driving our industries, …
China Cybercriminals Behind Toll-Themed Smishing Attacks Surge in the US and UK

Resecurity warns that a China-based cybercriminal gang dubbed the “Smishing Triad” is launching a wave of road toll-themed SMS phishing …
[Scary] A New Real Cash Scam Sweeps Across the U.S. Warn Your Family and Friends!

Right now, today, thousands of people are being tricked into going to their banks or credit unions to withdraw large sums of cash and will …
Lack of Security Awareness Tops List of Obstacles to Cyber Defense

Most organizations cite low security awareness among employees as the biggest barrier to defending against cyberattacks, according to a new …
The Continued Abuse of Legitimate Domains: A Spike in the Exploitation of Google Drive to Send Phishing Attacks

First QuickBooks, then Microsoft, and now Google—will the hijacking of legitimate third-party platform communications stop escalating in 2025?…
How Does Human Risk Management Differ from Security Awareness Training?

In today's cybersecurity landscape, organizations face an ever-present and often underestimated threat: human risk. Despite significant …
AI-Powered Spear Phishing Can Now Outperform Human Attackers

Researchers at Hoxhunt have found that AI agents can now outperform humans at creating convincing phishing campaigns.
UK Organizations Cite Phishing as the Most Disruptive Type of Cyberattack

Phishing was the most prevalent and disruptive type of attack experienced by UK organizations over the past twelve months, according to the …
Hidden Threats in Our Power Grid: The Chinese Transformer Backdoor Scandal

America's critical infrastructure faces an unprecedented threat, and it's already installed in hundreds of locations across the nation.
Warning: QuickBooks Phishing Campaign Targets Taxpayers

Cybercriminals are capitalizing on tax season by launching phishing campaigns targeting QuickBooksusers, Malwarebytes reports.
Europe's Energy Sector at Risk: The Critical Need for Cybersecurity

Reliable energy is the backbone of any modern society. It powers our homes, industries, and economies. But what happens when this essential …
Beware the Tax Trap: Seasonal Urgency Drives a Spike in Tax-Related Phishing Scams

Cybercriminals are quick to exploit seasonal events — and tax season is no exception. It’s a yearly honeypot for cybercriminals, who take …
Shadow AI: A New Insider Risk for Cybersecurity Teams to Tackle Now

Disclaimer: Don't get me wrong, I love using generative AI daily for research and writing. This is about how other users could be using it …
64% of Australian Organizations Hit by Ransomware Were Forced to Halt Operations

Illumio’s recent Global Cost of Ransomware Study found that 64% of Australian companies hit by ransomware had to shut down operations as a …
Seeing (and Hearing) Isn’t Believing: My SEC Presentation on AI-Driven Scams

On March 6, I had the opportunity to speak and provide testimony at the SEC Investor Advisory Committee’s panel on Retail Investor Fraud in …
Securing Employee Identities: Expert Tips for Identity Management Day 2025

With this week being Identity Management Day on April 8th, it's the perfect reminder for organizations to focus on protecting their employees'…
Russian Threat Actor Launches Spear-Phishing Campaign Against Ukrainians

The Russian threat actor Gamaredon is targeting Ukrainians with spear-phishing documents related to troop movements, according to researchers …
North Korea Expands Its Fraudulent IT Worker Operations

North Korea’s fraudulent employment operations have expanded to hit countries around the world, with a particular focus on Europe, according …
The Real Deal: How Cybercriminals Exploit Legitimate Domains

When it comes to secure email gateways (SEGs), the narrative is quite simple. For years, organizations have relied on SEGs as the foundation …
Your KnowBe4 Compliance Plus Fresh Content Updates from March 2025

Check out the March updates in Compliance Plus so you can stay on top of featured compliance training content.
Upgraded Phishing-as-a-Service Platform Drives a Wave of Smishing Attacks

A phishing-as-a-service (PhaaS) platform dubbed ‘Lucid’ is driving a surge in SMS phishing (smishing) attacks, according to researchers at …
Online Gaming Platform Steam Tops List of Most Imitated Brands For the First Time

Steam was the most impersonated brand in phishing attacks during the first quarter of 2025, according to a new report from Guardio. The …
Your KnowBe4 Fresh Content Updates from March 2025

Check out the 58 new pieces of training content added in March, alongside the always fresh content update highlights, new features and events.
Phishing Attacks Lead to Theft in the Shipping Industry

Phishing attacks are driving a surge in “double brokering” scams in the shipping industry, according to Christian Reilly, Cloudflare’s Field …
Warning: QR Code Phishing (Quishing) Becoming Increasingly Stealthy

Attackers are using new tactics in QR code phishing (quishing) attacks, according to researchers at Palo Alto Networks’ Unit 42.
Malicious Memes: How Cybercriminals Use Humor to Spread Malware

Internet memes and viral content have become a universal language of online culture. They're easily shareable, often humorous, and can spread …
Compliance Plus Library Reaches 800 Pieces of Content

It seems like only yesterday that we launched the Compliance Plus training library as a result of customers asking us to address their needs …
The State of NIS2: A Fragmented Implementation Across the EU

The Network and Information Systems Directive 2022 (NIS2) was designed to strengthen the cybersecurity resilience of critical infrastructure …
Exploring the Implications of DORA: A New Global Standard For Financial Cybersecurity

As of January 17, 2025, the Digital Operational Resilience Act (DORA) came into force across all European Union member states, with the …
Most Phishing Emails Rely Purely on Social Engineering

99% of phishing emails that reached inboxes last year did not contain malware, according to a new report from Fortra.
Report: Phishing Remains the Most Prevalent Cyber Threat

INKY has published its annual report on email security, finding that phishing accounted for 30% of all reported cybercrimes last year.
Surge in Phishing Attacks Hijacking Legitimate Microsoft Communications

A KnowBe4 Threat Lab PublicationAuthors: By James Dyer, Threat Intelligence Lead at KnowBe4 and Lucy Gee, Cybersecurity Threat Researcher at …
Amount of Money Requested In BEC Attacks Nearly Doubled in Q4 2024

The average amount of money requested in business email compromise (BEC) attacks spiked to $128,980 in the fourth quarter of 2024, according …
The Human Element: Addressing Cybersecurity Risk in Danish and Swedish Organizations

We recently conducted research in Denmark and Sweden to understand security culture in local organizations better.
Act Now: Phishing-as-a-Service Attacks are on the Rise

Phishing-as-a-service (PhaaS) platforms drove a surge in phishing attacks in the first two months of 2025, according to researchers at …
Why Password Security Matters: The Danish and Swedish Password Problem

In today’s world, cybersecurity is more critical than ever. Organizations and individuals alike face a constant barrage of cyber threats, and …
Hundreds of Malicious Android Apps Received 60 Million Downloads

Bitdefender warns that a major ad fraud campaign in the Google Play Store resulted in more than 60 million downloads of malicious apps.
Key Takeaways from the KnowBe4 2025 Phishing Threat Trends Report

Our latest Phishing Threat Trends Report explores the evolving phishing landscape in 2025, from renewed tactics to emerging attack techniques.
Scammers Can Be Victims Too

There are thousands of people worldwide trying to scam you, hoping they can make you a victim, steal your money, and harm you in some way. …
Phishing Attacks Abuse Microsoft 365 to Bypass Security Filters

Threat actors are abusing Microsoft’s infrastructure to launch phishing attacks that can bypass security measures, according to researchers at…
Be Vigilant: BEC Attacks Are on the Rise

Business email compromise (BEC) attacks rose 13% last month, with the average requested wire transfer increasing to $39,315, according to a …
Agentic AI: Why Cyber Defenders Finally Have the Upper Hand

My two previous recent postings on AI covered “Agentic AI” and how that impacts cybersecurity and the eventual emergence of malicious agentic …
The Cybersecurity Confidence Gap: Are Your Employees as Secure as They Think?

Our recent research reveals a concerning discrepancy between employees' confidence in their ability to identify social engineering attempts …
Booking.com Phishing Scam Targets Employees in the Hospitality Sector

A phishing campaign is impersonating travel agency Booking.com to target employees in the hospitality industry, according to researchers at …
98% Spike in Phishing Campaigns Leveraging Russian (.ru) Domains

A KnowBe4 Threat Lab publicationAuthors: Martin Kraemer, Jeewan Singh Jalal, Anand Bodke, and James Dyer EXECUTIVE SUMMARY: We observed a 98% …
Protect Yourself: Social Engineering Fuels SIM Swapping Attacks

Group-IB has published a report on SIM swapping attacks, finding that attackers continue to use social engineering to bypass technical …
Make Your Real Emails Less Phishy

I infrequently get emails from customers who are frustrated because their employer sent out some legitimate mass email to all employees that …
245% Increase in SVG Files Used to Obfuscate Phishing Payloads

A KnowBe4 Threat Labs PublicationAuthors: James Dyer and Cameron Sweeney The KnowBe4 Threat Research team has observed a sustained increase in…
AI and AI-agents: A Game-Changer for Both Cybersecurity and Cybercrime

Artificial Intelligence (AI) is no longer just a tool—it is a game changer in our lives, our work as well as in both cybersecurity and …
Beware: Malvertising Campaign Hits Nearly a Million Devices

Microsoft warns that a widespread malvertising campaign hit nearly one million devices around the world. The campaign, which began on illegal …
U.S. Justice Department Charges China’s Hackers-for-Hire Working IT Contractor i-Soon

The U.S. Justice Department has charged ten Chinese nationals for acting as hackers-for-hire for the Chinese government.
The Myth of Geographic Immunity in Cybersecurity

In the realm of cybersecurity, perception often diverges from reality. A common misconception is that nation-state cybercriminals primarily …
Autonomous Agentic AI-Enabled Deepfake Social Engineering Malware is Coming Your Way!

I’ve been in the cybersecurity industry for over 36 years. Surprisingly, hackers and malware haven't changed all that much.
Your KnowBe4 Compliance Plus Fresh Content Updates from February 2025

Check out the February updates in Compliance Plus so you can stay on top of featured compliance training content.
Your KnowBe4 Fresh Content Updates from February 2025

Check out the 58 new pieces of training content added in February, alongside the always fresh content update highlights, new features and …
Warning: Ransomware Threats Increased Fourfold in 2024

Researchers at Barracuda observed a fourfold increase in ransomware threats last year, driven by increasingly sophisticated …
Software Will Become Agentic and the Security Lessons We Need To Learn

Ever since OpenAI publicly released ChatGPT in late 2022, people have been predicting the end of programmers.
Invoice or Impersonation? 36.5% Spike in Phishing Attacks Leveraging QuickBooks’ Legitimate Domain in 2025

A KnowBe4 Threat Lab PublicationAuthors: Martin Kraemer, James Dyer, and Lucy Gee Much like sending a phishing email from a compromised …
AI Literacy: A New Mandate Under the EU AI Act - What Your Organization Needs to Know

The European Union's AI Act is ushering in a new era of workplace requirements, with AI literacy taking center stage. Under Article 4, …
Data at Risk: 96% of Ransomware Attacks Involve Data Theft

A new report from Arctic Wolf has found that 96% of ransomware attacks now involve data theft as criminals seek to force victims to pay up.
Alert: Phishing Attacks Use New JavaScript Obfuscation Technique

Researchers at Juniper Threat Labs warn that phishing attacks are utilizing a new obfuscation technique to hide malicious JavaScript.
Q&A with Martin Kraemer on Information Sharing in Cybersecurity

Recently, Dr. Martin J. Kraemer, Security Awareness Advocate at KnowBe4, and Dr. William Seymour, Lecturer in Cybersecurity at King’s College …
Primary Refresh Tokens Aren’t Your Parent’s Browser Token

If you haven’t been paying attention closely enough, a new type of access control token, like a super browser token on steroids, is becoming …
Schools in Session: Surge in Phishing Attacks Targeting the Education Sector

A KnowBe4 Threat Lab PublicationAuthors: Jeewan Singh Jalal, Anand Bodke, Daniel Netto and Martin Kraemer
Announcing: Audiocasts - A New Podcast-Like Training Content Type
We are very excited to announce the addition of audiocasts, a new content type now available in the ModStore to help strengthen your security …
Protect Yourself from Job Termination Scams

ESET warns of a wave of phishing attacks informing employees that they’ve been fired or let go. The emails are designed to make the user panic…
Protect Your Devices: Mobile Phishing Attacks Bypass Desktop Security Measures

Zimperium warns of a surge in phishing attacks specifically tailored for mobile devices. These attacks are designed to evade desktop security …
KnowBe4 Named #1 Security Product and #2 Overall Software Product in G2’s 2025 Best Software Awards

KnowBe4 has been recognized in G2’s 2025 Best Software Awards, earning the top spot as the #1 Security Product and ranking #2 Overall Software…
Chinese Hackers Target Hospitals by Spoofing Medical Software

A Chinese government-backed hacking group is using fake medical software to compromise hospital patients' computers, infecting them with …
Phishing Attack Leads to Lateral Movement in Just 48 Minutes

Researchers at ReliaQuest have published a report on a phishing breach in the manufacturing sector that went from initial access to lateral …
Viral but Vulnerable: The Hidden Risks of Cybersecurity Misinformation on Social Media

It's no surprise that 18–29-year-olds are turning to social media for cybersecurity information. As digital natives, this age group naturally …
Warning: Russian Threat Actors Are Targeting Signal Accounts With Malicious QR Codes

Several Russian state-sponsored threat actors are using QR code phishing (quishing) to compromise Signal accounts, according to researchers at…
KnowBe4's Interview of a North Korean Fake Employee

You would think with all the global press we have received because of our public announcement of how we mistakenly hired a North Korean fake …
Phishing Kit Abuses Open Graph to Target Social Media Users

Researchers at Cyble warn that a phishing kit is abusing the Open Graph (OG) protocol to target social media users.
Phishing Attacks Increased by Nearly 200% in H2 2024

Phishing and malicious emails remained the primary vectors of infection during the second half of 2024, according to a new report from Acronis.
Spear Phishing is the Top Cyber Threat to the Manufacturing Sector

Spear phishing was the top cybersecurity threat to the manufacturing sector over the past six months, according to a report from ReliaQuest. …
Scanning for Trouble: Behind the Scenes of Our QR Code Phishing Demo

At KnowBe4, we constantly strive to stay ahead of emerging threats and create training content to warn users about the latest tactics used by …
Protect Your Data: Russian Spear-Phishing Targets Microsoft 365 Accounts

Several Russian threat actors, including the SVR’s Cozy Bear, are launching highly targeted spear phishing attacks against Microsoft 365 …
Phishing for Love: A Sharp Surge in Valentine’s Day-Themed Scams
Authors: Martin Kraemer, Security Awareness Advocate at KnowBe4 and James Dyer, Threat Intelligence Lead at KnowBe4 This Valentine’s Day, …
New Research: Ransomware Data Extortion Skyrocketing

Data theft extortion attacks increased by 46% in the fourth quarter of 2024, according to a new report from Nuspire.
[POLL] Sam Altman: "I don't do Google searches anymore." How about you?
I'm doing a quick poll because I find myself exactly where Sam is. But I would love to understand how that is for us IT pros here. Hence.. a …
New Phishing Campaign Targets The X Accounts of Politicians, Tech Companies, Cryptocurrency, And More

SentinelOne warns that a phishing campaign is targeting high-profile X accounts, including those belonging to US political figures, leading …
Facebook Users Beware: Thousands Hit by New Phishing Scam

Check Point warns that a large-scale phishing campaign is targeting Facebook accounts with phony copyright infringement notices.
2024 Was a Record-Breaking Year For Ransomware

2024 saw the highest-ever amount of ransomware attacks, according to a new report from NCC Group.
Cybersecurity Resilience and Culture Matters to Face the Growing Frequency and Sophistication of Cybercrime

Dr. Martin J. Kraemer discusses learning from The Word Economics Forum Cybersecurity Outlook 2025 report Last year, the British multinational …
From Madison Avenue to Malware

In the bustling world of 1960s Madison Avenue, a young advertising executive named Lester Wunderman was about to revolutionize the industry. …
Don’t Fall Victim: DeepSeek-Themed Scams Are on the Rise

Scammers are taking advantage of the newfound popularity of the China-based AI app DeepSeek, according to researchers at ESET.
Make-Shift Brand Impersonation: Abusing Trusted Domains with Open Redirects

A KnowBe4 Threat Lab publicationAuthors: Daniel Netto, Jeewan Singh Jalal, Anand Bodke, and Martin Kraemer
Warning: Organizations Need to Prep For AI-Powered Ransomware Attacks

The rise of agentic AI tools will transform the cybercrime landscape, according to a new report from Malwarebytes.
From Firewalls to Digital Well-Being: A Whole-School Approach to Online Safety

Recently, I started working with my children's school to enhance their online safety measures and develop a digital mindfulness course in …
Organizations Observed 50% Increase in Deepfakes and Phishing Scams in 2024

Nearly half (46%) of businesses observed an increase in deepfakes and generative AI-related fraud last year, a new report from AuthenticID has…
Warning: Phishing Campaign Targets Germany with New Malware

Researchers at Cisco Talos warn that a new phishing campaign is targeting users in Germany and Poland in an attempt to deliver several strains…
Your KnowBe4 Compliance Plus Fresh Content Updates from January 2025

Check out the January updates in Compliance Plus so you can stay on top of featured compliance training content.
Your KnowBe4 Fresh Content Updates from January 2025

Check out the 25 new pieces of training content added in January, alongside the always fresh content update highlights, new features and …
Beware: Mobile Phishing Mimicking the USPS Is On the Rise

Researchers at Zimperium warn that a large phishing campaign is impersonating the US Postal Service (USPS) to target mobile devices with …
The Rising Tide of Cybercrime Concerns in Africa

Our recent Africa Cybersecurity Awareness survey has revealed a startling surge in cybersecurity concerns among African users, with 58% of …
Using Genuine Business Domains and Legitimate Services to Harvest Credentials

A KnowBe4 Threat Lab PublicationAuthors: Jeewan Singh Jalal, Anand Bodke, and Martin Kraemer
Microsoft is Still the Most Commonly Impersonated Brand in Phishing Attacks

Microsoft, Apple, and Google were the most commonly impersonated brands in phishing attacks last quarter, according to researchers at Check …
Tips for Detecting Real-time Deepfakes: A Guide to Staying One Step Ahead

Deepfakes are no longer just the stuff of sci-fi thrillers—they’re here, and they’re deceptively good. From celebrity endorsements to …
[Eye Opener] Is DeepSeek The Next Threat in Social Engineering?

AI is advancing at lightning speed, but it’s also raising some big questions, especially when it comes to security. The latest AI making …
Beware of Toll Scam Texts: How Cybercriminals are Targeting U.S. Drivers

Drivers across the U.S. are being bombarded with fraudulent text messages claiming to come from toll operators like E-ZPass.
Nearly Three-Quarters of UK Education Orgs Have Sustained Cyberattacks

73% of educational institutions in the UK have sustained at least one cyberattack or breach in the past five years, according to researchers …
Phishing is the Top Security Threat For Smartphone Users
Phishing attacks are the most common security issue for smartphone users, according to a new study by Omdia.
84% of Healthcare Organizations Sustained Cyberattacks Last Year

A new survey by cybersecurity vendor Netwrix found that 84% of healthcare organizations spotted a cyberattack in the past twelve months, with …
4 Ways to Mature Your Human Risk Management Program

Human risk management (HRM) is now the primary approach to addressing the ongoing need for strong security cultures in organizations of all …
Russian Spear-Phishing Campaign Targets WhatsApp Accounts

The Russian threat actor “Star Blizzard” has launched a spear-phishing campaign attempting to compromise WhatsApp accounts, according to …
Malvertising Campaign Abuses Google Ads to Target Advertisers

Researchers at Malwarebytes are tracking a major malvertising campaign that’s abusing Google Ads to target individuals and businesses …
Threat Actors Abuse Google Translate to Craft Phishing Links

Threat actors are abusing Google Translate’s redirect feature to craft phishing links that appear to belong to, according to researchers at …
Phishing Campaign Attempts to Bypass iOS Protections

An SMS phishing (smishing) campaign is attempting to trick Apple device users into disabling measures designed to protect them against …
From Pig Butchering to People Talking

Interpol has recently recommended discontinuing the use of the term "Pig Butchering" in cybercrime discussions, expressing concern that such …
Effective Security Awareness Training Really Does Reduce Data Breaches

Social engineering and phishing are involved in 70% - 90% of data breaches. No other root cause of malicious hacking (e.g., unpatched software…
Your KnowBe4 Compliance Plus Fresh Content Updates from December 2024

Check out the December updates in Compliance Plus so you can stay on top of featured compliance training content.
Ransomware Gangs Claimed More Than 5,000 Attacks in 2024

Ransomware groups claimed responsibility for 5,461 attacks in 2024, with 1,204 of these attacks being publicly confirmed by victim …
Brad Pitt Romance Scams Pushed By AI-Enabled Deepfakes

I have helped people detect romance scams for decades. It is still very common for romance scammers to leverage both pictures of celebrities …
First Ever Magic Quadrant™ for Email Security Platforms by Gartner®

In cybersecurity, email has always been a critical concern. However, we feel the new 2024 Gartner® Magic Quadrant for Email Security …
Your KnowBe4 Fresh Content Updates from December 2024

Check out the 52 new pieces of training content added in December, alongside the always fresh content update highlights, new features and …
Japan Attributes More Than 200 Cyberattacks to China Threat Actor "MirrorFace"

Japan’s National Police Agency (NPA) has attributed more than 200 cyber incidents over the past five years to the China-aligned threat actor …
Deepfakes, Shallow Morals: The Real Issue Behind the UK's Crackdown

The UK government decided to wage war on explicit deepfakes. About time, right? But before we start celebrating, let's take a closer look.
Phishing Campaign Abuses Legitimate Services to Send PayPal Requests

A phishing campaign is abusing Microsoft 365 test domains to send legitimate payment requests from PayPal, according to Fortinet’s CISO Dr. …
Malicious WordPress Plugin Assists in Phishing Attacks

Researchers at SlashNext warn that cybercriminals are using a WordPress plugin called “PhishWP” to spoof payment pages and steal financial …
[BUDGET AMMO DEPT] WSJ: "Cybersecurity Is the King of Business Worries"

Kim S. Nash, the Deputy Bureau Chief at the Wall Street Journal who owns the cybersecurity beat wrote in her newsletter today: "Forget trade …
Phishing for Gamers: Fake Offers Invite Gamers to Test New Gaming Titles

A phishing campaign is targeting users with phony offers to beta test new video games, according to researchers at Malwarebytes.
Credential Phishing Increased by 703% in H2 2024

Credential phishing attacks surged by 703% in the second half of 2024, according to a report by SlashNext. Phishing attacks overall saw a 202%…
Tax-Themed Phishing Campaign Delivers Malware Via Microsoft Management Console Files

Securonix warns that tax-themed phishing emails are attempting to deliver malware via Microsoft Management Console (MSC) files.
FTC Warns Immigrants About Rising Social Media Immigration Scams

The Federal Trade Commission (FTC) has issued an urgent warning about a surge in immigration scams targeting immigrants and their families on …
Russia’s APT29 Launches Major Spear Phishing Campaign

Trend Micro warns that the Russian state-sponsored threat actor Earth Koshchei (also known as “APT29” or “Cozy Bear”) is using spear phishing …
"Get Beyond Security Awareness Training" Does Not Mean Forgetting About It

KnowBe4 is a big believer in focusing on decreasing human risk as the best way to decrease cybersecurity risk in most environments.
Attackers Abuse HubSpot’s Free Form Builder to Craft Phishing Pages

A threat actor is abusing HubSpot’s Free Form Builder service to craft credential-harvesting phishing pages, according to Palo Alto Networks’ …
James Bond-Style Scamming Profits Explode

There is a type of scam where victims are contacted by someone fraudulently posing as a popular trusted entity (e.g., Amazon, U.S. Post …
Mobile Phishing Attacks Use New Tactic to Bypass Security Measures

ESET has published its threat report for the second half of 2024, outlining a new social engineering tactic targeting mobile banking users.
No, KnowBe4 Is Not Being Exploited

Some of our customers are reporting “Threat Alerts” from Mimecast stating hackers have exploited KnowBe4 or KnowBe4 domains to send email …
AI-Powered Investment Scams Surge: How 'Nomani' Steals Money and Data
Cybersecurity researchers are warning about a new breed of investment scam that combines AI-powered video testimonials, social media …
Phishing Campaign Targets YouTube Creators

An email phishing campaign is targeting popular YouTube creators with phony collaboration offers, according to researchers at CloudSEK. The …
DarkGate Malware Distributed Via Microsoft Teams Voice Phishing

Threat actors are using voice phishing (vishing) attacks via Microsoft Teams in an attempt to trick victims into installing the DarkGate …
U.S. Justice Department Indicts Fake IT Workers From North Korea

The U.S. Justice Department revealed indictments against 14 North Korean nationals for their involvement in a long-running scheme designed to …
Critical Infrastructure Under Siege: 42% Spike in Ransomware Attacks on Utilities

Ransomware attacks targeting utilities have surged by 42% over the past year, with spear phishing playing a major role in 81% of cases, …
94% of U.K. Businesses Aren’t Adequately Prepared for AI-Driven Phishing Scams

A new report makes it clear that U.K. organizations need to do more security awareness training to ensure their employees don’t fall victim to…
Sophisticated Phishing Campaign Attempts to Bypass SEGs

A widespread phishing campaign is attempting to steal credentials from employees working at dozens of organizations around the world, …
Mobile Phishing Campaign Targets Job Seekers

Researchers at Zimperium warn that a phishing campaign is targeting Android phones to deliver the Antidot banking trojan.
Be Careful of Malicious Ads

For decades, we have all been warned to be appropriately skeptical of internet search engine results. Sadly, most people are not.
Nearly Half a Billion Emails in 2024 Were Malicious

A new report from Hornetsecurity has found that 427.8 million emails received by businesses in 2024 contained malicious content.
Phishing Attacks Are Now Leveraging Google Ads to Hijack Employee Payments

Researchers at Silent Push warn that a phishing campaign is using malicious Google Ads to conduct payroll redirect scams.
Phishing Holds the Top Spot as the Primary Entry Point for Ransomware Attacks

New analysis of ransomware attacks shows that phishing is the primary delivery method and organizations need to offer more effective security …
Your KnowBe4 Compliance Plus Fresh Content Updates from November 2024

Check out the November updates in Compliance Plus so you can stay on top of featured compliance training content.
The Rise of Phishing Attacks: How New Domain Extensions Are Fueling Cyber Crime

In recent years, the world of cybersecurity has witnessed a concerning trend: a significant increase in phishing attacks.
IRS Warns of Holiday-Themed Shopping Scams

The US Internal Revenue Service (IRS) has issued an advisory warning taxpayers to be on the lookout for holiday-themed shopping scams.
Why Controversial Phishing Emails Do Not Work

Frequently, when a cybersecurity training manager sends out a controversial simulated phishing attack message that angers a bunch of employees…
Unwrapping Cybersecurity: A Festive "Die Hard" Guide

It is the holiday season. Think twinkling lights, the scent of pine, and cyber threats lurking in the shadows, waiting to pounce quicker than …
FBI Warns of Cybercriminals Using Generative AI to Launch Phishing Attacks

The US Federal Bureau of Investigation (FBI) warns that threat actors are increasingly using generative AI to increase the persuasiveness of …
Your KnowBe4 Fresh Content Updates from November 2024

Check out the 84 new pieces of training content added in November, alongside the always fresh content update highlights, events and new …
Malicious Google Ads Target Users Seeking Solutions to Printer Problems
Scammers are abusing Google ads to target users searching for help with printer problems, according to researchers at Malwarebytes.
Phishing Attacks Impersonating Big Brands Starts to Zero in on Just One Brand
The latest data on brand phishing trends shows one brand dominating quarter over quarter, but also continuing to take on a larger share of the…
And the Winner of The Inside Man Biggest Fan Contest 2024 is…
It’s been several weeks since the exciting premiere of The Inside Man - Season 6 in St. Petersburg, Fl. If you missed my post, I talked about …
China Threat Actor Targets Individuals and Entities in Japan Via Spear Phishing Campaign
Researchers at Trend Micro warn that the China-aligned threat actor Earth Kasha has launched a new spear phishing campaign targeting …
The Cruel Twist: When Fake Firing Leads to Real Hacking
Cybercriminals are constantly evolving their tactics to exploit our vulnerabilities. A recent phishing campaign has taken this to a new low, …
[NEW PRODUCT]: KnowBe4’s AIDA: Revolutionizing Security Awareness Training with AI-Powered Automation and Personalization
Technological advances in artificial intelligence (AI) are only making the ongoing problem of social engineering worse.
Malicious Loan Apps Target Android Users in Africa, South America and Asia
Researchers at McAfee warn of a surge in malicious loan apps targeting Android users across South America, Southern Asia, and Africa.
Nearly Every Hacker Believes AI Tools Have Created a New Attack Vector
A new survey of hackers shows that AI is not only empowering hackers to be more effective, but that AI itself is “ripe for exploitation.”
CISA Strongly Recommends Phishing-Resistant MFA
We are excited to see the Cybersecurity Infrastructure Security Agency (CISA) and outgoing Director Jen Easterly strongly recommend …
75% of Black Friday Spam Emails Are Scams
Three out of four Black Friday-themed spam emails are scams, according to researchers at Bitdefender. Most of these scams are targeting users …
[New!] Check Out These Powerful New KnowBe4 AI Features
You do not want to miss this one! You can now see our AI Defense Agents (AIDA) live in a demo, now that they are released. Customers can now …
Chinese Threat Actor Targets Black Friday Shoppers With Phishing Campaign
Researchers at EclecticIQ warn that the financially motivated Chinese threat actor “SilkSpecter” has launched a phishing campaign targeting …
U.K. Residents are Victims of the Latest Phishing Scam Targeting Starbuck Customer Credentials
Analysis of a new phishing attack highlight just how easy it can be to spot these kinds of attacks if recipients were properly educated.
Phishing Emails Use SVG Files to Avoid Detection
Phishing emails are increasingly using Scalable Vector Graphics (SVG) attachments to display malicious forms or deliver malware, …
Threat Group Use AI Adult-Based “Deepnude” Image Generator Honeypots to Infect Victims
The threat group FIN7 is using the lure of generating nude images of favorite celebrities to get victims to download their NetSupport RAT.
Phishing Attacks Exploits the Open Enrollment Period
A phishing campaign is impersonating HR to target employees who are making annual insurance changes during the open enrollment period, …
Fraud Awareness Week
The Association of Certified Fraud Examiners (ACFE) recently released a report Occupational Fraud 2024: A Report to the Nations, where they …
Ransomware Gangs Evolve: They're Now Recruiting Penetration Testers
A new and concerning cybersecurity trend has emerged. According to the latest Q3 2024 Cato CTRL SASE Threat Report from Cato Networks, …
Out of 29 Billion Cybersecurity Events, Phishing was the Primary Method of Initial Attack
The newly released single largest analysis of cyber attacks across all of 2023 show a strong tie between the use of phishing and techniques …
Beware of Fake Tech Support Scams
About five years ago, I was having trouble with an expensive brand-name refrigerator that my wife and I had bought. It was a great …
Dark Side of Deals: Emerging Scams for Black Friday, Cyber Monday and Giving Tuesday
As the holiday shopping season kicks into high gear, cybercriminals are gearing up too. This year, alongside the usual suspects, we're seeing …
Threat Actors are Sending Malicious QR Codes Via Snail Mail
The Swiss National Cyber Security Centre (NCSC) has warned of a QR code phishing (quishing) campaign that’s targeting people in Switzerland …
A New Era In Human Risk Management:Introducing KnowBe4 HRM+
Cybersecurity threats grow more sophisticated by the day. Amid this constant change, one truth remains: people are simultaneously our greatest…
Purina’s Champions Program Is the Best I Have Seen
In my most recent book, Fighting Phishing: Everything You Can Do to Fight Social Engineering and Phishing, I highlight the use of “champions,"…
The World Premiere of The Inside Man - Season 6 in St. Petersburg, Florida
KnowBe4, the leading platform for security awareness training, is excited to bring the award-winning original series, "The Inside Man,” back …
Phishing Attacks Exploit Microsoft Visio Files and SharePoint
Threat actors are exploiting Microsoft Visio files and SharePoint to launch two-step phishing attacks, according to researchers at Perception …
Half of all Ransomware Attacks This Year Targeted Small Businesses
New data shows just how crippling ransomware has been on small businesses that have fallen victim to an attack and needed to pay the ransom.
[World Premiere] KnowBe4 Debuts New Season 6 of Netflix-Style Security Awareness Video Series - “The Inside Man”
We’re thrilled to announce the long-awaited sixth season of the award-winning KnowBe4 Original Series - “The Inside Man” is now available in …
Fortifying Defenses Against AI-Powered OSINT Cyber Attacks
In the ever-evolving landscape of cybersecurity, the convergence of Artificial Intelligence (AI) and Open-Source Intelligence (OSINT) has …
Criminal Threat Actor Uses Stolen Invoices to Distribute Malware
Researchers at IBM X-Force are tracking a phishing campaign by the criminal threat actor “Hive0145” that’s using stolen invoice notifications …
Nation-State Threat Actors Rely on Social Engineering
A new report from ESET has found that most nation-state threat actors rely on spear phishing as a primary initial access technique.
Step-by-Step To Creating Your First Realistic Deepfake Video in a Few Minutes
Learn how to step-by-step create your first realistic deepfake video in a few minutes.
[FREE RESOURCE KIT] Stay Cyber Safe this Holiday Season with Our Free 2024 Resource Kit!
Isn’t it typical for bad actors to strike when we’re distracted and busy during this time of year?
Criminals Use Search Engine Poisoning to Boost Phishing Pages
Researchers at Malwarebytes warn that cybercriminals are using search engine poisoning to boost phishing pages to the top of Bing’s search …
Recon 2.0: AI-Driven OSINT in the Hands of Cybercriminals
Cybercriminals are using artificial intelligence (AI) and generative AI in open source intelligence (OSINT) activities to target your …
[Eye Opener] Attackers Don’t Hack, They Log In. Can You Stop Them?
The latest trend in cybercrime is that attackers don't really focus on “hacking” in; they’re logging in.
Phishing Campaign Impersonates OpenAI To Collect Financial Data
Cybercriminals are impersonating OpenAI in a widespread phishing campaign designed to trick users into handing over financial information. The…
The Deceptive Media Era: Moving Beyond "Real vs. Fake"
As society grapples with the rapid advancement of AI and synthetic media, we've been asking the wrong question. The focus on whether content …
Attackers Abuse DocuSign to Send Phony Invoices
Threat actors are abusing DocuSign’s API to send phony invoices that appear “strikingly authentic,” according to researchers at Wallarm.
[Last Chance] KB4-CON APJ Cybersecurity Event is in 10 Days
Tick tock, the countdown is on! KB4-CON APJ starts in just 10 days, and you still have time to register!
BlackBasta Ransomware Gang Uses New Social Engineering Tactics To Target Corporate Networks
ReliaQuest warns that the BlackBasta ransomware gang is using new social engineering tactics to obtain initial access within corporate networks.
Attackers Abuse Eventbrite to Send Phishing Emails
Attackers are abusing Eventbrite’s scheduling platform to send phishing emails, according to researchers at Perception Point. These attacks …
Celebrating 5 Million Learners: The Evolution of KnowBe4's Compliance Plus
When you think of KnowBe4, you might immediately picture phishing simulations, password security modules, or other security awareness training…
If Social Engineering Is 70% - 90% of Attacks, Why Aren’t We Acting Like It?
Over a decade ago, I noticed that social engineering was the primary cause for all malicious hacking. It has been that way since the beginning…
Your KnowBe4 Compliance Plus Fresh Content Updates from October 2024
Check out the October updates in Compliance Plus so you can stay on top of featured compliance training content.
Phishing Alert: Cybercriminals Impersonating KnowBe4 Training Emails
In the ever-evolving landscape of cybersecurity threats, we've recently encountered a sophisticated phishing attempt targeting one of our …
Every Cybersecurity List Should Be a Risk-Ranked List
Cybersecurity is all about risk management and reduction. You cannot get rid of all risk. Well, I guess you could, but you (and everyone else)…
The Rise of Outsourced Cybersecurity: How CISOs are Adapting to New Challenges
Chief Information Security Officers (CISOs) are facing unprecedented challenges. The combination of increasingly sophisticated cyber threats, …
Threat Actors Abuse LinkedIn to Target Job Seekers
Threat actors are targeting people who have recently lost their jobs with employment scams on LinkedIn, according to researchers at …
Your KnowBe4 Fresh Content Updates from October 2024
Check out the 60 new pieces of training content added in October, alongside the always fresh content update highlights, events and new features.
QR Code Phishing is Growing More Sophisticated
Sophos describes a QR code phishing (quishing) campaign that targeted its employees in an attempt to steal information.
75% of Organizations Have Experienced a Deepfake-Related Attack
As generative AI evolves and becomes a mainstream part of cyber attacks, new data reveals that deepfakes are leading the way.
Crooks are Sending Halloween-Themed Phishing Emails
Halloween-themed spam and phishing emails have surged over the past two months, with a significant increase beginning in October, according to…
4 out of 10 Phishing Emails Are Sent From a Compromised Email Account
Analysis of phishing emails in the second quarter of this year paints a picture of what security teams and vigilant recipients should expect …
Threat Actors Compromise Valid Accounts Via Social Engineering
Phishing remains a top initial access vector for cyberattacks, according to researchers at Cisco Talos.
Cyber Attack Tools Now Being Used To Help Phishing Pages Avoid Detection
Cybercriminals are offering tools to help phishing pages avoid detection by security tools, according to researchers at SlashNext.
The £3 Million Daily Heist
A recent report from UK Finance covered by the BBC paints a concerning picture of the evolving landscape of financial fraud. With a 16% rise …
Cybersecurity Budgets Are Increasing, but Security Leaders Don’t Think It’s Enough
Despite the belief that today’s SOC should be doing the lion’s share of protecting an organization, new data shows reliance on more than just …
[2025 Is Too Late] - European Companies Must Act Now Against AI-Powered Cyber Threats
European Organizations Can't Afford to Wait: Critical Cybersecurity Threats Demand Immediate Action
Ransomware Gang Attack Tactics Have Shifted
A recent analysis of the ransomware group Meow raises the notion that groups are evolving from using encryption as a tactic to more profitable…
New Research: 140% Increase in Callback Phishing
Researchers at Trustwave observed a 140% increase in callback phishing attacks between July and September 2024. Callback phishing is a social …
More Than 33,000 People in the UK Have Been Hacked Over the Past Year
Action Fraud, the UK’s national fraud and cyber crime reporting service, warns that more than 33,000 people have reported that their online …
Nearly Two-Thirds of IT Leaders Have Fallen For Phishing Attacks
Sixty-four percent of IT leaders have clicked on phishing links, a new survey by Arctic Wolf has found. Despite this, 80% of these same …
Where Do I Point the Camera?
It's October 10th, 2024, and I've just stepped out of KB4-CON EMEA, my head buzzing with insights and my notebook filled with scribbles. I …
Cyber Attackers are Adopting a “Mobile First” Attack Strategy
With 16+ billion mobile devices in use worldwide, new data sheds light on how cyber attackers are shifting focus and tactics to put attacks …
KnowBe4's Cybersecurity Experts Shine at Barnes & Noble in New York City
New York City's iconic Barnes & Noble on 5th Avenue recently featured the newly released books of two of KnowBe4's leading cybersecurity …
North Korean IT Worker Threat: 10 Critical Updates to Your Hiring Process
KnowBe4 was asked what changes were made in the hiring process after the North Korean (DPRK) fake IT worker discovery. Here is the summary and…
FBI Warns Scammers Are Targeting Law Firms For Phony Debt Collections
The U.S. FBI warns that scammers are attempting to trick law firms into transferring money as part of a phony debt collection scheme.
Phishing Attacks Are Abusing Legitimate Services to Avoid Detection
Microsoft warns that threat actors are abusing legitimate file-hosting services to launch phishing attacks. These attacks are more likely to …
UK Company Hacked After Accidentally Hiring North Korean Cybercriminal
In a shocking turn of events, an unnamed company based in the UK has fallen victim to a sophisticated cyber attack after inadvertently hiring …
AI-Enhanced Cyber Attacks Top the List of Potential Threats Facing Data Security
AI is quickly becoming the basis for more cyber attacks, leading organizations to realize the risk it presents. A new report now shows that …
Chinese Threat Actor Targets OpenAI With Spear-Phishing Attacks
OpenAI has disclosed that its employees were targeted by spear-phishing attacks launched by a suspected Chinese state-sponsored threat actor.
The Number of Malicious Emails Reaching Inboxes Is Declining
New research shows that less malicious emails are getting past security scanners to the inbox, but also provides details about how phishing …
North Korean Hackers Continue to Target Job Seekers
A North Korean threat actor is launching social engineering attacks against job seekers in the tech industry, according to researchers at Palo…
KnowBe4 Named a Leader in the Fall 2024 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR) Software
We are excited to announce that KnowBe4 has been named a leader in the Fall 2024 G2 Grid Report for Security Orchestration, Automation, and …
KnowBe4 Named a Leader in the Fall 2024 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares security awareness training (SAT) …
What Spending 3 Hours in IKEA Taught Me About Cybersecurity Awareness
It was a Saturday morning, and I had grand plans. By "grand plans," I mean sitting on the sofa, watching reruns of "The IT Crowd," and …
44% of U.S. Organizations Experienced One or More Ransomware Attacks in the Last Year
As ransomware becomes more pervasive, new data provides insight into how well organizations are responding and the attack vector being used …
Meet SmartRisk Agent™: Unlock Your New Human Risk Management
Depending on who you ask, between 70 and 90 percent of cyber risk has human error as the root cause. That's why Human Risk Management (HRM) is…
"Operation Kaerb" Takes Down Sophisticated Phishing-as-a-Service Platform “iServer”
A partnering of European and Latin American law enforcement agencies took down the group behind the mobile phone credential theft of 483,000 …
Sextortion Scammers Attempt to Hit “Close to Home”
We live in a world where, despite the sharing of information online, we feel like those interactions will never reach home. But a new scam – …
Trinity Ransomware Targets the Healthcare Sector
The Trinity ransomware gang is launching double-extortion attacks against organizations in the healthcare sector, according to an advisory …
Google App Scripts Become the Latest Way to Establish Credibility and Automate Phishing Attacks
Cybercriminals have found a new way of leveraging legitimate web services for malicious purposes, this time with the benefit of added …
Hurricane Deepfakes Flood Social Media
As the recent hurricane Helene caused major damage and as hurricane Milton is expected to make landfall in Florida soon, deepfakes are …
Attackers Abuse URL Rewriting to Evade Security Filters
Attackers continue to exploit URL rewriting to hide their phishing links from email security filters, according to researchers at Abnormal …
[Cybersecurity Awareness Month] Keeping Your Mobile Devices Secure from the ‘Inside’ Out
As remote work and connecting while traveling has become the norm, mobile device security responsibilities have also increased.
Free Phishing Platform Has Created More than 140,000 Spoofed Websites
A free phishing-as-a-service (PhaaS) platform named Sniper Dz has assisted in the creation of more than 140,000 phishing sites over the past …
What Bletchley Park Can Teach Us About Building a Strong Security Culture
During World War II, a group of brilliant minds led by Alan Turing gathered at Bletchley Park in England to crack the German Enigma code. This…
North Korea's Secret IT Army and How to Combat It
Organizations around the world are unknowingly recruiting and hiring fake employees and contractors from North Korea. These sophisticated …
Financial Services Industry Experiences a Massive Increase in Brand Abuse
Industry analysis of the domains used behind phishing and brand impersonation attacks show financial institutions are being leveraged at an …
Infostealer Threat Group “Marko Polo” Evolving Into an “Empire”
New research by Recorded Future provides insight into how advanced and sophisticated the threat group Marko Polo has become since launching in…
Don’t Put Real Answers Into Your Password Reset Questions
This recent article on how a hacker used genealogy websites to help better guess victims' password reset answers made it a great time to share…
New VPN Credential Attack Goes to Great Lengths to Obtain Access
A new “so-phish-ticated” attack uses phone calls, social engineering, lookalike domains, and impersonated company VPN sites to gain initial …
Cybercriminal Gang Targeting SMBs Using Business Email Compromise
Researchers at Todyl have published a report on a major cybercriminal group that’s conducting business email compromise (BEC) attacks against …
The U.K.'s NCSC and U.S. FBI Warn of Iranian Spear-Phishing Attacks
The U.K.’s National Cyber Security Centre (NCSC) and the U.S. FBI have released an advisory warning of Iranian state-sponsored spear-phishing …
Dick’s Sporting Goods Cyber Attack Underscores Importance of Email Security and Internal Controls
The recent cyber attack on Dick's Sporting Goods makes it clear that email played a critical role and emphasizes the need for better security …
From Desire Paths to Security Highways: Lessons from Disney's Approach to User-Centric Design
When Walt Disney first unveiled the Magic Kingdom, he made a decision that would revolutionize theme park design - and inadvertently offer a …
The Rise of Deepfake Scams: A Wake-Up Call After US Senator Becomes Latest Victim
In an era where technology continues to blur the lines between reality and fiction, a recent incident involving U.S. Senator Ben Cardin serves…
Threat Actors Behind MFA Bypass Service ‘OTP Agency’ Plead Guilty to Fraud
The criminal prosecution of the threat actors behind the "OTP Agency" has highlighted an ingenious new tactic that cybercriminals can use to …
New Survey Shows 40% of Respondents Never Received Cybersecurity Training From Their Employer
Yubico has published a survey of 20,000 people from 10 countries around the world, finding that 40% of respondents have never received …
[Cybersecurity Awareness Month] Responding to Cyber Incidents the ‘Inside Man’ Way: Fiona's Approach
In a world where cybersecurity incidents are no longer a matter of if they will happen, but when, having a solid incident response plan is a …
The Number of Ransomware Attacks Around the World Increased by 73% in 2023
The number of ransomware attacks around the world increased by 73% in 2023, according to a new report by the Institute for Security and …
Your KnowBe4 Compliance Plus Fresh Content Updates from September 2024
Check out the September updates in Compliance Plus so you can stay on top of featured compliance training content.
From Tetris to Minecraft: The Evolution of Security Awareness into Human Risk Management
Once upon a time, security awareness training resembled a never-ending game of Tetris. Threats cascaded down, demanding swift action and …
Scammers Use QR Code Stickers to Target UK Motorists
Netcraft warns that scammers are posting QR code stickers on parking meters in the UK and other European countries.
Your KnowBe4 Fresh Content Updates from September 2024
Check out the 40 new pieces of training content added in September, alongside the always fresh content update highlights, events and new …
The AI Revolution: Balancing Innovation and Ethics in the Age of Intelligent Technology
Artificial intelligence (AI) is revolutionizing most, if not all, industries worldwide. AI systems use complex algorithms and large datasets …
Election-Themed Phishing Threats Are on the Rise
Researchers at ReliaQuest have published a report looking at cyber threats surrounding the upcoming US presidential election, warning that …
[WTH?] Critical Vulnerabilities in Automated Tank Gauges. This Is Not OK.
A new wave of concern has surfaced around the security of Automated Tank Gauges (ATGs), critical systems that monitor and manage liquid levels…
[Cybersecurity Awareness Month] From ‘The Inside Man’ to Real Life: AI's Role in Modern Cyber Threats
AI and AI-generated deepfakes are proving to be the most intriguing, and in some ways troubling, recent advances in technology.
McAfee Discovers New Phishing Campaign Targeting GitHub Users
A phishing campaign is targeting GitHub users with phony CAPTCHA pages, according to researchers at McAfee. The phishing emails ask users to …
Scammers Abuse Virtual Shopping Lists to Trick Walmart Customers
Threat actors are abusing virtual shopping lists to trick Walmart customers into transferring money or disclosing personal information, …
Half of all Financial Services Cyber Attacks Start with a Very Costly Phish
New analysis of attacks on the financial sector shows that the combination of phishing emails and compromised credentials is a recurring — and…
Educate Your Users About Malicious SEO Poisoning Attacks
Since the beginning of computers, social engineering has been the number one way that computers and networks have been compromised. Social …
Zscaler: There are 200 Malicious Lookalike Domains for Every 1 Impersonated Brand
Analysis of typosquatting and brand impersonation activity across 500 of the most visited domains provides insight in to how these techniques …
Online Scams Are Shortening Their Cycles and Making More Money
New analysis of blockchain activity shows scammers are needing less time to obtain crypto payments and are seeing higher payoffs per scam.
Phishing Attacks Abuse Content Creation and Collaboration Platforms
Researchers at Barracuda have observed an increase in phishing attacks that abuse popular content creation and collaboration platforms. These …
Beyond Analyst Reports: KnowBe4's Undeniable Leadership in Human Risk Management
Analyst reports aim to provide market insights. But when it comes to Human Risk Management (HRM), we’ve noticed that they often fall short of …
The Inside Man Biggest Fan Contest is Heating Up
We are halfway through our annual The Inside Man Biggest Fan Contest, and we already have some amazing entries! Encourage your users to get …
U.S. Government Indicts Chinese National For Alleged Spear Phishing Attacks
The U.S. Justice Department has indicted a Chinese national, Song Wu, for allegedly sending spear phishing emails to employees at various U.S.…
A Must See for KnowBe4 Customers and Partners: Geoff White to Keynote KB4-CON EMEA 2024
As a valued KnowBe4 customer and partner, we're thrilled to bring you exciting news about our upcoming KB4-CON EMEA 2024 in London.
North Korean Hackers Target Software Developers With Phony Coding Tests
Researchers at ReversingLabs warn that North Korea’s Lazarus Group is targeting software developers with phony job interviews.
SANS Releases Guide to Address Rise in Attacks on Manufacturing and Industrial Control Systems
Increased ransomware attacks on industrial control systems (ICS), mixed with general ICS insecurity found across the manufacturing sector, has…
Cost of Cybercrime Estimated 15.6 Trillion in 2029
Statista projects that the total cost of cybercrime will increase from $6.4 trillion between 2024 and 2029, reaching a staggering $15.63 …
CyberheistNews Vol 14 #38 [CODE RED] A Must-See New Webinar: How To Block North Korean Infiltrators
Phishing Attack Takes a Two-Step Approach to Leverage Legitimate Sites and Evade Detection. [4-Minute Survey] Share Your …
[Cybersecurity Awareness Month] Prepare for All Manner of Cyber Threats Like the Heroes of ‘The Inside Man’
Mark Shepherd, the Inside Man, is on a mission.
New Ransomware Threat Group, RansomHub, is so Effective, the NSA is Already Warning You About Them
The latest evolution of the ransomware service model, RansomHub, has only been around since February of this year, but its affiliates are …
BEC Scams Have Caused $55 Billion in Losses Over the Past Ten Years
Business email compromise (BEC) attacks have caused more than $55 billion in losses between 2013 and 2023, according to an advisory from the …
[4-Minute Survey] Share Your Thoughts on AI in InfoSec With Me?
Can you help me with your input? I'd love your thoughts about AI in InfoSec. This is a super short survey that asks about any AI tools you use…
Authorized Push Payment Fraud Responsible for Over Half of U.K. Frauds and Scams
Research from The Financial Ombudsman Service, a U.K. based organization dedicated to helping citizens with free financial advice, has found …
Attackers Using HTTP Response Headers to Redirect Victims to Phishing Pages
Researchers at Palo Alto Networks’ Unit 42 warn that attackers are using refresh entries in HTTP response headers to automatically redirect …
Legal Firms Increasingly Targeted by Phishing Attacks, Ransomware

Researchers at Bitdefender warn that law firms are high-value targets for ransomware gangs and other criminal threat actors. Attackers …
Forget the Talent Gap – It’s an Experience Gap
South Africa’s cybersecurity workforce shortage mirrors global trends, but also faces local factors like underinvestment in basic education, …
Losses From Investment Scams have Increased Six-Fold Since 2021
The Better Business Bureau (BBB) has observed a six-fold increase in losses from investment scams over the past three years. The BBB has …
Upcoming Webinar On How To Avoid Hiring Nation-State Fake Employees
In July 2024, KnowBe4 revealed that we had unknowingly hired a North Korean who was pretending to be someone else. We locked down the laptop …
Election-Themed Scams Are on the Rise

Researchers at Malwarebytes warn of a surge in election-themed scams ahead of November’s presidential election in the US. These attacks can be…
Use of Malicious Links Surges by 133% in Q1, Setting the Tone for the First Half of 2024
Threat actors are opting for malicious links over attachments in email-based attacks because it gives them a critical advantage that many …
Phishing Attack Takes a Two-Step Approach to Leverage Legitimate Sites and Evade Detection
Analysis of a new phishing attack demonstrates how attackers may take a longer path to reach their malicious goals while staying “under the …
Manufacturing Sector Is the Latest Target of Advanced Credential Harvesting Attacks
A new attack runs slow and steady, focused on compromising large manufacturing companies using contextual social engineering to trick victims …
Phishing is Still the Top Initial Access Vector
Phishing remains a top initial access vector for threat actors, according to researchers at ReliaQuest. Phishing and other social engineering …
Threat Actors Increasingly Exploit Deepfakes for Social Engineering
The availability of deepfake technology has given threat actors a valuable tool for social engineering attacks, according to researchers at …
[Security Masterminds Podcast] The Human Side of Cybersecurity: Bridging the Gap with Empathy and Strategy
In cybersecurity, technology often takes center stage. From the latest AI-driven defenses to sophisticated encryption techniques, it's easy to…
Organizations in the Middle East Targeted By Malware Impersonating Palo Alto GlobalProtect VPN
A social engineering campaign is targeting entities in the Middle East using malware that impersonates Palo Alto Networks’ GlobalProtect VPN, …
Major Scam Operation Uses Deepfake Videos
Researchers at Palo Alto Networks’ Unit 42 are tracking dozens of scam campaigns that are using deepfake videos to impersonate CEOs, news …
Your KnowBe4 Compliance Plus Fresh Content Updates from August 2024
Check out the August updates in Compliance Plus so you can stay on top of featured compliance training content.
Scammers Use Fake Funeral LiveStream Social Media Posts to Extort Victims
In a new low for cybercriminals, a new scam attempts to take advantage of those grieving the loss of a loved one, and charges their credit …
Nearly Half of Mid-Market and Enterprise Organizations Have Experienced Four or More Ransomware Attacks in the Last Year
New data exposes the reality of ransomware attacks today, including their frequency, impact, ransom payment – and the involvement of human …
Threat Actors Abuse Microsoft Sway to Launch QR Code Phishing Attacks
Researchers at Netskope last month observed a 2000-fold increase in traffic to phishing pages delivered through Microsoft Sway.
U.S. Experiences 52% Increase in the Number of Ransomware Attacks in One Year
New analysis of current ransomware attacks shows a massive focus on U.S. organizations, with growth spread across nearly every industry.
Your KnowBe4 Fresh Content Updates from August 2024
Check out the 29 new pieces of training content added in August, alongside the always fresh content update highlights, events and new features.
Fewer, High-Profile Ransomware Attacks Are Yielding Higher Ransoms
Analysis of cryptocurrency payments made on the blockchain highlights shifts in the size and frequency of ransomware attacks and may paint a …
Iran’s APT42 Targets WhatsApp Users With Spear-Phishing Attacks
Researchers at Meta have published details on Iranian spear-phishing attacks targeting WhatsApp accounts. The activity is attributed to APT42,…
Email Compromise Remains Top Threat Incident Type for the Third Quarter in a Row
New analysis of Q2 threats shows a consistent pattern of behavior on the part of threat actors and threat groups, providing organizations with…
Phishing Attacks Are Increasingly Targeting Social Media and Smartphone Users
Threat actors are increasingly tailoring their attacks to target social media apps and smartphone users, according to a new report from the …
More Carrots and Fewer Sticks
This blog was co-written by Perry Carpenter and Roger A. Grimes. As I sit in the 2024 Seattle Convene conference this week and listen to …
Ransomware Recovery Costs Have Doubled for State and Local Governments
Thirty-four percent of state and local government entities were hit by ransomware in 2024, a new report from Sophos has found. While this is a…
KnowBe4 Expands Children’s Interactive Cybersecurity Activity Kit for 2024/2025 School Year
Can you believe it’s already back-to-school time for many? Where has the summer gone?
Business Email Compromise Scams Rise 20%, Making up Nearly Half of all Spam Emails
New research on email threats points to AI-based tools to assist in generating BEC content. And the overwhelming targeted role may or may not …
The Number of Email-Based Cyber Attacks Detected Surge 239% in 1H 2024
New data shows the most prevalent and obvious path into an organization – email – continues to be exploited by a growing number of …
Malvertising Campaign Impersonates Dozens of Google Products
A malvertising campaign is abusing Google ads to impersonate Google’s entire product line, according to researchers at Malwarebytes. The …
Deceptive AI: A New Wave of Cyber Threats
As artificial intelligence (AI) technology advances, its influence on social media has become more and more pervasive and riddled with …
US Political Campaigns Targeted by Iranian Spear Phishing Attacks
Researchers at Recorded Future’s Insikt Group warn that the Iranian state-sponsored threat actor “GreenCharlie” is launching spear phishing …
Phishing Scammers Leverage Microsoft Dynamics 365 to Target US Government Contractors
Analysis of a phishing campaign targeting thousands of government contractors, dubbed “Operation Uncle Sam,” takes advantage of some …
Threat Actors Abuse URL Rewriting to Mask Phishing Links
Threat actors are abusing a technique called “URL rewriting” to hide their phishing links from security filters, according to researchers at …
Cybersecurity in 2024: Reflecting on the Past, Preparing for the Future
As Europe is returning from summer breaks, it is time to reflect on the first half of 2024 and look forward to the rest of the year.
The Long Road to Recovery Following a Ransomware Attack
When it comes to the duration of a ransomware attack and the subsequent recovery process, the numbers are staggering and vary wildly. Partly …
U.K. Management Almost Twice as Likely to Fall for Phishing Attacks Versus Entry-Level Employees
Highlights from a new survey focused on employee compliance reveals just how targeted and susceptible U.K. businesses are to phishing attempts.
Ransomware Group Known as ‘Royal’ Rebrands as BlackSuit and Is Leveraging New Attack Methods
The ransomware threat group formerly known as "Royal" has rebranded itself as BlackSuit and updated their attack methods, warns the FBI.
Is Disabling Clickable URL Links Enough?
Recently, we had a customer reach out to ask if disabling clickable uniform resource locator (URL) links in emails was enough protection by …
[PROVED] Unsuspecting Call Recipients Are Super Vulnerable to AI Vishing
Heads-up: I just proved that unsuspecting call recipients are super vulnerable to AI vishing
File-Sharing Phishing Attacks Increased by 350% Over the Past Year
File-sharing phishing attacks have skyrocketed over the past year, according to a new report from Abnormal Security.
Ransomware Payments Decline While Data Exfiltration Payments Are On The Rise
The latest data from Coveware shows a slowing of attack efficacy, a decrease in ransom payments being made, and a shift in initial access …
Latest Phishing Scam Uses Cross-Site Scripting Attack to Harvest Personal Details
Cross-Site Scripting (XSS) is alive and well, and used in attacks to obfuscate malicious links in phishing emails to redirect users to …
Employment Scams Continue to Target Job Seekers Via Phony Employment Offers
Threat actors continue to target job seekers with phony employment offers on job search platforms like Indeed, researchers at Bitdefender warn.
Real Social Engineering Attack on KnowBe4 Employee Foiled
DavidB, the KnowBe4 VP of Asia Pacific and Japan, recently experienced a sophisticated social engineering attack via WhatsApp.
Reflecting on KnowBe4's 5th Consecutive TrustRadius Tech Cares Award
For the fifth year in a row, we've been honored with the TrustRadius Tech Cares Award! This recognition is a testament to our unwavering …
Summer Lovin' or Summer Scammin'?
Summer. The season of sun, sand, and romance scams. As the weather heats up, so does the activity of romance scammers, who prey on the …
Chameleon Malware Poses as CRM App
Researchers at ThreatFabric warn that a phishing campaign is distributing the Chameleon Android malware by impersonating a Customer …
[FREE RESOURCE KIT] 2024 Cybersecurity Awareness Month Kit Now Available
Cyber risks abound, inside and out. Threats to your organization can come in many forms; from a suspicious email with a dodgy attachment to …
Attackers Abuse Google Drawings to Host Phishing Pages
Researchers at Menlo Security warn that a phishing campaign is exploiting Google Drawings to evade security filters.
Hacker Stories: A Facebook Physical Threat
Most people take a lot of measures to secure their online bank accounts, credit card accounts, retirement accounts and other financial …
A Whopping 33% of Young American Are Exposed to Political Lies on TikTok
Excellent reporting by the Wall Street Journal! They wrote about a disturbing trend. "Amid a deluge of election news and memes on TikTok, WSJ …
[WHOA] - This 'Unpatch Attack' Is A New One To Me!
In a startling revelation at Black Hat 2024, SafeBreach security researcher Alon Leviev demonstrated a critical vulnerability in Windows …
Not Just Us: North Korean Remote IT Fraudster Arrested in Tennessee
Just when we thought we had something special with our very own North Korean hacker, it turns out this type of fraud has made it to the …
New Phishing Campaign Targets Israeli Organizations To Deliver Malware
A new phishing campaign is targeting Israeli organizations to deliver the RHADAMANTHYS information-stealing malware, Cyber Security News …
SEC Report Provides Insight into Key Tronic Ransomware Costs Totaling Over $17 Million
The financial repercussions of the May 2024 ransomware attack on the electronics manufacturing services firm Key Tronic underscores just how …
2024 Phishing Insights: What 11.9 Million User Behaviors Reveal About Your Risk
Your secret weapon to combat cyber threats might be just under your nose! Cybercriminals continue to exploit vulnerabilities while upping …
62% of Phishing Emails Bypassed DMARC Checks in 1H of 2024
A report from Darktrace has found that 62% of phishing emails in the first half of 2024 were able to bypass DMARC verification checks in order…
“Pastejacking” Attacks Are Becoming a Thing (Because Users are Falling for Them)
New analysis shows users can be convinced to copy and paste malicious code on behalf of the attacker.
New Malvertising Campaign Impersonates Google Authenticator
Researchers at Malwarebytes spotted a malvertising campaign that abused Google Ads to target people searching for Google Authenticator.
AI Tools Have Increased the Sophistication of Social Engineering Attacks
The Cyber Security Agency of Singapore (CSA) has warned that threat actors are increasingly using AI to enhance phishing and other social …
KnowBe4 Honors the World Famous Hacker for the First National Social Engineering Day
On August 6th, 2024, we celebrate National Social Engineering Day – a new national day established by KnowBe4 and officially recognized by …
Creating a Big Security Culture With a Tiny Button
When it comes to creating a strong cybersecurity culture, one of the most powerful tools we have at our disposal is the Phish Alert Button …
Brand Impersonation of Microsoft Increases 50% in One Quarter
The use of the Microsoft brand in phishing attacks demonstrates both its widespread credibility as well as the continued success of attacks …
Phishing Attacks Continue to Leverage URL Shorteners to Obfuscate Malicious Links
Analysis of current phishing attacks by security researchers have uncovered an increase in the use of trusted shortlink services.
Prisoner Swap Includes Russian Hackers and KGB Assassin
Included among the U.S. prisoners being sent back to Russia in the swap are two prominent convicted hackers, both of whom were serving lengthy…
New Research: Smaller Companies Receiving Higher Rates Of Phishing Emails
Researchers at Barracuda have found that smaller companies tend to receive a higher rate of phishing attacks spread across the organization, …
Global Cyber Attacks See Highest Increases in the Last Two Years
New analysis of Q2 2024 cyber attacks shows the number of attacks experienced weekly by organizations globally is on the rise.
KnowBe4 Named a Leader in the Summer 2024 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR) Software
We are excited to announce that KnowBe4 has been named a leader in the Summer 2024 G2 Grid Report for Security Orchestration, Automation, and …
Half of Travel-Themed Spam Emails Are Scams
Researchers at Bitdefender have found that half of all travel-themed spam emails contain scams.
The First Half of 2024 Results in More Than 1 Billion Data Breach Victims
New data shows that cyber attacks have resulted in double the number of data breaches in 2024 than throughout all of 2023.
KnowBe4 Named a Leader in the Summer 2024 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares security awareness training (SAT) …
Organizations Prepare for More Evolved AI-Based Cyber Attacks as Deepfakes Become Top Concern
New data on how the threat of AI in cyber crime is being seen as a growing risk provides insight into how organizations are shifting from …
New Phishing Kit Uses Voice Call Generator to Impersonate Spanish Banks
A new cybercriminal group is selling “a sophisticated AI-powered phishing-as-a-service platform” that targets 36 Spanish banks, according to …
Dark Angels Ransomware Group Scores Record-Breaking $75 Million Payday
In the ever-evolving world of cybercrime, ransomware attacks continue to be a lucrative business for cybercriminals.
Scammers Exploit Interest in Generative AI Tools
Researchers at Palo Alto Networks’s Unit 42 are tracking phishing attacks exploiting interest in generative AI tools. The researchers observed…
IoT: Internet of Threats?
The Internet of Things (IoT) has slowly but surely weaved its way into our homes and places of work. From smart homes to industrial control …
The 2024 Olympics Offers Plenty of Opportunity For Online Scammers
Fortinet’s Threat Intelligence Report covering the Paris Olympics provides some very detailed coverage of how threat actors are taking …
QR Code Phishing is Still on the Rise
Organizations need to be aware of the threat posed by QR code phishing (quishing), according to researchers at Trend Micro.
Nearly All Ransomware Attacks Now Include Exfiltration of Data…But Not All Are Notified
Organizations are falling victim to ransomware attacks where data is stolen, but the victim isn’t being told about it. I have a theory as to …
Roger’s Hacking Stories
In this post, I'll share two fascinating hacking stories I've experienced: one involving a sophisticated scam that targeted a major U.S. …
How The Whole World Now Knows About Fake North Korean IT Workers
Wow. Last week's blog post went viral, hitting major media outlets and receiving over 100K hits in just a few days. Most responses, coming …
New Phishing Scam Leverages Chat To Add Credibility And Ensure Success
A new phishing scam is leveraging trusted aspects of ecommerce to make their scams look legitimate.
Phishing Campaigns Continue To Exploit CrowdStrike Outage
As expected, threat actors are taking advantage of the global IT outage caused by a faulty CrowdStrike update last Friday, SC Media reports.
Russian Super-Threat Group Fin7 Comes Back from the Dead
Declared “dead” by the U.S. Attorney’s Office in 2023, the Russian cyber crime group Fin7 is impersonating some of the top global brands.
Your KnowBe4 Fresh Content Updates from July 2024
Check out the 26 new pieces of training content added in July, alongside the always fresh content update highlights, events and new features.
Your KnowBe4 Compliance Plus Fresh Content Updates from July 2024
Check out the July updates in Compliance Plus so you can stay on top of featured compliance training content.
North Korean Fake IT Worker FAQ
Frequently Asked Questions About KnowBe4's Fake IT Worker Blog July 23, 2024, I wrote a blog post about how KnowBe4 …
Phishing Campaigns Abuse Cloud Platforms to Target Latin America
Several threat actors are abusing legitimate cloud services to launch phishing attacks against users in Latin America, according to Google’s …
Is Your Bank Really Calling? How to Protect Yourself from Financial Impersonation Fraud
Protecting your financial information has never been more crucial. With the rise of sophisticated scams, it's becoming increasingly difficult …
Crypto Data Breach Continues to Fuel Phishing Scams Years Later
According to security researchers at Cisco Talos, emails impersonating legitimate officers at the Cyprus Securities and Exchange Commission …
How a North Korean Fake IT Worker Tried to Infiltrate Us
Incident Report Summary: Insider Threat TLDR: KnowBe4 needed a software engineer for our internal IT AI team. We posted the job, received …
[Security Masterminds Podcast] Securing Software Over 50 Years: Reflections from an Industry Veteran
Does the challenge of keeping up with cybersecurity trends sound familiar? You may have been told to update your antivirus software and hope …
Phishing Attacks Will Likely Follow Last Week’s Global IT Outage
Organizations should expect to see phishing attacks exploiting the global IT outage that occurred last Friday, the Business Post reports.
CrowdStrike Phishing Attacks Appear in Record Time
I have been the CEO of an anti-virus software developer. We had a special acronym for catastrophic events like this, a so-called "CEE". As…
78% of Organizations Are Targets of Ransomware Attacks Two or More Times in Twelve Months
New data puts the spotlight on the frequency and impact of modern ransomware attacks, highlighting the overconfidence organizations are …
CISA’s Red Team Exercise Shows Value of Phishing, but Misses the Best Recommendation
Phishing is used to completely compromise the victim’s environment after other repeated methods failed.
Cyber Threats Targeting the 2024 Paris Olympics
Our friends at the CyberWire reported: "ZeroFox and Fortinet have both published reports on threats facing the 2024 Olympics in Paris. ZeroFox…
Change Healthcare Ransomware Attack May Cost Nearly $2.5 Billion
The ransomware attack against UnitedHealth Group’s Change Healthcare platform is expected to cost the company up to $2.45 billion, more than a…
Chile Leads Latin America With New Cybersecurity Governance
Chile took a major step toward a more resilient cyber landscape for its citizens and the Latin American region on Tuesday, March 26, 2024, …
7 in 10 Organizations Experienced a Business Email Compromise Attack in the Last 12 Months
Despite ransomware getting the lion’s share of the tech pub headlines, business email compromise (BEC) attacks are alive and well… and having …
From Reactive to Proactive: Cyber Insurance is Driving Optimal Security Investments for Organizations
New data shows that only 3 percent of organizations are solely relying on their current cyber defenses when adding on cyber insurance, …
Phishing Continues to Be the Primary Entry to Ransomware Attacks
Phishing remains a top initial access vector for ransomware actors, according to researchers at Cisco Talos. The threat actors often use …
Crack the Code on Ransomware: Empowering Your Last Line of Defense
Cybercriminals are maximizing the potential damage to your organization to boost their profits. A staggering 91% of reported ransomware …
New Ransomware Threat Group Calls Attack Victims to Ensure Payments
Analysis of new ransomware group Volcano Demon provides a detailed look into how and why calling victims ups the chances of ransomware payment.
Malvertising Campaign Impersonates Microsoft Teams
Researchers at Malwarebytes warn that a malvertising campaign is targeting Mac users with phony Microsoft Teams ads. The ads are meant to …
[NEW FREE TOOL]: Reveal Your Network's Hidden Weaknesses with KnowBe4's BreachSim Data Exfiltration Simulator
As cyber threats evolve, the target has become crystal clear: your data. A staggering 90% of ransomware attacks now include a data …
SEC Fines Publicly Traded Company $2.125 Million For Negligence Before, During, and After a Ransomware Attack
According to the filing, the organization in question failed to devise controls to adequately detect, respond to, and disclose an attack that …
Espionage-Intent Threat Groups Are Now Using Ransomware as a Diversion Tactic in Cyberattacks
A new report focused on cyber espionage actors targeting government and critical infrastructure sectors highlights the strategic use of …
IRS Warns of Phishing Attacks Targeting Car Dealerships
The US Internal Revenue Service (IRS) has issued an advisory warning of phishing campaigns targeting car dealerships. The IRS says car dealers…
Phishing Attacks Against State and Local Governments Are Surging
Researchers at Abnormal Security have observed a 360% increase in phishing attacks against state and local government entities over the past …
Ransomware Attacks on Healthcare Is Costing Lives
Ransomware is more prolific and expensive than ever. Depending on the source you read, the average or median ransomware payment was at least …
Russian Spear Phishing Campaigns Target NATO Entities
Researchers at Mandiant (part of Google Cloud) warn that Russian government threat actors continue to target NATO member countries with spear …
From Policy to Practice in Security Culture: What Security Frameworks Recommend
Recently I had to prepare for a governance, risk and compliance conference. I promptly realized that although I used to be quite immersed in …
New Phishing Platform Targets Microsoft 365 Accounts at Financial Firms
Analysis of the latest phishing-as-a-service (PhaaS) platform ONNX Store highlights just how successful these platforms can be.
Amazon-Related Scams Spike Ahead of Prime Day
Researchers at Check Point observed more than a thousand newly registered malicious or suspicious web domains related to Amazon last month. …
Phishing Attacks Target High Profile YouTube Accounts
Researchers at ESET warn of phishing attacks that are attempting to hack high-profile YouTube channels in order to spread scams or malware.
The Importance of Security Culture: When Telecom Giants Resort to Malware
I recently read a story about a South Korean telecom company that pushed out malware to over 600,000 of its customers who were using torrents …
Travelers Beware: Booking.com Warns of Increases in AI-Enabled Travel Scams
In an interview at the Collision technology conference in Toronto, Booking.com’s CISO sounds the alarm on what she calls “supercharged …
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human …
State-Sponsored Phishing Campaigns Target 40,000 VIP Individuals
Researchers at Menlo Security discovered three state-sponsored phishing campaigns that have targeted 40,000 important individuals over the …
Don't Fall for It: How to Spot Social Media Job Scams a Mile Away
As social media becomes more intertwined with our daily routines, cybercriminals are using it to trick people with fake job offers. What are …
Phishing Attacks Themed Around Popular Weight Loss Drugs Increase 183%
As popularity grows for these proven methods of weight loss, scammers have taken note and have placed a significant focus on separating …
New “Paste and Run” Phishing Technique Makes CTRL-V A Cyber Attack Accomplice
A new phishing campaign tries to trick email recipients into pasting and executing malicious commands on their system that installs DarkGate …
Sextortion Epidemic Targeting Teenagers Calls for Urgent Action
A few weeks ago I was privileged to visit the 8th grade of a high-school here in Cape Town and talk to the students about cybersecurity, …
Ransomware Attack on U.K. Health Service Laboratory Disrupts Major London Hospital Services
What likely started as a quick ransomware “smash and grab” has turned into a headline case resulting in responses from both U.K. and U.S. law …
Hacked Customer Support Portal Being Used to Send Phishing Emails
A hacked customer support portal belonging to router manufacturer Mercku is being used to respond to customer queries with phishing emails, …
New Malware Campaign Impersonates AI Tools To Trick Users
Researchers at ESET warn that malvertising campaigns are impersonating AI tools to trick users into installing malware. The Rilide …
The Curious Case of the Payroll Pilfering
In a world where cyber espionage has become as common as a rainy day in London, the recent events surrounding the UK armed forces' payroll …
Your KnowBe4 Compliance Plus Fresh Content Updates from June 2024
Check out the June updates in Compliance Plus so you can stay on top of featured compliance training content.
KnowBe4 Recognized as Cyber Security Educator of the Year at IT Europa Awards 2024
It's a great honor for KnowBe4 to be named the Cyber Security Educator of the Year at the prestigious IT Europa Channel Awards 2024.
Your KnowBe4 Fresh Content Updates from June 2024
Check out the 29 new pieces of training content added in June, alongside the always fresh content update highlights, events and new features.
TeamViewer Corporate Network Breached in Alleged APT Attack
In a concerning development, TeamViewer, one of the world's leading remote access software providers, has disclosed a cyber attack that …
Russian Threat Actor Launches Spear Phishing Attacks Against French Diplomats
France’s cybersecurity agency ANSSI has issued an alert outlining a Russian spear phishing campaign targeting French diplomats, the Record …
FBI Warns of Phishing Campaign Targeting the Healthcare Industry
The US FBI and the Department of Health and Human Services (HHS) have released a joint advisory warning of a social engineering campaign …
Cybercriminals Set Sights on Digital Identities of Singapore Citizens
Singapore has become the latest target for cybercriminals looking to steal digital identities and exploit them for nefarious purposes.
The Double-Edged Sword of AI: Empowering Cybercriminals and the Need for Heightened Cybersecurity Awareness
The BBC recently reported that Booking.com is warning that AI is driving an explosion in travel scams. Up to 900% in their estimation - making…
Simulated Phishing Tests Matter
If you had to choose between regular cybersecurity training and simulated phishing testing, the data shows you should choose simulated …
Mexican Organizations Under Attack from Specialized Cyber Criminals
A crafty group of cybercriminals has been relentlessly pursuing Mexican banks, cryptocurrency platforms and other organizations in an extended…
Phishing Attacks in the UK Have Surged
Over 11 million phishing attacks have been reported to the UK’s Suspicious Email Reporting Service (SERS) over the past year, according to new…
FREE Resource Kit for Ransomware Awareness Month in July
We’re here to help you and your users stay secure from the scourge of ransomware for Ransomware Awareness Month this July with a kit full of …
Balancing Act: The European Union's AI Act and the Quest for Responsible Innovation
The current landscape of artificial intelligence (AI) bears a striking resemblance to the early days of the internet. Just as the internet was…
BEC Attacks Accounted for More Than One in Ten Social Engineering Attacks in 2023
A new report from Barracuda has found that email conversation hijacking attacks have risen by 70% since 2022. Additionally, business email …
My Hacker Story: A Cautionary Tale of Intern Antics and Cultural Learnings
My hacker story does not paint me in the best light, and it is not intended to. I am a firm believer in sharing one's mistakes and being open …
The Indispensable World of Red Teaming
In this mad, mad world of breaches, organizations are scrambling to keep their heads above water. It's like trying to navigate a minefield …
Vacation-Themed Scams Are Spiking
Scammers are now impersonating legitimate services like Booking.com and Kayak to target people planning their summer vacations. One out of …
Happy 1st Birthday to Our KnowBe4 Community!
Happy 1st birthday to our KnowBe4 Community! We’re so excited to celebrate our community's first anniversary. It’s been filled with so many …
Brazilian Entities Increasingly Targeted by Nation-State Phishing Attacks
Mandiant has published a report looking at cyber threats targeting Brazil, finding that more than 85% of government-backed phishing activity …
The Overlooked Truth: User Experience in Cybersecurity
We live in a world where the term "cybersecurity" tends to make folks either shiver with anxiety or yawn with boredom. The narrative has …
No Politician Too Small: School Board Candidates Targeted By Phishing and BEC Scams
Cybercriminals are broadening their targets to include even local political candidates, as an escalating series of phishing attacks was …
Phishing Campaign Abuses Windows Search to Distribute Malware
Researchers at Trustwave warn that a phishing campaign is distributing malware via HTML attachments disguised as invoices. Notably, the HTML …
Microsoft and KnowBe4 Collaborate on Ribbon Phish Alert Button for Outlook
Increasing phishing attacks are a constant threat to organizations, making it crucial for users to report suspicious emails.
Unmasking the Threat: Why Phishing Scams are Surging in Japan
Japan has a large number of Forbes Global 2000 corporations--more than the UK, Germany, and France combined. Despite this economic strength, …
Phishing Campaign Targets Job Seekers With WARMCOOKIE Backdoor
A phishing campaign is impersonating recruiting firms to target job seekers with a new strain of malware, according to researchers at Elastic …
The Global Reach of Cyber Threats: Why Security Awareness Training is More Important Than Ever
Based on news cycles within cybersecurity, it's easy to fall into the trap of thinking that threats only come from certain parts of the world …
Cybercriminals Use New V3B Phishing Kit to Mimic 54 Different Banks in the European Union
A new phishing-as-a-service toolkit that leverages credential interception and anti-detection capabilities has put EU banks at severe risk of …
Phishing With Deepfakes for HK$200 Million
My hacker story occurred not too long ago at the Hong Kong office of an undisclosed multinational corporation. The hackers pulled off a …
New Research Shows An Alarming Trend of Phishing Attacks Doubling For US and European Organizations
Cybercriminals never sleep, and their aim keeps getting better. According to new research from Abnormal Security, phishing attacks targeting …
Beware: Major AI Chatbots Now Intentionally Spreading Election Disinformation
Just when you thought the disinformation landscape couldn't get any worse, an alarming new report from Democracy Reporting International …
Sinister "More_eggs" Malware Cracks Into Companies by Targeting Hiring Managers
Job seekers, beware - cybercriminals have a nasty new way to slide their malicious code on corporate networks. Researchers have uncovered a …
DarkGate Malware Being Spread Via Excel Docs Attached To Phishing Emails
A phishing campaign is spreading the DarkGate malware using new techniques to evade security filters, according to researchers at Cisco Talos.
New HR-Themed Credential Harvesting Phishing Attack Uses Legitimate Signature Platform Yousign
A new phishing campaign is exploiting the eSignature platform Yousign.
Bruce Schneier: "AI Will Increase the Quantity—and Quality—of Phishing Scams"
Wow. It does not happen often that the godfather of infosec comes out this strong about phishing risks. He co-published new research in the …
Everything You Can Do to Fight Social Engineering and Phishing
Social engineering and phishing are not just IT buzzwords; they are potent threats capable of devastating damage to your organization.
[New Feature] Find Out if They've Got a Bad Reputation in Record Time with PhishER Plus Threat Intel
The PhishER Plus platform just got smarter with the addition of the new PhishER Plus Threat Intel feature that integrates web reputation data …
Nearly Three-Quarters of Organizations Were the Target of Attempted Business Email Compromise Attacks
New data highlights just how dangerous Business Email Compromise attacks are.
Minnesotans Targeted by Scammers With Phony Arrest Warrants
The Minnesota Judicial Branch has issued an advisory warning that scammers are messaging Minnesotans with phony arrest warrants for missing …
Fighting Phishing: Everything You Can Do to Fight Social Engineering and Phishing
I have created a comprehensive webinar, based on my recent book, “Fighting Phishing: Everything You Can Do to Fight Social Engineering and …
Breach or Bluff: Cyber Criminals' Slippery Tactics
When the news first broke about a potential data breach at Ticketmaster, the details were murky. The Department of Home Affairs confirmed a …
Social Engineering Scams Can Come in the Mail, Too
Social engineering scams can come through any communications channel (e.g., email, web, social media, SMS, phone call, etc.). They can even …
“Operation Endgame” Ends with the Arrest of 4 Cybercriminal Suspects and 100 Servers
Coordinated efforts between law enforcement agencies across nine countries has resulted in a major disruption of a threat group’s malware and …
26% of Global Organizations Lack Security Training Programs
More than a quarter (26%) of organizations around the world provide no security awareness training for their employees, according to a survey …
Best Buy/Geek Squad Impersonation Scams Surged in 2023
The US Federal Trade Commission (FTC) has found that Best Buy, and its tech support subsidiary Geek Squad, were the most commonly impersonated…
Email Compromise Continues to Dominate as Top Threat Incident Type as Tactics Evolve
As email compromise attacks increase, analysis of tactics provides context on how organizations need to evolve their defenses.
Enhance NIS2 Compliance: Elevate Your Cybersecurity with Awareness & Culture Before The Deadline
The NIS2 Directive, also known as the Network and Information Security Directive, is a crucial piece of legislation designed to enhance …
[NEW RESEARCH]: KnowBe4’s 2024 Phishing by Industry Benchmarking Report Reveals that 34.3% of Untrained End Users Will Fail a Phishing Test
The prevalence of cyber crime continues to soar, victimizing individuals in both their work and private lives. Cybercriminals are indiscriminate, …
Russia’s Military Intelligence Service Launches Spear Phishing Attacks
Researchers at Recorded Future warn that BlueDelta, a threat actor tied to Russia’s GRU, is launching spear phishing attacks against European …
New Transparent Phishing Attacks Leverage Cloudflare Worker Serverless Computing
An increasing number of phishing campaigns from several threat groups are being tracked as they leverage legitimate Cloudflare services as …
Your KnowBe4 Compliance Plus Fresh Content Updates from May 2024
Check out the May updates in Compliance Plus so you can stay on top of featured compliance training content.
The Hard Evidence That Phishing Training and Testing Really Works
Security awareness training (SAT) and simulated phishing works to significantly reduce cybersecurity risk. We have the data, customer …
91% of Every Ransomware Attack Today Includes Exfiltrating Your Data
New insight into ransomware attacks show that cyber attacks are a top concern for organizations – with many not aware they were a victim until…
Your KnowBe4 Fresh Content Updates from May 2024
Check out the 60 new pieces of training content added in May, alongside the always fresh content update highlights, events and new features.
Cybercriminals Target Hajj Pilgrims
Criminals are launching a variety of scams targeting Muslims around the world who are planning on making the Hajj pilgrimage to Mecca, …
Criminals Abuse Cloud Storage Platforms to Host Phishing Sites
Threat actors are abusing cloud storage platforms to host phishing sites that can more easily evade detection by security scanners, according …
Threat Actor Void Manticore Uses Cyber Weapon “Wipers” to Destroy Data and Systems
This Pro-Hamas hacktivist group has updated their payload arsenal to include updated versions of their BiBi Wiper malware, and two new wiper …
KnowBe4 Free Tools Now Available On CISA’s Website
We are big fans of the U.S. Cybersecurity Infrastructure Security Agency (CISA), whose informal slogan of “An organization so committed to …
China Threat Actor Targeting African and Caribbean Entities With Spear Phishing Attacks
The China-aligned threat actor “Sharp Dragon” is launching spear phishing attacks against government entities in African and Caribbean …
[FedRAMP Phishing Rule]: "Users are the last line of defense and should be tested."
If you want to sell cloud-based software to the U.S. Government, you need to be FedRAMP authorized. This is what they state in their Program …
CISA Releases Cybersecurity Resources for High-Risk Communities
Working to ensure all communities within the United States are educated and prepared, the Cybersecurity and Infrastructure Security Agency …
As Many as 1 in 7 Emails Make it Past Your Email Filters
Fluctuations in consecutive quarterly reports demonstrates that organizations should be worried that their cyber defenses may not be strong …
New Research Finds Phishing Scams Targeting Popular PDF Viewer
Several phishing campaigns are targeting users of the Foxit PDF Reader, according to researchers at Check Point. Foxit is a popular …
From Boredom to Engagement: Gamification in Cybersecurity Awareness
As someone who can barely keep up when my 10-year-old shows me around his Minecraft worlds, I was a bit apprehensive about writing a review of…
Secure Your Site: Learn from the Top 10 Cybersecurity Experts of 2024
Companies have needed a website for the last 25 years at least. But where do you host your site? The techies at HostingAdvice decided to …
UK Cybersecurity Org Offers Advice for Thwarting BEC Attacks
The UK’s National Cyber Security Centre (NCSC) has issued guidance to help medium-sized organizations defend themselves against business email…
Don't Let Criminals Steal Your Summer Fun
Summer has finally arrived in certain parts of the world, and with it come many exciting events — from the grandeur of the Olympics to the …
Malicious Use of Generative AI Large Language Models Now Comes in Multiple Flavors
Analysis of malicious large language model (LLM) offerings on the dark web uncovers wide variation in service quality, methodology and value –…
Announcing KnowBe4 Student Edition: Cybersecurity Education Tailored for the Next Generation
I recently heard another heartbreaking story of students who were scammed out of financial aid by a phishing attack. We have also heard …
The Shadow War: Cognitive Warfare and the Politics of Disinformation
For better or for worse, we live in a world that is an anarchy of nations. Over the last few decades, warfare has transcended traditional …
Newly Updated Grandoreiro Banking Trojan Distributed Via Phishing Campaigns
Researchers at IBM X-Force are tracking several large phishing campaigns spreading an updated version of the Grandoreiro banking trojan.
Cyber Insurance Claims Rise Due To Phishing and Social Engineering Cyber Attacks
New data covering cyber insurance claims through 2023 shows claims have increased while reaffirming what we already know: phishing and social …
New Threat Report Finds Nearly 90% of Cyber Threats Involve Social Engineering
Analysis of over 3.5 billion attacks provides insight into where threat actors are placing their efforts and where you should focus your cyber…
Verizon: The Human Element is Behind Two-Thirds of Data Breaches
Despite growing security investments in prevention, detection and response to threats, users are still making uninformed mistakes and causing …
8 out of 10 Organizations Experience a Cyber Attack and Attribute Users as the Problem
Regardless of whether your environment is on-premises, in the cloud or hybrid, new data makes it clear that users are the top cybersecurity …
Scam Service Attempts to Bypass Multi-factor Authentication
A scam operation called “Estate” has attempted to trick nearly a hundred thousand people into handing over multi-factor authentication codes …
Black Basta Ransomware Uses Phishing Flood to Compromise Orgs
Rapid7 reports an interesting social engineering scheme that easily bypasses content filtering defenses and creatively uses a fake help desk …
Phishing and Pretexting Dominate Social Engineering-Related Data Breaches
New data shows that despite the massive evolution of the cybercrime economy, threat actors are sticking with the basics in social engineering …
FBI Warns of AI-Assisted Phishing Campaigns
The US Federal Bureau of Investigation’s (FBI’s) San Francisco division warns that threat actors are increasingly using AI tools to improve …
Attackers Leveraging XSS To Make Phishing Emails Increasingly Evasive
Attackers are exploiting Reflected Cross-Site Scripting (XSS) flaws to bypass security filters, according to a new report from Vipre. This …
“Unknown” Initial Attack Vectors Continue to Grow and Plague Ransomware Attacks
Trend analysis of ransomware attacks in the first quarter of this year reveals a continual increase in the number of "unknown" initial attack …
Alert: Nova Scotians Hit by Surge of Sophisticated Spear Phishing Scams
The Royal Canadian Mounted Police (RCMP) in Nova Scotia is warning of spear phishing attacks that impersonate company managers. The scammers …
New Research: Number of Successful Ransomware Attacks Rise 29% in a Just One Year
New analysis of Q1’s ransomware attacks uncovers a single group responsible for the majority and discusses what makes them so successful.
Reality Hijacked: Deepfakes, GenAI, and the Emergent Threat of Synthetic Media
"Reality Hijacked" isn't just a title—it's a wake-up call. The advent and acceleration of GenAI is redefining our relationship with 'reality' …
[Beware] Ransomware Targets Execs' Kids to Coerce Payouts
Just when you think bad actors cannot sink any lower, they find a way to. In a recent chilling evolution of ransomware tactics, attackers are …
Google’s Multi-Party Approval Process Is Great, but Not Unphishable
Like most observers, I celebrated Google’s recent announcement on April 9th about new multi-party approvals for a handful or so of common …
Ransomware Detection Time Shortens by 44% as Organizations Attempt to Keep Up with Attackers
New data shows organizations are improving their ability to detect and respond to ransomware attacks, but is it fast enough to make a …
Phishing-as-a-Service Platform LabHost Disrupted by Law Enforcement Crackdown
One of the largest phishing-as-a-service platforms, LabHost, was severely disrupted by law enforcement in 19 countries during a year-long …
Digital Doppelgängers: AI-Generated Celeb Fashion Takes Over the Met Gala on Social Media
The Met Gala, fashion's biggest night, was not just the A-list attendees who stole the spotlight—digital imposters in the form of AI-generated…
Arizona Election Workers Battle Against Deepfake Threats in New AI Defense Drill
In the quest to secure the integrity of elections, Arizona election workers have taken a groundbreaking step by participating in a …
[Must Read] How Boeing Battled a Whopping $200M Ransomware Demand
Boeing recently confirmed that in October 2023, it fell victim to an attack by the LockBit ransomware gang, which disrupted some of its parts …
[Breaking] The News Is Increasingly Broken. Surge Of Inaccurate AI News Stories
Keeping up to date what is happening is crucial in IT, but the reliability of the news you consume is facing a growing threat.
Phishing Reports in Switzerland More Than Doubled Last Year
Switzerland’s National Cyber Security Centre (NCSC) received more than 30,000 reports of cyber incidents in the second half of 2023, more than…
9 in 10 Organizations Paid At least One Ransom Last Year
New analysis of cyber attacks shows ransomware attacks are running far more rampant than previously thought, with half of organizations …
KnowBe4 Earns Multiple 2024 Best Of Awards From TrustRadius
KnowBe4 is proud to be recognized by TrustRadius for our Security Awareness Training and PhishER platforms.
Verizon: Nearly 80% of Data Breaches Involve Phishing and the Misuse of Credentials
Innovative analysis of data breaches shows which attack vectors are being used and how they’re enabled, highlighting the roles phishing and …
Credential-Harvesting Campaign Impersonates Fashion Retailer Shein
A phishing campaign is impersonating fashion retailer Shein in an attempt to steal users’ credentials, according to researchers at Check Point.
The Education Sector Experienced the Highest Number of Data Breaches in 2023
New data from Verizon makes it clear that the Education sector is under attack, but also breaks down which threat actions and patterns are …
U.S. Government Warns of North Korean Spear-Phishing Campaigns
The North Korean state-sponsored threat actor Kimsuky is launching spear phishing attacks against individuals working at think tanks and …
Introducing The New KnowBe4.com
I'm excited to unveil our newly redesigned website at knowbe4.com! The team has worked hard to create a sleek, modern design with improved …
Verizon: The Percentage of Users Clicking Phishing Emails is Still Rising
The long-awaited annual Verizon Data Breach Investigations Report is out, and it’s made very clear that users continue to be a problem in …
Protecting Your Digital Footprint: The Dangers of Sharing Too Much on Social Media
For most folks, social media has become integral to their daily lives in today's hyperconnected world. They use platforms like Facebook, …
Analysis Shows 2023 to be “Worst Year for Phishing on Record”
Newly-released data highlights our worst fears about the prevalence of phishing, and some glimmer of hope that the good guys may be winning …
Is RogerLovesTaco$24 a Strong Password?
Is "RogerLovesTaco$24" a strong password? No! Everyone has a ton of passwords. They should be strong and unique for every site and service you…
Navigating the Masquerade: Recognizing and Combating Impersonation Attacks
With all great power, there comes an equal potential for misuse. Among the sophisticated arsenal of threat actors, impersonation attacks have …
[CASE STUDY] Healthcare Organization Hardens Employee Defenses Against Insidious Callback Phishing Attacks
A major U.S. healthcare provider significantly reduced their employees' susceptibility to callback phishing attacks after using KnowBe4's …
North Korean Threat Actors Target Software Developers With Phony Job Interviews
Suspected North Korean threat actors are attempting to trick software developers into downloading malware during phony job interviews, …
FBI Warns of Verification Scams Targeting Dating Site Users
The US Federal Bureau of Investigation (FBI) has issued an advisory warning of a scam campaign targeting users of online dating platforms. The…
How New College Graduates Can Avoid Increasingly Personalized Job Scams
For many fresh out of college, the drive to land that first professional role is a top priority. Yet, new graduates can be exposed to …
Phishing Failures: How Not to Phish Your Users
This blog was co-written by Javvad Malik and Erich Kron. Let’s dive into the cautionary world of phishing simulations gone wrong. You know, …
Targeted Smishing Attacks by Threat Group “The Com” On The Rise
Cyber activity by the group "The Com," which leverages (SIM) swapping, cryptocurrency theft, swatting, and corporate intrusions, is increasing.
The Art of Huh?
One of the best things you can teach yourself, your family, and your organization is how to recognize the common signs of phishing and how to …
Phishing Campaigns Spoof the U.S. Postal Service
Researchers at Akamai have found that phishing sites impersonating the U.S. Postal Service get as much traffic as the real USPS website.
Your KnowBe4 Compliance Plus Fresh Content Updates from April 2024
Check out the April updates in Compliance Plus so you can stay on top of featured compliance training content.
How an Athletic Director Exploited AI to Frame a Principal with Fabricated Racist Comments
In an unsettling turn of events, a high school athletic director in Maryland is accused of using artificial intelligence (AI) in a morally …
US Justice Department Accuses Iranian Nationals of Launching Spear Phishing Attacks
The US Department of Justice has indicted four Iranian nationals for allegedly launching spear phishing attacks against the US government and …
Next Week is World Password Day!
May 2nd is World Password Day. Despite the computer industry telling us for decades that our passwords will soon be gone, we now have more …
Your KnowBe4 Fresh Content Updates from April 2024
Check out the 33 new pieces of training content added in April, alongside the always fresh content update highlights, events and new features.
AI-Assisted Phishing Attacks Are on the Rise
Threat actors are increasingly using generative AI tools to improve their phishing campaigns, according to a new report from Zscaler.
New Report Finds That 27% of Small Businesses Would Be Put Out of Business By A Cyber Attack
According to the U.S. Chamber of Commerce, the pressure is mounting on small and medium businesses (SMBs), as they must get their cyber …
Phishing Campaign Exploits Nespresso Domain
Attackers are launching phishing campaigns using an open-redirect vulnerability affecting a website belonging to coffee machine company …
Global Optics Provider Hit with Ransomware Attack and a $10M Ransom
Global optics manufacturer Hoya had business operations at its headquarters and several business divisions impacted and is now facing a “No …
Level Up Your Users’ Cybersecurity Skills with 'The Inside Man: New Recruits’
We’re thrilled to announce our newest addition to our ModStore’s already brimming collection of games with a new offering based on our …
Environmental Sustainable Training: KnowBe4's Commitment to a Greener Earth
KnowBe4 is committed to sustainability and helping protect the environment, as evidenced by our initiatives such as our public commitment to …
USPS Surges to Take Top Spot as Most Impersonated Brand in Phishing Attacks
New data shows phishing attacks are deviating from the traditional focus on technology and retail sectors and are opting for alternate brands …
[NEW GAME] The Inside Man: New Recruits Game
We released a new game, now available on the KnowBe4 Modstore. I played it myself and this is recommended for all Inside Man fans! "Mark …
4 out of 5 of Physicians Were Impacted by February’s Cyber Attack on Change Healthcare
A new survey of physicians details the devastating impact of the Change Healthcare cyber attack on the healthcare sector.
Kudos! CEO Reveals He Got Phished
The other day I was participating in a company’s employee meeting when the CEO revealed he had been “caught” that morning by a real phishing …
Half of U.K. Businesses Experienced a Security Breach or Cyber Attack in the Last 12 Months
Analysis of cyber attacks targeting U.K. organizations highlights the effectiveness of social engineering attacks and the fact that businesses…
Russian Threat Actor FIN7 Targeting the Automotive Industry with Spear Phishing Attacks
The cybercriminal threat actor FIN7 is launching spear phishing attacks against the automotive industry in the United States, according to …
LastPass Warns of Deepfake Phishing Attempt
LastPass has warned that one of its employees was targeted by a social engineering attack that used an audio deepfake that impersonated the …
AI Voice Cloning and Bank Voice Authentication: A Recipe for Disaster?
New advancements in generative AI voice cloning come at a time when banks are looking for additional ways to authenticate their customers – …
KnowBe4 Named a Leader in the Spring 2024 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR) Software
We are excited to announce that KnowBe4 has been named a leader in the Spring 2024 G2 Grid Report for Security Orchestration, Automation, and …
Phishing Frenzy: Microsoft and Google Most Mimicked Brands in Cyber Scams
Microsoft and Google were the most frequently impersonated brands in phishing attacks during the first quarter of 2024, according to a report …
Cisco Calls Out Organizations As Being “Overconfident and Unprepared” for Cyber Attacks
In a new report, Cisco says the cyber readiness of organizations is lacking despite having experienced multiple cyber attacks within the last …
KnowBe4 Named a Leader in the Spring 2024 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares security awareness training (SAT) …
[WARNING] FBI Issues Alert on Major Phishing Campaign That Impersonates US Toll Services
The FBI has issued an alert warning of a widespread SMS phishing (smishing) campaign targeting people in several US states with phony notices …
You Really Are Being Surveilled All the Time
“If the product is free, you are the product!” No truer words have ever been spoken. But in today’s internet-connected, ad-everywhere world, …
I don't have to say it, do I?
So today, news broke that Iran has sent dozens, if not more than 100 drones to Israel in a direct attack. Discussion on Twitter also claim …
[Heads Up] Global Cybercrime Hotspot Countries Revealed: Secure Your Defenses
In a groundbreaking study that spanned three years, an international research team, including experts from the University of Oxford and UNSW …
State-Sponsored Disinformation Campaigns Targeting Africa Driving Instability And Violence
A shocking report shows how email-based disinformation campaigns can have material real-world impacts to the citizens in the targeted …
U.S. Department of Health Alert: Hackers are Targeting IT Help Desks at Healthcare Organizations
A new sector alert published by the U.S. Department of Health and Human Services outlines new attacks in which social engineering is used to …
Cyber Attacks Could Cause Global Bank Runs
The International Monetary Fund (IMF) has warned that severe cyber attacks against financial institutions could lead to major bank runs and …
UK Councils Under Cyber Attack: The Urgent Need for a Culture of Cybersecurity and Resilience
The very fabric that stitches our society together — our councils and local governing bodies — is under a silent siege from cyber attacks. The…
Yesterday, in DC, I was given the Holland on the Hill Freddy Heineken Award
The Holland on the Hill Freddy Heineken Award honors an entrepreneur who has made a substantial and positive contribution to the US-Dutch …
Water Facilities Compromised By Iranian Threat Actors
In December 2023, a joint alert was issued by the FBI, CISA, NSA, EPA, and INCD regarding Iranian cyber actors known as "CyberAv3ngers" linked…
Top Tax Scams of 2024 Your Organization Should Watch Out For
As the April 15, 2024 filing deadline approaches, tax scammers are working overtime to take advantage of rushed or stressed taxpayers.
Malvertising Campaigns Surged in 2023
Researchers at BlueVoyant observed a 50% increase in large-scale malvertising campaigns in 2023 compared to 2022.
Critical Improvements To The Seven Most Common Pieces of Cybersecurity Advice
I have been in the cybersecurity industry for over 35 years and I am the author of 14 books and over 1,400 articles on cybersecurity.
New Phishing-as-a-Service (PhaaS) platform, 'Tycoon 2FA', Targets Microsoft 365 and Gmail Accounts
A new PhaaS service brings the power of bypassing multi-factor authentication (MFA) to the world’s most-used email platforms.
All The Ways the Internet is Surveilling You
Your personal information is continuously harvested and analyzed by countless data brokers eager to sell to the highest bidder. From your name…
Australian Government Commits to Become a World-Leader in Cybersecurity by 2030
The Australian Government has leveraged insight from cybersecurity experts to create a new six-part plan to combat cybersecurity over the …
Tokyo Police Department Warns of Phishing Scam That Uses Phony Arrest Warrants
The Tokyo Metropolitan Police Department has warned of a phishing scam that’s attempting to trick individuals with phony arrest warrants, the …
Large-Scale StrelaStealer Campaign Impacts Over 100 Organizations Within the E.U. and U.S.
A new campaign of StrelaStealer attacks identified by security analysts at Unit42 has been spotted targeting E.U. and U.S. organizations. This…
The Cyber Achilles' Heel: Why World Leaders and High-Profile Individuals Must Prioritise Cybersecurity
Social media has become an indispensable tool for communication, outreach, and engagement. From world leaders to high-profile individuals, …
Catfishing Campaign Targets Members of the UK Government
At least twelve men working in the UK parliament have recently been targeted by WhatsApp spear phishing messages, POLITICO reports. The …
Apple Users Become the Latest Targets of MFA Attacks
A new string of multi-factor authentication (MFA) attacks targeting the reset of Apple IDs seem to be popping up in a likely attempt to steal …
IT Leaders Can’t Stop AI and Deepfake Scams as They Top the List of Most Frequent Attacks
New data shows that the attacks IT feels most inadequate to stop are the ones they’re experiencing the most.
Malicious App Impersonates McAfee to Distribute Malware Via Text and Phone Calls
A trojanized version of the McAfee Security app is installing the Android banking Trojan “Vultur,” according to researchers at Fox-IT. The …
New Report Shows Phishing Links and Malicious Attachments Are The Top Entry Points of Cyber Attacks
New TTP attack data covering 2023 sheds much needed light on the threat actor and user actions that are putting organizations at the most risk.
Despite Cybersecurity Improvements in UK Organizations, Attacks Still Persist
The UK government's third phase of research shows how well UK organizations have been improving their cybersecurity efforts but …
Thread Hijacking Phishing Attack Targets Pennsylvania Journalist
A journalist in Pennsylvania was targeted by phishing attacks that involved thread hijacking, according to Brian Krebs at KrebsOnSecurity.
Must-Read New Study on Russian Propaganda Techniques
The Kyiv Post just published: "A knockout study by the Institute for the Study of War (“ISW”), just out March 27, is a must read for all the …
Your KnowBe4 Compliance Plus Fresh Content Updates from March 2024
Check out the March updates in Compliance Plus so you can stay on top of featured compliance training content.
Russian Federation-backed threat group APT29 Now Targeting German Political Parties
New analysis of APT29’s (aka Cozy Bear) activities and their association with Russia’s Foreign Intelligence Service (SVR) has revealed …
Narwhal Spider Threat Group Behind New Phishing Campaign Impersonating Reputable Law Firms
Using little more than a well-known business name and a invoice-related PDF, the “NaurLegal” phishing campaign aims at installing malware …
75% of Organizations Believe They Are at Risk of Careless or Negligent Employees
New data shows organizations are well aware that their users are one of their greatest cybersecurity risks today, and yet aren’t taking the …
New Malware Loader Delivers Agent Tesla Remote Access Trojan Via Phishing
A new malware loader is delivering the Agent Tesla remote access Trojan (RAT), according to researchers at Trustwave SpiderLabs. The malware …
Your KnowBe4 Fresh Content Updates from March 2024
Check out the 35 new pieces of training content added in March, alongside the always fresh content update highlights, events and new features.
[New Feature] Start Coaching Your Users in Real Time With the New Google Chat Integration for KnowBe4's SecurityCoach
Attention Google Workspace users! You’ve asked, and we’ve delivered, integrating KnowBe4's SecurityCoach with Google Chat.
The Number of New Pieces of Malware Per Minute Has Quadrupled in Just One Year
The threat of novel malware is growing exponentially, making it more difficult for security solutions to identify attachments and links to …
A Simple 'Payment is Underway' Phishing Email Downloads RATs from AWS, GitHub
Analysis of a new initial access malware attack shows how simple these attacks can be while also proving that malware can reside on legitimate…
[SCARY] Research Shows Weaponized GenAI Worm That Gets Distributed Via A Zero Click Phishing Email
Israeli researchers came out with a hell of a hing just now. Here is a bit of the abstract and a video. YIKES.
It’s Official: Cyber Insurance is No Longer Seen as a 'Safety Net'
A new report on the state of email security sheds some light on how organizations are viewing and approaching cyber insurance as they shift …
New Phishing-as-a-Service Kit Attempts to Bypass MFA
A Phishing-as-a-Service (PhaaS) platform called “Tycoon 2FA” has surged in popularity over the past several months, according to researchers …
[New Research] KnowBe4's Report is a Call to Action for Global Organizations to Improve Their Security Culture
We’re thrilled to announce the release of the 2024 Security Culture Report, which dives deep into how security measures affect organizations …
The Average Malicious Website Exists for Less Than 10 Minutes
A new Chrome update brings to light Google findings about malicious websites that have serious implications on detecting malicious links, …
There Is Only So Much Lipstick You Can Put on a Cybercriminal Troll
The one thing I love about our annual conference in Orlando, KB4-CON, is its thought-provoking nature. Year after year, the events team …
FBI: Losses Due to Cybercrime Jump to $12.5 Billion as Phishing Continues to Dominate
The FBI’s Internet Crime Complaint Center (IC3) newly-released Internet Crimes Report provides an unbiased big picture of the cyber crimes …
Cloud-Conscious Cyber Attacks Spike 110% as Threat Groups Sharpen their Attack Skills
New data shows increased expertise in leveraging and exploiting cloud environments.
Social Engineering The #1 Root Cause Behind Most Cyber Crimes In FBI Report
The following paragraphs were cited directly from my recent article highlighting social engineering. "Social engineering and phishing are …
Ransomware Group “RA World” Changes Its’ Name and Begins Targeting Countries Around the Globe
The threat group "RA World" (formerly RA Group) has shifted from country-specific ransomware attacks to include specific industries via a new …
[Heads-Up] Phishing Campaign Delivers VCURMS RAT
Researchers at Fortinet are tracking a phishing campaign that’s distributing a new version of the VCURMS remote access Trojan (RAT).
CISA Recommends Continuous Cybersecurity Training
In an age when 70% - 90% of successful data breaches involve social engineering (which gets past all other defenses), sufficient training is …
[Heads Up] Reinforce Your Defenses Against Rising Supply-Chain Cyber Threats
James Rundle at The Wall Street Journal today reported that in response to escalating supply-chain cyberattacks, companies are intensifying …
AI and the Boardroom: Bridging Innovation and Security
Today, artificial intelligence (AI) is no longer a futuristic concept but a tool that is driving operational efficiency, customer experience, …
Phishing Tops 2023’s Most Common Cyber Attack Initial Access Method
New analysis shows that the combination of phishing, email, remote access, and compromised accounts are the focus for most threat actors.
State-Sponsored Russian Phishing Campaigns Target a Variety of Industries
Researchers at IBM X-Force are monitoring several ongoing phishing campaigns by the Russian state-sponsored threat actor ITG05 (also known as …
Phishing-as-a-Service Platforms LabHost and Frappo Help Threat Actors Target Canadian Banks
Analysis of attacks on banking institutions in Canada can be almost perfectly tied to the use and availability of phishing-as-a-service …
CISA: Healthcare Organizations Should Be Wary of Increased Ransomware Attacks by ALPHV Blackcat
A joint cybersecurity advisory published last week discusses ransomware attack impacts on healthcare, along with ALPHV’s attack techniques, …
Organizations Are Vulnerable to Image-based and QR Code Phishing
A majority of organizations have a false sense of security regarding their resistance to phishing attacks, according to a new report from …
If Social Engineering Accounts for up to 90% of Attacks, Why Is It Ignored?
Social engineering and phishing are involved in 70% to 90% of all successful cybersecurity attacks. No other initial root hacking cause comes …
Sophos: Over 75% of Cyber Incidents Target Small Businesses
New analysis of incident data shows threat actors are evolving their attack techniques to take advantage of budget and resource-strapped small…
Despite Feeling Prepared for Image-Based Attacks, Most Organizations Have Been Compromised by Them
With QR-code phishing attacks on the rise, new data sheds light on just how unprepared organizations actually are in stopping and detecting …
New Research: BEC Attacks Rose 246% in 2023
Business email compromise (BEC) attacks surged by 246% last year, according to researchers at ReliaQuest.The researchers believe the increase …
Compromised Credentials Postings on the Dark Web Increase 20% in Just One Year
Data trends show a clear upward momentum of posts from initial access brokers on the dark web, putting the spotlight on what may become …
AI-Driven Voice Cloning Tech Used in Vishing Campaigns
Scammers are using AI technology to assist in voice phishing (vishing) campaigns, the Better Business Bureau (BBB) warns. Generative AI tools …
[Security Masterminds] The Art of Defending Against Social Engineering in the Age of AI: Insights from Rachel Tobac
Social engineering attacks can seem unpredictable and challenging to defend against. However, with the right approach, organizations can …
I am announcing AIDA: Artificial Intelligence Defense Agents!
AI is evolving a breakneck speed. Elon Musk recently said: "I've never seen any technology advance faster than AI compute. We are on the edge…
Dodging Digital Deception: How to Spot Fake Recruiters and Shield Your Career Search from Phishing Scams
Scammers are impersonating job-seeking platform Dice with phony employment opportunities designed to steal victims’ information.
How Much Will AI Help Cybercriminals?
Do not forget, AI-enabled technologies, like KnowBe4’s Artificial Intelligence Defense Agents (AIDA), will make defenses increasingly better.
Generative AI Results In 1760% Increase in BEC Attacks
As cybercriminals leverage tools like generative AI, making attacks easier to execute and with a higher degree of success, phishing attacks …
The European Union's Unified Approach to Cybersecurity: The Cyber Solidarity Act
The construction of a more cyber resilient European Union (EU) took a remarkable step forward this past week as negotiators from the European …
FBI's 2023 Internet Crime Report Highlights Alarming Trends on Ransomware
The specter of cybercrime continues to grow, with losses soaring to $12.5 billion in 2023, according to the recently released Internet Crime …
Three Essential Truths Every CISO Should Know To Guide Their Career LinkedIn
According to my research, it became clear that if CISO's focused on these three items, it would take care of 99% of the vulnerabilities.
AI and Ransomware Top the List of Mid-Market IT Cyber Threats
A recent report reveals a significant discrepancy in the priorities of mid-market IT departments when it comes to addressing cyber threats. …
European Diplomats Targeted With Phony Invitations to a Wine-Tasting Party
Researchers at Zscaler observed a cyberespionage campaign that targeted European diplomats with malicious PDFs disguised as invitations to a …
Customer Spotlight: MESA’s Strategy for Building Strong Security Culture and Email Defense
In a world where digital threats grow more sophisticated by the day, gaining firsthand knowledge from those who have successfully bolstered …
New Research: Spike In DNS Queries Driving Phishing and Cyber Attacks
New analysis of DNS queries shows material growth in phishing, malware and botnets and offers insight into how many threats the average person…
Chicago Man Sentenced to Eight Years in Prison for Phishing Scheme
A 30-year-old man from Chicago, Joseph Alexander Valdez, has been sentenced to eight years in prison for conducting a Snapchat phishing scheme…
Microsoft and OpenAI Team Up to Block Threat Actor Access to AI
Analysis of emerging threats in the age of AI provides insight into exactly how cybercriminals are leveraging AI to advance their efforts.
Phishers Abusing Legitimate but Neglected Domains To Pass DMARC Checks
A recent great article by BleepingComputer about domain hijacking and DMARC abuse reminded me that many companies and people do not understand…
Phishing Kit Targets the FCC and Crypto Exchanges
Researchers at Lookout have discovered a sophisticated phishing kit that’s targeting employees at the US Federal Communications Commission …
Planning with Purpose: 10 Tips to Develop a Year-Long Security and Compliance Training Program
Our team at KnowBe4 recently got together to talk about planning for annual security and compliance training.
Cybercriminals Sent 1.76 Billion Social Media Phishing Emails in 2023
As social media phishing reaches new heights, new data reviewing 2023 shows a massive effort by cybercriminals to leverage impersonation of …
Email-Based Cyber Attacks Increase 222% as Phishing Dominates as the Top Vector
Analysis of the second half of 2023 shows attackers are getting more aggressive with email-based phishing attacks in both frequency and …
New Research: Ransomware Incidents Spike 84% in 2023
Newly-released data covering cyberthreats experienced in 2023 sheds some light on how very different last year was and paints a picture of …
Phishing Campaign Targets Mexican Taxpayers With Tax-Themed Lures
A phishing campaign is targeting users in Mexico with tax-themed lures, according to researchers at Cisco Talos. The phishing emails direct …
Game-Changer: Biometric-Stealing Malware
I have been working in cybersecurity for a long time, since 1987, over 35 years. And, surprisingly to many readers/observers, I often say I …
When Threat Actors Don’t Have a Viable Email Platform to Phish From, They Just Steal Yours
New analysis of a phishing campaign shows how cybercriminals use brand impersonation of the platforms they need to compromise accounts and …
Credential Theft Is Mostly Due To Phishing
According to IBM X-Force’s latest Threat Intelligence Index, 30% of all cyber incidents in 2023 involved abuse of valid credentials. X-Force’s…
Emails Are Responsible for 88% of Malicious File Deliveries
Emails are still the most common delivery method for malicious files, according to Check Point’s Cyber Security Report for 2024.
Annual Ransomware Payments Surpass $1 Billion
For the first time, analysis of ransomware payments made in a single year tops $1,000,000,000. This signals a massive return to more frequent,…
[SCARY] You knew about OSINT, but did you know about ADINT?
WIRED just published a scary (long) article. I am summarizing it here and highly recommend you read the whole thing.
Swiss Government Identified 10,000 Phishing Websites Impersonating 260 Brands
Attacks targeting Swiss residents increased 10% last year, according to newly-released data that shows a growth in not just phishing attacks, …
Your KnowBe4 Compliance Plus Fresh Content Updates from February 2024
Check out the February updates in Compliance Plus so you can stay on top of featured compliance training content.
Face off: New Banking Trojan steals biometrics to access victims’ bank accounts
Venturebeat had the scoop on a fresh Group-IB report. They discovered the first banking trojan that steals people’s faces. Unsuspecting users …
Nearly One in Three Cyber Attacks In 2023 Involved The Abuse of Valid Accounts
Thirty percent of all cyber incidents in 2023 involved abuse of valid credentials, according to IBM X-Force’s latest Threat Intelligence …
Data Breach at French Healthcare Payment Processor Puts 20 Million Policyholders at Risk
A single account being phished caused millions of French healthcare policyholder records to be breached.
Your KnowBe4 Fresh Content Updates from February 2024
Check out the 29 new pieces of training content added in February, alongside the always fresh content update highlights, events and new …
Exposed: Global Espionage Unleashed by China's Police in Groundbreaking Leak
I get my news from a very wide variety of sources. One is the venerable SpyTalk news that lives in Substack. They just reported something …
QR-Code Attacks Target the C-Suite 42 Times More than Standard Employees
QR-code attacks leveraging QR-codes are kicking into high gear and becoming a common method used in phishing attacks, according to new data …
Anyone Can Be Scammed and Phished, With Examples
I recently read an article about a bright, sophisticated woman who fell victim to an unbelievable scam. By unbelievable, I mean most people …
Malware Delivered Through Phishing Surges 276%
Researchers at VIPRE Security observed a 276% increase in malware delivered by phishing between Q1 and Q4 of 2023.
[INFOGRAPHIC] KnowBe4’s Learner App by the Numbers
The KnowBe4 Learner App enables your users to complete their security awareness and compliance training conveniently from their smartphones …
Malvertising Campaign Spreads Phony Utility Bills
A widespread malvertising campaign is attempting to trick users into paying phony utility bills, according to researchers at Malwarebytes.
The Unsettling Leap of AI in Video Creation: A Glimpse Into Sora
In the rapidly evolving landscape of artificial intelligence (AI), the launch of Sora by OpenAI marks an unnerving milestone in video synthesis.
IBM Tests Audio-Based Large Language Model to Hijack Live Conversations
With the idea in mind to “audio-jack” a live call-based banking transaction, security researchers were successful in inserting …
Making The Return on Investment (ROI) Case For Security Awareness Training
As an InfoSec professional, one of your many important responsibilities is to minimize expensive downtime and prevent data breaches.
State-Sponsored Threat Actors Targeting European Union Entities With Spear Phishing Campaigns
Numerous state-sponsored threat actors frequently launched spear phishing attacks against European Union entities last year, according to a …
Only 7% of Organizations Can Restore Data Processes within 1-3 Days After a Ransomware Attack
New data on how organizations are able to respond to ransomware attacks also shows that paying a ransom is highly likely, despite having a …
The IT Pro's How-to Guide to Building a Strong Security Culture
The thought of building and improving your organization’s security culture can seem like a daunting task. How can you influence an entire …
Messaging Platform Telegram Sprouts Cyber Crime “Marketplaces” of Tools, Insights and Data
Cybercriminals are taking advantage of the messaging platform Telegram by creating channels and groups where learning and commerce all can …
Augmented Security: The Impact of AR on Cybersecurity
Recently, Apple launched its Apple Vision Pro to much fanfare and has pushed the discussion of Augmented Reality (AR) beyond the realms of …
Iran-Aligned Threat Actor "CharmingCypress" Launches Spear Phishing Attacks
Researchers at Volexity warn that the suspected Iranian threat actor CharmingCypress (also known as “Charming Kitten” or “APT42”) has been …
Over Half of Malware Downloads Originate from SaaS Apps
As the popularity of SaaS apps continues to grow, security analysts expect the misuse of such apps as the host for malware downloads to …
Phishing Campaign Exploits Remote Desktop Software
A phishing campaign is attempting to trick users into downloading remote monitoring and management (RMM) software like AnyDesk, Atera, and …
Number of Data Compromises Affecting U.S. Organizations Rises To 77%
New data summarizing the compromises of data in 2023 provides key details on who’s being targeted, what types of data is being compromised, …
Cupid’s Arrow of Cyber Scams
Valentine's Day. A time where love is in the air, florists work overtime, and restaurant tables are as scarce as a truthful politician. But as…
Another Ransomware-as-a-Service Known as “Wing” Takes Flight on the Dark Web
Analysis of this newly-spotted service makes it clear that the newest entrant into the Ransomware-as-a-Service (RaaS) space has taken note of …
AI in Cyberspace: A Double-Edged Sword
The UK's National Cyber Security Centre (NCSC), recently shared its findings on how AI might reshape the cyber landscape. In two separate …
Hard Lessons From Romance Scams
Seeing as this week is Valentine’s Day, I should have written something about rom coms, true love, and trusting your heart more. But this is …
Security Teams Spend 71 Hours Responding to Every One Hour in a Cyber Attack
New data sheds light on what kinds of cyber attacks are targeting your cybersecurity team, what it’s costing them, why it’s taking so much …
Americans Lose a Record $10 Billion to Fraud in 2023; Mostly Due To Investment Scams
The US Federal Trade Commission (FTC) has disclosed that people in the United States lost a record $10 billion to fraud in 2023, a 14% …
Calculating Materiality for SEC Rule 1.05
The U.S. Securities and Exchange Commission (SEC), through a new requirement of Item 1.05 of the 8-K, requires that all regulated companies …
Browser-Based Phishing Attacks Increase 198%, With Evasive Attacks Increasing 206%
A new report shows massive increases in browser attacks in the second half of 2023, with over 31,000 threats specifically designed to bypass …
Watch Out For Valentine’s Day Romance Scams
Users should be wary of online romance scams ahead of Valentine’s Day, according to Imogen Byers at ESET. While in the past these scams could …
Cybersecurity Resiliency and Your Board of Directors
Growing cybersecurity threats, especially ransomware attacks, and the Securities and Exchange Commission’s (SEC) recent rules have made having…
81% of Organizations Cite Phishing as the Top Security Risk
Organizations are finally dialing in on where they need to focus their cybersecurity strategies, starting with phishing. But the top four …
Unprecedented Rise of Malvertising as a Precursor to Ransomware
Cybercriminals increasingly used malvertising to gain initial access to victims’ networks in 2023, according to Malwarebytes’s latest State of…
Chinese Hackers Spy on Dutch Ministry of Defense: A Story of Alarming Cyber Espionage
In a revelation that adds yet another chapter to the ongoing saga of international cybersecurity threats, the Dutch Ministry of Defense …
How to Fight Long-Game Social Engineering Attacks
Sophisticated cybercriminals are playing the long game. Unlike the typical hit-and-run cyber attacks, they build trust before laying their …
Synthetic Data: The New Frontier in Cyber Extortion
Organizations are increasingly facing cyber attacks resulting in data breaches, and part of their post-incident responsibilities includes …
Generative AI Used to Launch Phishing Attacks
Criminal threat actors are increasingly utilizing generative AI tools like ChatGPT to launch social engineering attacks, according to …
New Phishing-As-A-Service Kit with Ability to Bypass MFA Targets Microsoft 365 Accounts
A phishing-as-a-service platform called “Greatness” is facilitating phishing attacks against Microsoft 365 accounts, according to researchers …
Fake “I Can’t Believe He’s Gone” Posts Seek to Steal Facebook Credentials
A new scam relies on a victim's sense of curiosity, brand impersonation, and the hopes of a new login to compromise Facebook credentials.
Social Engineering Masterstroke: How Deepfake CFO Duped a Firm out of $25 Million
Check out this one line for a moment...“duped into attending a video call with what he thought were several other members of staff, but all of…
Vendor Email Compromise Attacks Against Financial Services Surge 137% Last Year
Analysis of 2023 attacks shows how the financial services industry had a very bad year, with increases in both vendor email compromise (VEC) …
81% of Underwriters Expect Cyber Insurance Premiums to Increase as Risk is Expected to Soar
New data from cyber insurance underwriters shows what they think the biggest threats will be in 2024 and what organizations should do about …
Microsoft Teams: The New Phishing Battlefront - How Attackers Are Exploiting Trusted Platforms
Attackers are abusing Microsoft Teams to send phishing messages, according to researchers at AT&T Cybersecurity.
Associated Press: "Grave peril of digital conspiracy theories."
The AP published a great article. This is your executive summary: Conspiracy theories have always been part of American culture, but advanced …
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human …
FBI Cyber Alert: Tech Support Scams Steal Cash or Precious Metals
The US Federal Bureau of Investigation (FBI) has issued an alert warning that scammers are tricking victims into converting their savings into…
Ransomware Payments On The Decline As Cyber Attackers Focus on The Smallest, And Largest, Organizations
New data for Q4 of 2023 reveals a sizable shift in the cyber threat landscape, with serious implications regarding ransomware and social …
[Live Demo] Customizing Your Compliance Training to Increase Effectiveness
Linking compliance training to specific outcomes is hard. Compliance training has a reputation for being challenging for organizations to …
The Percentage of Organizations Globally Struck by Ransomware Hits an All-Time High
Check Point’s review of ransomware shows that the percent of organizations worldwide hit by this greatest of cyberthreats rose by a whopping …
Open Redirects Used to Disguise Phishing Links
Phishing attacks are increasingly using open redirects to evade detection by security filters, according to researchers at Trustwave.
Forget Deepfake Audio and Video. Now There’s AI-Based Handwriting!
Researchers have developed AI technology that can mimic someone’s handwriting with only a few paragraphs of written content. Experts worry …
Malvertising Targets Chinese-Speaking Users
Researchers at Malwarebytes warn that a malvertising campaign is targeting Chinese-speaking users with phony ads for encrypted messaging apps.…
Identify Weak User Passwords With KnowBe4’s Enhanced Weak Password Test
Passwords are part of every organization’s security risk profile. Just one weak password with access to an organization’s critical systems can…
Scammers Use Airdrops to Lure Users With Phony NFTs
Researchers at Check Point warn that scammers are using airdrops to distribute phony non-fungible tokens (NFTs) that direct users to malicious…
Bravo Host Andy Cohen Scammed Out of a “Sizable” Amount of Money by Fraudsters Posing as the Bank
Bravo host Andy Cohen tells how he became the victim of an impersonation scam that gave scammers access to control his bank account.
Your KnowBe4 Compliance Plus Fresh Content Updates from January 2024
Check out the January updates in Compliance Plus so you can stay on top of featured compliance training content.
Your KnowBe4 Fresh Content Updates from January 2024
Check out the 37 new pieces of training content added in January, alongside the always fresh content update highlights, events and new features.
Houston, We Have a 2024 China Problem
Russia is not the only global problem that democracy has to deal with. The Chinese regime ran large influence campaigns, attempting mass …
The Number of Ransomware Attack Victims Surge in 2023 to over 4000
The surge in Ransomware-as-a-Service affiliates is likely the reason behind the dramatic increase in the number of victimized organizations, …
HP Enterprise Reveals It was hacked by the same Russians that broke into Microsoft
In a new SEC disclosure, Hewlett Packard Enterprise (HPE) announced on Wednesday that it fell prey to the same Russian intelligence group, …
Browser-based Phishing Attacks Increase By 198% Over Six Months
Researchers at Menlo Security observed a 198% increase in browser-based phishing attacks over the past six months.
Social Engineering Attacks Rising in the Trucking Industry
Spear phishing and voice phishing (vishing) are on the rise in the trucking industry, according to a new report from the National Motor …
New Deepfake Video Scam has “Taylor Swift” Offering Free French Cookware
A new wave of ads utilizing video of well-known celebrities seemingly promoting video games, fake giveaways, and more are starting to popup, …
Roblox Game 'Hack-A-Cat' Now Part of the Free KnowBe4 Children’s Interactive Cybersecurity Activity Kit
If you haven’t heard of Roblox, you probably don’t have kids like me. Roblox is an online virtual world/metaverse that has been around since …
Use of Generative AI Apps Jumps 400% in 2023, Signaling the Potential for More AI-Themed Attacks
As the use of Cloud SaaS platforms of generative AI solutions increases, the likelihood of more “GPT” attacks used to gather credentials, …
North Korean Threat Actor Targeting Cybersecurity Researchers With Spear Phishing Attacks
A suspected North Korean state-sponsored threat actor called “ScarCruft” is launching spear phishing attacks against cybersecurity …
Unprecedented Cybersecurity Alert: 26 Billion Records Exposed in Mega Data Breach
Cybernews just reported: In what appears to be a digital tsunami, a colossal data breach has surfaced, unveiling a staggering 26 billion …
Facebook Phishing Scams Target Concerned Friends and Family
BleepingComputer describes a phishing scam that’s been running rampant on Facebook for the past several months, in which threat actors use …
AI Does Not Scare Me, But It Will Make The Problem Of Social Engineering Much Worse
I am not scared of AI. What I mean is that I do not think AI is going to kill humanity Terminator-style. I think AI is going to be responsible…
Russian State-Sponsored Threat Actor Targets High Profile Individuals in Phishing Campaign
The Russian state-sponsored threat actor “COLDRIVER” is launching phishing campaigns against “high profile individuals in NGOs, former …
Russian Hackers Win Big: Microsoft's Senior Exec Team Emails Breached
In a Friday regulatory filing, Microsoft has reported that its corporate email accounts were compromised by a Russian state-sponsored hacking …
Facebook Work-From-Home “Job” Posting Scam Goes the Extra Mile to Trick Victims
A new job posting scam found by IT security company Qualysys is focused on capturing victim’s identity details, accessing victim’s Facebook …
Scammers Target Owners of Missing Pets
Some particularly cold-hearted scammers are targeting users of lost pet forums with phony ransom demands, the BBC reports.
More Than Half of Data Breaches in the U.K.’s Legal Sector are Due to Insider Error
A new analysis of data breaches in the United Kingdom's legal sector shows that organizations need to be looking inward more and look for ways…
‘Swatting’ Becomes the Latest Extortion Tactic in Ransomware Attacks
Rather than stick to traditional ransomware extortion methods that revolve around the attack itself, a new form of extortion known as Swatting…
Ninety-Four Percent of Organizations Sustained Phishing Attacks Last Year
A survey by Egress has found that 94% of organizations were hit by phishing attacks in 2023, Infosecurity Magazine reports. Additionally, 91% …
Malicious APKs Drain Bank Accounts
A phishing campaign is targeting Chinese users in an attempt to distribute malicious apps, according to researchers at Palo Alto Networks’s …
Cryptocurrency Drainer Distributed Through Phishing
Mandiant has published a report on “CLINKSINK,” a cryptocurrency Drainer-as-a-Service (DaaS) that’s targeting users of the Solana currency.
LinkedIn is Being Used for *Dating* – It’s a Recipe for Disaster
A new article explains how business professionals are beginning to be not-so-professional and seeking to make personal connections. It’s only …
Analysis of Phishing Emails Shows High Likelihood They Were Written By AI
It’s no longer theoretical; phishing attacks and email scams are leveraging AI-generated content based on testing with anti-AI content …
Women CyberSecurity Society Targeted by Smishing Campaign
The Canada-based Women CyberSecurity Society (WCS2) has warned that its leadership, members, and volunteers are being targeted by an SMS …
Three-Quarters of Organizations Have Experienced Phishing Attack in the Last 12 Months
Regardless of whether your environment remains on-premise, resides in the cloud, or is a hybrid configuration, new data makes it clear that …
[New Phishing Template] Formula 1 Exclusive: Gene Haas on Guenther Steiner's Departure
In a surprising turn of events for Formula 1 enthusiasts, the Haas F1 Team is grappling with the departure of its widely-respected Team …
Beware of "Get to Know Me" Surveys
Trained security awareness professionals are aware that whatever someone says about themselves and personal experiences can be used against …
Microsoft Takes the Lead in Q4 2023 for Alarming Phishing Attempts
Microsoft was the most impersonated brand last quarter, accounting for a third (33%) of all brand phishing attempts in October, November, and …
FTC Issues Warning About the Dangers of QR Code-Based Scams
The latest consumer alert posted by the federal trade commission (FTC) signals that the upticks in QR code-based scams are being seen by …
KnowBe4 Named a Leader in the Winter 2024 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR)
We are excited to announce that KnowBe4 has been named a leader in the Winter 2024 G2 Grid Report for Security Orchestration, Automation, and …
[Security Masterminds] Revolutionizing Cybersecurity Training: How AI Is Changing the Game
Artificial intelligence (AI) in the cybersecurity realm is a nuanced topic. On the one hand, it has the potential to enhance our abilities to …
Beyond the Scams: Unraveling the Dark Tactics of Real-World Kidnapping Scams and Virtual Extortion
The world can be a scary and dangerous place. Its unethical scammers have no problem doing almost anything to make a buck, but sometimes, …
Pikabot Malware Spreading Through Phishing Campaigns
Researchers at Trend Micro warn that a threat actor known as “Water Curupira” is distributing the Pikabot malware loader via widespread …
KnowBe4 Named a Leader in the Winter 2024 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares security awareness training (SAT) …
Cybercriminals Celebrate the Holidays with Dark Web Data Dumps, Dubbed “Leaksmas”
Millions of data records and GBs of data from organizations around the globe were made freely available to cybercriminals to coincide with …
Red Flags for Phishing: Verizon Outlines Common Scams to Watch Out For
Verizon has published an article outlining various forms of social engineering attacks, including SMS/text messaging phishing (smishing), …
Guarding the Cloud: Top 5 Cloud Security Hacks and How You Can Avoid Them
Navigating the cloud security landscape is no walk in the park. It requires IT professionals like you to not only tackle traditional security …
FBI Releases Blackcat Ransomware Decryption Tool to Victims, Disrupting Attacks
For the first time ever, the U.S. Justice Department announced the existence of an FBI-developed decryption tool that has been used to save …
2024 Security Software Pricing Preference Survey
I need your help, I'm super interested to know what your current preferences are related to licensing and pricing models for security …
Black Basta Ransomware Decryptor Released to Help Some Victims
A flaw found by security researchers in the encryption software allows victim organizations to use “Black Basta Buster” to recover some of …
Beware of Fraudulent Charge Messages
Be careful of emails, SMS messages, or calls claiming to be from your bank about your card being used fraudulently. If this ever happens, call…
Out of the Shadows: Resecurity Exposes 'GXC Team' – Architects of Cybercrime in Online Banking and Social Engineering
Resecurity is tracking a cybercriminal gang called “GXC Team” that develops and sells tools to facilitate online banking theft and social …
Phishing Reigns as the Most Likely and Most Feared Cyber Attack
With over half of organizations being the victim of password-based attacks in the last year, new data sheds light on the risk of phishing …
[LIVE DEMO] Are Your Users Making Risky Security Mistakes? Deliver Real-Time Coaching in Response to Risky User Behavior with SecurityCoach
Do you need an easy, automated way to provide real-time feedback the moment your users make risky mistakes to help reinforce the training …
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human …
Lockbit 3.0 Ransomware Disrupts Emergency Care at Multiple German Hospitals
Hitting three hospitals within a Germany-based hospital network, the extent of the damage in this confirmed ransomware attack remains …
New Research: Phishing Attacks Stole $295 Million In Crypto In 2023
Researchers at Scam Sniffers have found that phishing attacks stole nearly $295 million worth of cryptocurrency from 324,000 victims in 2023, …
A Dream Team Security Awareness Training Program?
Every person and organization is different and requires slightly different methods and ways of learning. But every person and organization can…
[Security Masterminds] Beyond the Technical: Cultivating Empathy in Cybersecurity
Cybersecurity exists to protect people and their information. In our recent discussion on Security Masterminds, Julie provided unique insights…
Researchers use AI chatbots against themselves to 'jailbreak' each other
Fascinating article at TechXplore, December 28, 2023. Computer scientists from Nanyang Technological University, Singapore (NTU Singapore) …
AI in 2024: The Top 10 Cutting Edge Social Engineering Threats
The year 2024 is shaping up to be a pivotal moment in the evolution of artificial intelligence (AI), particularly in the realm of …
Your KnowBe4 Fresh Content Updates from December 2023
Check out the 36 new pieces of training content added in December, alongside the always fresh content update highlights, events and new …
Impersonation Attack Data Breaches Predicted to Increase in 2024
With so much of an attack riding on a cybercriminals ability to gain access to systems, applications and data, experts predict the trend of …
U.K. Government 'Ill-Prepared' to Deal With High Risk of Catastrophic Ransomware Attacks
A new report from the U.K. government’s Joint Committee on the National Security Strategy (JCNSS) outlines both just how likely an attack on …
SMTP Smuggling Technique Bypasses Email Authentications Establishing Legitimacy
A newly-discovered technique misusing SMTP commands allows cybercriminals to pass SPF, DKIM and DMARC checks, empowering impersonated emails …
We Do What We Are Trained To Do
When I was young, I was an oceanfront lifeguard, firefighter and EMT paramedic. All disciplines involved frequent education and training.
Ransomware Attacks Rise 85% Compared to the Previous Year
With November demonstrating multiple increases when compared to various previous time periods, new data signals that we may be in for a bumpy …
Cyber Scammers Beef Up the Number of Fake Delivery Websites Just in Time for Christmas
Cybersecurity researchers at Group-IB have identified a single scam campaign leveraging over 1500 websites impersonating postal carriers and …
The AI Threat: How America's 2024 Election Could Be Compromised
I found an interesting article at THEHILL that started with "Fears grow over AI’s impact on the 2024 election" and discusses the rising …
Nice! I made it in the Top 25 Cybersecurity CEOs to Watch in 2024
The CyberExpress is a VC-backed cyber security news mag that provides the latest news and analysis about the information security industry. …
SC Mag: "Attacks on critical infrastructure are harbingers of war: Are we prepared?"
I just found a great post by Morgan Wright, chief security advisor of SentinelOne. Here is a quick summary and a link to the full article is …
Missing the Lock Icon in Chrome’s Address Bar? It’s a Move to Make You More Secure
In response to what Google calls “over trust” in the web address lock icon to indicate that a site is authentic and its’ communications are …
Underground Cyber Crime Marketplaces are Now Showing Up on the Open Web
Marketplaces such as OLVX are shifting from the dark web to the open web to take advantage of traditional web services to assist in marketing …
Interest in AI-Generated ‘Undressing’ Increases 2000% as it Becomes a Mainstream Online Business
The advent of non-consensual intimate imagery (NCII) as a monetized business on the Internet has shifted pornography into the realm of …
Cancer Center Patients Become Attempted Victims of Data Extortion
Cybercriminals of the lowest kind breached as many as 800,000 patients and then sent emails threatening to sell their data if they didn’t pay …
“Mr. Anon” Infostealer Attacks Start with a Fake Hotel Booking Query Email
This new attack is pretty simple to spot on the front, but should it be successful in launching its’ malicious code, it’s going to take its’ …
New Remote “Job” Scam Tells Victims They'll Get Paid For Liking YouTube Videos
Researchers at Bitdefender warn that scammers are tricking victims with fake remote job opportunities. In this case, the scammers tell victims…
Holiday Scams Include Thousands of Impersonation Phishing Domains per Brand
Midstride in this year’s holiday shopping, it’s important to realize just how many websites exist that impersonate legitimate online …
Unique Malware Used in Cyber Attacks Increases by 70% in Just One Quarter
As more cybercriminal gangs continue to enter the game, the massive increase in unique types of malware means it will become increasingly …
IRS Warns of Expected Wave of Tax Scams
Urging taxpayers and tax professionals to be vigilant, the Internal Revenue Service (IRS) provides some simple guidance on how to spot new …
Why Security Awareness Training Is Effective in Reducing Cybersecurity Risk
Security awareness training (SAT) works! A well-designed security awareness training campaign will significantly reduce cybersecurity risk.
Brand New BazarCall Phishing Campaign Abuses Google Forms
A new BazarCall phishing campaign is using Google Forms to send phony invoices, according to researchers at Abnormal Security.
As the Holiday Season Ramps Up, So Do Scams Impersonating the U.S. Postal Service
Taking traditional “delayed package” scams up a notch, new phishing and smishing attack campaigns are leveraging freemium DNS services to …
Phishing Remains the Most Common Attack Technique, With Malicious URL Use Increasing 144%
Analysis of nearly a year’s worth of emails brings insight into exactly what kinds of malicious content are being used, who’s being …
Undercover Threat: North Korean Operatives Infiltrate U.S. Companies Through Job Platforms
Researchers at Nisos warn that North Korean threat actors are impersonating skilled job seekers in order to obtain remote employment at US …
How To Fight Long-Game Social Engineering
CISA sent out a warning about a Russian advanced persistent threat (APT) called Star Blizzard warning about their long-game social engineering…
Who's Calling? Spam, Scams and Wasted Time
First ever insight into those annoying spam calls provides enlightening detail into how many calls are there, where are they coming from, and …
Unwrapping the Threat: AI-Powered Phishing Attacks Take Center Stage in 2023 Holidays
As the holiday season approaches, so does the annual surge in online shopping and holiday package tracking. Unfortunately, this joyous time …
Russia Weaponizes Israel-Hamas Conflict in Targeted Phishing Attack
Researchers at IBM X-Force are tracking a phishing campaign that’s using themes related to the Israel-Hamas war to deliver Headlace, a …
Russian Hackers Indicted for Phishing Attacks Against U.S. and Allies
The US Justice Department has indicted two individuals for launching spear phishing attacks against the US, the UK, Ukraine and various NATO …
Deepfakes: The New Face of Fraud
Security analysts at identity vendor Sumsub are seeing a massive rise in the use of deepfake fraud in their Identity Fraud Report 2023. And …
WSJ: "A Hidden Risk in the Municipal Bond Market: Hackers"
December 7, 2023 - The Wall Street Journal has an interesting perspective on K-12 Public schools suffering ransomware attacks. The number …
2024 IT Spending Surge: Surprising Insights from Piper Sandler's CIO Survey
Industry analysts Piper Sandler do a yearly 'Industry Note' where they survey CIOs about their next year budget expectations. For 2024 there …
Maximizing Your Purchasing Power: A Source For Validated KnowBe4 Reviews
One of the key strategies to maximize your purchasing power is to research products and compare total cost of ownership. Take the time to do …
Phishing Defense: Train Often to Avoid the Bait
Surveys, unfortunately, show that the vast majority of organizations do little to no security awareness training. The average organization, if…
Nearly Every CIO Identifies at Least One Cyber Threat as a Risk to their Business
When 97% of CIOs all see things the same way, it’s probably a sign to take the risk of cyber threats seriously – a problem new data shows is …
Cyber Attacks and Data Breaches Cited as the Number One Business Risk for Organizations
Even when looking at the various kinds of risks to business, cyber attacks still remain the biggest problem. But new data shows there may be a…
Phishing-Resistant MFA Will Not Stop Phishing Attacks
You would be hard-pressed to find an author and organization (KnowBe4) that has pushed the use of phishing-resistant multi-factor …
Don't Be Fooled By This Sneaky Disney+ Scam
A phishing campaign is impersonating Disney+ with phony invoices, according to researchers at Abnormal Security. The phishing emails targeted …
New York Unit of Worlds Largest Bank Becomes Ransomware Victim
The ransomware attack on ICBC Financial Services caused disruption of trading of U.S. Treasuries and marked a new level of breach that could …
The Alarming Threat of Ransomware: Insights from the Secureworks State of the Threat Report 2023
In the ever-evolving landscape of cybersecurity, the battle against ransomware has taken a concerning turn. According to the latest findings …
New SEC Rules Will Do More Than Result in Quick Breach Reporting
On July 26, the U.S. Security & Exchange Commission (SEC) announced several new cybersecurity rules, taking affect mid-December 2023, that…
Financial Institutions are the Most Affected by Phishing Attacks and Scams
New data shows how the overwhelming majority of phishing attacks on financial institutions dwarf every other industry sector by as much as a …
PDFs: Friend or Phishing Foe? Don't Get Caught by the Latest Scam Tactic
Researchers at McAfee warn that attackers are increasingly utilizing PDF attachments in email phishing campaigns.
How The Disinformation Machine Works, And How $400 Can Stop It
Specifically when wars break out, disinformation kicks into high gear. In the wake of the October 7 Hamas attack, the internet has been …
Phishing Kits Undergo an Evolution in Feature Set, Demand, and Branding
Now being commonly referred to as “Scama” – short for Scamming Method – these kits are being sold promoting highly advanced feature sets, …
Guarding Against the Rise of QR Code Phishing Attacks: How to Protect Yourself and Your Organization
In the ever-evolving landscape of cyber threats, scammers and hackers are relentless in exploiting every avenue of communication. From emails …
Sexual Harassment Prevention Training from…KnowBe4?
When you think of KnowBe4, you probably think of phishing training, good password hygiene modules, security awareness, or maybe even data …
Combatting Rogue URL Tricks: Quickly Identify and Investigate the Latest Phishing Attacks
Everyone knows you shouldn’t click phishy links. But are your end users prepared to quickly identify the trickiest tactics bad actors use …
The Israel-Hamas Conflict is the Latest Example of Phishing Attacks Taking Advantage of Current Events
Using something as simple as an attachment with an Israel/Hamas-related filename seems to be all it takes for new social engineering attacks …
Security Awareness Training Can Help Defeat Deepfake and AI Phishing
There is no doubt that more pervasive deepfake and AI technologies will make for more realistic, sophisticated, phishing attacks, and add to …
Vishing Gang Takes Victims for “Tens of Millions” Using Little More than Social Engineering
Czech and Ukrainian police have arrested six individuals responsible for a call center-based vishing scam designed to trick victims into …
The Israel-Palestine Conflict is the Latest Example of Phishing Attacks Taking Advantage of Current Events
Using something as simple as an attachment with an Israel/Palestine-related filename seems to be all it takes for new social engineering …
Criminals Are Cautious About Adopting Malicious Generative AI Tools
Researchers at Sophos have found that the criminal market for malicious generative AI tools is still disorganized and contentious.
Top Four Security Tips for Cyber Safety on National Computer Security Day
To celebrate National Computer Security Day, which is recognized on November 30 every year, KnowBe4 encourages all IT and security …
Your KnowBe4 Fresh Content Updates from November 2023
Check out the 49 new pieces of training content added in November, alongside the always fresh content update highlights, events and new …
No One Knows How Online Pharmacy Company was Hit with a Data Breach Impacting 2.3 Million Customers
This is a cautionary tale of both how your data can legally end up in the hands of an organization you never intended and how victims can be …
QR Code Phishing Campaigns on the Rise
There’s been a “precipitous rise” in QR code phishing campaigns in 2023, according to Matthew Tyson at CSO.
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human …
Users Fall for Smishing Attacks 6-10 Times More Than Email-Based Attacks
With organizations heavily focusing on protecting the corporate endpoint, cybercriminals are switching focus onto mobile devices where users …
Who Knew Neanderthals were so High-Tech?
Researchers at ESET describe various types of scams launched by users of Telekopye, a telegram bot that assists in crafting social engineering…
My Top 7 Cybersecurity Reflections for 2024
The digital landscape is evolving at an exponential rate, and with it, the cybersecurity challenges we face.
Initial Access Broker Activity Doubles in One Year’s Time
New data sheds light on just how active the Initial Access Broker (IAB) business is, and the growth uncovered doesn’t bode well for potential …
Huntress Finds Business Email Compromise (BEC) Increases In Q3, 2024
Huntress has released a report finding that business email compromise (BEC) attacks have risen in the third quarter of 2023.
New Data Covers How the Retail Market is at Greater Risk of Industry-Specific Cyberthreats
A new analysis of the retail market’s threat landscape discusses the challenges faced by this industry and what threat tactics are being used …
Digital Skimming Increases by 50%, Just in Time for the Holiday Season
Security researchers identify growth in the use of an ongoing cyberskimming campaign that involves compromising legitimate website checkout …
Phishing Attacks Expected to More Than Double During the Black Friday and Cyber Monday Shopping Week
Another day, another warning about holiday scams! Lookout Inc., a data-centric cloud security company, is warning employees and businesses …
Visa Warns of Increased Phishing Scams During Holiday Season
Visa Payment Fraud Disruption (PFD) expects phishing attacks to increase between November 2023 and January 2024. Findings in its Holiday …
Compromised Bloomberg Crypto Channel Phishes for Thousands of Discord Users' Login Details
Scammers are using a compromised X (formerly Twitter) account belonging to Bloomberg Crypto to send users to a phishing site designed to steal…
73% of Organizations Affected by Ransomware Attacks Globally in 2023, According to Statista
I recently wrote about how 1 in 34 organizations globally has experienced an attempted ransomware attack. But that statistic doesn’t provide …
With Expected Increases of Holiday Sales Comes Similar Expectations of More Cyber Scams
If increases in cyberattacks this year are any indication of what to expect in the next six weeks of holiday shopping, we should expect a …
Cybercrime Group "Scattered Spider" is a Social Engineering Threat
The US Cybersecurity and Infrastructure Security Agency (CISA) and the FBI have released a joint Cybersecurity Advisory describing the …
KnowBe4 Integrates With Cisco Duo To Streamline Secure Sign Ins
Social engineering remains one of the top attack vectors that cybercriminals use to execute malicious acts. KnowBe4’s security awareness …
Johnny Jet's $3,000 Podcast Scam Nightmare – Unveiling the Elaborate Con that Hijacked his Facebook Kingdom
Travel influencer Johnny Jet has disclosed that he fell victim to a scam that caused him to lose access to his Facebook account, which has …
QR Code Phishing Attacks Surging
The massive uptick in QR Code phishing is an indicator that scammers are seeing success in taking victims from the initial attack medium to …
[Keynote Announcement] See Rachel Tobac at KB4-CON 2024!
We can’t keep this a secret any longer! Rachel Tobac will be joining us live at KB4-CON 2024, happening in Orlando, Florida March 4-6. She’s …
BlackCat Ransomware's New SEC Reporting Tactic: Turn Regulations Against Victims
Man Bites Dog: In an unusual twist in cybercrime, the ransomware group BlackCat/ALPHV is manipulating the SEC's new 4-day rule on cyber …
How to Help "Frequent Clickers" Become More Mindful
Within our organizations, there are those employees who consistently exhibit mindfulness, avoiding every phishing attempt. Yet, there are also…
New ASD Cyber Threats Report Shows A Cybercrime Incident Is Reported in Australia Every Six Minutes
The annual Cyber Threat Report by the Australian Signals Directorate (ASD) was released this week, containing insights that every Australian …
AI-Manipulated Media Through Deepfakes and Voice Clones: Their Potential for Deception
Researchers at Pindrop have published a report looking at consumer interactions with AI-generated deepfakes and voice clones.
It’s Official: Scams Via Email and Text are Inescapable as Nearly Every American Receives Fake Messages Daily
New findings show that the overwhelming majority of people have to sort through scam messages and texts.
Online Scammer Poses as Skype, Swindles Victims Through Cryptocurrency Scam
Researchers at SlowMist describe a phishing campaign that’s distributing a phony version of Skype in order to steal cryptocurrency, …
1 Out of Every 34 Organizations Worldwide Have Experienced an Attempted Ransomware Attack
With organizations globally experiencing an increase in attempted ransomware attacks year over year, new data shows how the global average …
[Holiday Resource Kit] The Holiday Season is Here. How Are You Staying Cyber Safe?
It's the busiest time of year for everyone, especially cybercriminals. They know surges in online shopping, holiday travel and time …
AI Disinformation Exposed: A Fake "Tom Cruise" Attacks the Olympics
Using a page straight out of the KGB playbook, a new AI-driven disinformation attack has been unleashed. The latest victim of this disturbing …
[HEADS UP] FBI Warns About Callback Phishing
In a recent official advisory, the FBI warned about the threat of callback phishing (among other threats). Below is the relevant excerpt.
What Does the Latest SEC Charges Against Solarwinds’ CISO Means for CISOs Everywhere?
In this blog, we'll take a look at the well-known Sunburst attack of 2018 and how the specific charges stemming from this attack will impact …
[INFOGRAPHIC] Original Research: Cybersecurity Challenges Faced by European Infosec Leaders
Cybersecurity threats continue to put European organisations of all sizes at risk. Infosec leaders face multi-pronged challenges, from …
“Skillful Social Engineering of the IT Support Desk” One of the Most Common Tactics in Ransomware Attacks
As ransom payments reach an all-time high, it’s time to look at attacks from a data perspective and find the greatest opportunities to stop …
KnowBe4 Wins Multiple 2023 Best Of Awards From TrustRadius
KnowBe4 is proud to be recognized by TrustRadius for our Security Awareness Training and PhishER platforms in three categories for Best Value …
New Phishing Campaign Abusing .top Domains
A phishing campaign is exploiting a large number of .top domains, according to researchers from WhoisXML API. In an article for CircleID, the …
New York Department of Financial Services Strengthens Cybersecurity Regulation
The NYDFS’ 23 NYCRR Part 500 has been updated to reflect the current preventative and responsive measures necessary for Financial Services org…
New State of Phishing Report 2023: An Alarming Surge in Phishing Threats
The fight against cyber threats remains a top priority for all organizations, including phishing attacks. SlashNext just released its …
Targeted Social Engineering on the Rise With Lowering Phishing-as-a-Service Costs
Targeted individuals were the most common victims of social engineering attacks in the second half of 2022 and the first half of 2023, …
Get Ready: International Fraud Awareness Week
November 12-18, 2024 is International Fraud Awareness Week and I know what you are thinking: “Didn’t we just have an entire month dedicated to…
IT Admins Continue to Use Weak Passwords
In an analysis of web pages identified as admin portals, some incredibly weak passwords were identified – and some of them are going to really…
Spear Phishing Becomes Most Common Attack Technique in Q3 2023
Spear phishing was the most common attack technique in the third quarter of 2023, according to researchers at ReliaQuest.
Healthcare Sector Experiencing Increases in Ransomware, Ransoms and Downtime
An analysis of ransomware attacks on healthcare organizations from 2016 through October of 2023 shows the healthcare sector is likely to …
Small Businesses are Experiencing More Cyber Attacks
As large organizations realize the likelihood of cyber attacks and improve their cyber readiness, small businesses are seeing increases not …
Investigate User-Reported Emails with Ease Through the Powerful Combination of CrowdStrike Falcon Sandbox and KnowBe4 PhishER Plus
The never-ending deluge of phishing emails, malware and ransomware threats can leave incident response and security operation teams (SOC) …
Cybersecurity Expert: AI Lends Phishing Plausibility for Bad Actors
Cybersecurity experts expect to see threat actors increasingly make use of AI tools to craft convincing social engineering attacks, according …
WSJ: "SEC Sues SolarWinds Over 2020 Hack Attributed to Russians"
October 30, 2023 the Wall street Journal broke news that the United States Security and Exchange Commission sued Solarwinds. Here are the …
September Sees a 32% Increase in the Number of Ransomware Attacks in Just One Month
Continued analysis of ransomware attacks shows an upward trend in the number of attacks, with September resulting in the highest number of …
Cybercriminal Group Octo Tempest and Its Menacing Phishbait
Microsoft is tracking a cybercriminal group called “Octo Tempest” that uses threats of violence as part of its social engineering and data …
Exposed: Scam Artists Mimicking PepsiCo in Phishing Schemes
Researchers at INKY warn that a phishing campaign is attempting to distribute malware by impersonating PepsiCo.
The Outstanding ROI of KnowBe4's Security Awareness Training Platform
Let me give you a quick introduction. My name is Stu Sjouwerman (pronounced shower-man). I’m the Founder and CEO of KnowBe4, my 5th startup. I…
The Outstanding ROI of KnowBe4's Trusted Security Awareness Training
Let me give you a quick introduction. My name is Stu Sjouwerman (pronounced shower-man). I’m the Founder and CEO of KnowBe4, my 5th startup. I…
New Amazon-Themed Phishing Campaign Targets Microsoft Live Outlook Users
Several months ago, Netskope Threat Labs uncovered a surge in PDF phishing attachments infiltrating Microsoft Live Outlook. These attacks were…
[Live Demo] Customizing Your Compliance Training to Increase Effectiveness
Linking compliance training to specific outcomes is hard. Compliance training has a reputation for being challenging for organizations to …
Your KnowBe4 Fresh Content Updates from October 2023
Check out the 27 new pieces of training content added in October, alongside the always fresh content update highlights, events and new features.
Celebrating Cybersecurity Awareness Month with KnowBe4: Insights from Our Valued Customers
To celebrate Cybersecurity Awareness Month this year, KnowBe4 customers from various industries and backgrounds are sharing their innovative …
Human-Crafted Phishing Emails Only Three Percent More Successful Than AI-Generated Ones, According To IBM
Red teamers at IBM X-Force warn that AI-generated phishing emails are nearly as convincing as human-crafted ones, and can be created in a …
The Role of AI in Email Security and How Real-Time Threat Intelligence Can Supercharge Your SOC Team
In response to improved email security measures, cybercriminals have pivoted to more advanced attack methods, namely artificial intelligence …
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human …
FBI Warns of North Korean Social Engineering Tactics and Recruitment/Hiring of IT Workers
The U.S. Federal Bureau of Investigation (FBI) and South Korea’s Ministry of Foreign Affairs have issued an advisory offering guidance to “the…
[Cybersecurity Awareness Month] Mindful Defense: Enchantments Against Spear Phishing By Breachatrix le Phish
In the mystical realm of cyberspace, where digital forests hold secrets and virtual owls deliver messages, we find ourselves in a constant …
One Out of Every Eight Emails Found to be Malicious as Attackers Continue to Hone Their Skills
An increase in the number of malicious emails being sent is resulting in more phishing attacks reaching inboxes. New data clarifies the …
Vietnam-Based Cyber Groups Using Fake Job Postings to Deliver Malware
Several cybercriminal groups based in Vietnam are using fake job postings to trick users into installing malware, according to researchers at …
Leadership Less Involved in Cyber-Preparedness Despite a Majority of Orgs Thinking Data Loss from a Cyber Attack Likely in the Next 12 Months
You probably expect executive leadership to not just support cybersecurity efforts, but to be involved. New data shows organizations have a …
Most Organizations Believe Malicious Use of AI is Close to Evading Detection
As organizations continue to believe the malicious use of artificial intelligence (AI) will outpace its defensive use, new data focused on the…
Functionality Misuse from Multiple Legitimate Company Websites is the Latest Example of ‘Site Hopping’
A new technique is becoming increasingly common as a way to bypass security scanners. The challenge is that the specific execution is …
A Brief History of Phishing, and Other Forms of Social Engineering
Social engineering attacks have a very long history, though the Internet has made it easier to launch these attacks en masse, according to …
QR Code Phishing on the Rise: The Alarming Findings From the Hoxhunt Challenge
As the digital landscape continues to evolve, so do the tactics of cybercriminals. The Hoxhunt Challenge, a comprehensive study conducted …
Phishing-as-a-Service: As Simple As Uploading A Logo
Researchers at Fortra are tracking “Strox,” one of the most popular phishing operations of the past two years. Users of Strox phishing kits …
CISA, NSA, FBI, and MS-ISAC Release Phishing Prevention Guidance
October 18, 2023, the Cybersecurity Infrastructure and Security Agency (CISA), the National Security Agency (NSA), the Federal Bureau of…
Phishing Attacks Surge By 173% In Q3, 2023; Malware Threats Soar By 110%
A new report from Vade Secure has found that phishing attacks rose by 173% in the third quarter of 2023, while malware threats have increased …
[Cybersecurity Awareness Month] How To Stop the Ransomwolf Attacks: Similarities to the Werewolves Terrors
Imagine a monstrous entity emerging from the shadows to prey on vulnerable organizations, leaving havoc in its wake. No, we are not talking …
Cyber Insurers Notes Ransomware Claims Rose Significantly in the First Half of 2023
Cyber insurers are claiming that cybercriminals made ransomware attacks popular again in 2023 after a slight break in 2022.
Summit Sabotage: Malicious Phishing Campaign Hits Female Political Leaders Using Social Engineering
A threat actor dubbed “Void Rabisu” used social engineering to target attendees of the Women Political Leaders (WPL) Summit that was held in …
Phishing Tests Start The Virtuous Cycle Of A Strong Security Culture
Phishing tests are the catalyst to achieve a sustainable security culture within your organization. They are actually the start of a virtuous …
Exponential Deepfake Porn is Out of Control And a Huge Security Risk
This year, the world of deepfake pornography is growing at an alarming rate, thanks to advances in AI and ML. Deepfakes make it look like …
Subscribe to CyberheistNews, Now Available on LinkedIn!
We're so excited to announce that CyberheistNews is now available on LinkedIn!
9 in 10 CISOs Report at Least One Disruptive Cyberattack in the Last Year
A new report sheds light on whether CISOs have been the victim of a cyber attacks, if they're every paid a ransom, their greatest cyber …
60% of Organizations are Very Concerned About the Potential Impact of Ransomware Attacks
As the number of reported ransomware attacks increases, new data provides a fresh look at how ready organizations are for ransomware attacks.
53% of Organizations Experienced Cyber Attacks
As increasing percentages of businesses experience cyberattacks, new data provides details on where the most organizational risk lies.
Should You Use Controversial Simulated Phishing Test Emails?
The Wall Street Journal recently published an article about using highly-emotionally charged, “controversial”, subjects in simulated phishing …
KnowBe4 Named a Leader in the Fall 2023 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR)
We are excited to announce that KnowBe4 has been named a leader in the Fall 2023 G2 Grid Report for Security Orchestration, Automation, and …
New Research: Phishing Remains the Most Popular Technique for Bad Actors
A report from Trustwave notes that phishing remains one of the most popular and effective techniques for attackers to gain access to …
Beware of Bogus Roborock Retailers: The Perils of Misleading URLs in E-Commerce
Roborock's online storefronts have been used for cybercrime schemes in the past, and it seems attackers are continuing to create fake online …
“Human-Operated” Ransomware Attacks Double in the Last Year
As attackers leave little-to-no traces of their attack patterns, more ransomware groups are shifting from automated attacks to manual attacks.
Harvested Credentials Are Put Up for Sale Monthly on the Dark Web at a Rate of 10,000 a Month
Credential harvesting has become a business in and of itself within the cybercrime economy. New insight from Microsoft details the types of …
New Cyber Attack Techniques Will Not Replace Old-School Social Engineering
Even though there are new attack types for cybercriminals, they are still leveraging old-school attack vectors. Why? Because they still work.
Business Email Compromise Attempts Skyrocket in the Last Year
Threat actors launched 156,000 business email compromise (BEC) attempts per day between April 2022 and April 2023, according to Microsoft’s …
[INFOGRAPHIC] KnowBe4’s SecurityCoach: Top 10 Integrations
Real-time security coaching helps improve your organization’s security culture by enabling real-time coaching of your users in response to …
KnowBe4 Named a Leader in the Fall 2023 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares security awareness training (SAT) …
[Cybersecurity Awareness Month] Password Security: Do Not Get Bit by Count Hackula
Our login credentials of a username and password are sometimes all that stands between our personal identifiable information and …
[DISINFORMATION ALERT] Israel-Hamas war causes deluge of dis- and misinformation
Social media, and it seems particularly X (former Twitter) seems to drown in an almost instant deluge of disinformation caused by the …
Smishing Triad Threat Actor Sets Its Sights on the UAE
Resecurity warns that the Smishing Triad threat actor has “vastly expanded its attack footprint” in the United Arab Emirates (UAE).
74% of CEOs Concerned About Their Organization's Ability to Protect Against Cyber Attacks, Despite Seeing Cybersecurity as Critical
According to the recent The Cyber-Resilient CEO report released by IT services and consulting agency Accenture, a staggering 74% of CEOs have …
Register for KB4-CON EMEA 2023 Now!
Exciting news, registration for KB4-CON EMEA 2023 is open!
Ransomware Attack Dwell Time Drops by 77% to Under 24 Hours
As attackers evolve their toolsets and processes, the significant drop in dwell time signifies a much higher risk to organizations that now …
One Out of Five Organizations Must Improve Their Security Posture to be Eligible for Cyber Insurance
As insurers become more educated on what a “secure organization” looks like, they are tightening their requirements that puts the onus on …
Healthcare Industry Witnesses 279% Increase in Business Email Compromise Attacks in 2023
The massive uptick in business email compromise (BEC) is considered one of the costliest attack types, requiring organizations to put …
Energy Sector Experiences Three Times More Operational Technology Cybersecurity Incidents Than Any Other Industry
While industries like financial services and healthcare tend to dominate in IT attacks, the tables are turned when looking at Operational …
Stay a Step Ahead of your #1 Downtime Threat - Business Email Compromise
A new report from Secureworks has found that business email compromise (BEC) remains “one of the most financially damaging online crimes …
The Role of AI in Email Security and How Real-Time Threat Intelligence Can Supercharge Your SOC Team
In response to improved email security measures, cybercriminals have pivoted to more advanced attack methods, namely artificial intelligence …
Clorox Experiences Significant Financial Loss Stemming From Recent Cyber Attack
Popular American global manufacturer of cleaning products Clorox stated that recent sales and profit loss to a cyber attack.
[New Report] Over Half of Phishing Emails Use Obfuscation
A new report shows staggering phishing trends using obfuscation techniques that should make any organization feel worried.
New Gartner Forecast Shows Global Security and Risk Management Spending to Increase by 14% in 2024
Gartner issued a press release that forecasted global security and risk management end-user spending to reach $188.1 billion, along with …
[FREE RESOURCES] Celebrate Cybersecurity Awareness Month This October with our Cyber-Monsters!
Cyber threats can be scary, and for good reason.
Malicious URLs In Phishing Emails: Hover, Click and Inspect Again
The most often recommended piece of anti-phishing advice is for all users to “hover” over a URL link before clicking on it. It is great advice.
Senior Executives Beware: The Rise of EvilProxy Phishing Campaigns
Menlo Security warns that a social engineering campaign is using the EvilProxy phishing kit to target senior executives across a range of …
Open-Source Intelligence (OSINT): Learn the Methods Bad Actors Use to Hack Your Organization
They are out there, watching and waiting for an opportunity to strike; the bad actors who have carefully researched your organization in order…
[Cybersecurity Awareness Month] Spoofy Steve's Business Email Compromise Scams You Need to Watch Out For
Like a ghost, most business email compromise (BEC) scams are able to sneak through most technical defenses and end up in end-user inboxes.
Generative AI and the Automation of Social Engineering Increasingly Used By Threat Actors
Threat actors continue to use generative AI tools to craft convincing social engineering attacks, according to Glory Kaburu at Cryptopolitan.
[HEADS UP] Aurora Police Department Warns of Contactless Payment Processors Scams
If you didn't trust contactless payment processors before, you really won't after hearing about this recent scam.
Lazarus Attack on Spanish Aerospace Company Started with Messages from Phony Meta Recruiters
A recent attack on an undisclosed Spanish aerospace company all started with messages to the company's employees that appeared to be coming …
New SMS Phishing Campaign Impersonating The US Postal Service
DomainTools is tracking an increase in SMS phishing (or “smishing”) campaigns impersonating the US Postal Service (USPS). The text messages …
Security Awareness Is Dead. Long Live Security Awareness
Our actions determine outcomes, not our thoughts, our knowledge, or our intentions.
Your KnowBe4 Fresh Content Updates from September 2023
Check out the 66 new pieces of training content added in September, alongside the always fresh content update highlights, events and new …
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human …
[Heads Up] China Invests Billions in Huge Global Disinformation Campaign
Dustin Volz from the WSJ dropped a huge scoop today. This is rocket fuel infosec budget ammo I would send to my C-suite in a New York minute. …
Ransomware Now Considered a “Crisis” in the Financial Services Sector
A recent panel discussion of banking CISOs and experts at the SIBOS conference focused on the current state of ransomware and what …
It’s Official – Generative AI Has Made Phishing Emails Foolproof
The most basic use of tools like ChatGPT to script out professional-looking emails has all but eliminated improperly written content as an …
Threat Group UNC3944 Continues to See Success Using Text-Based Social Engineering
A new update on UNC3944 group's activities shows how they are evolving their focus squarely on SMiShing credential harvesting attacks that …
Pharma Industry Seeing Reduction in Data Breach Costs, But Still Have Much to Do
Insights from IBM’s Cost of a Data Breach Report on the Pharmaceutical Industry shows that while the overall cost has improved, there are …
Facebook Messenger Becomes the Delivery Mechanism for Infostealer Malware Attack
Millions of business accounts on Facebook are the target of a new malware attack, which is seeing a success rate of 1 out of 70, causing …
Zero-Point Fonts in Phishing Emails
Attackers are using zero-point fonts to make phishing emails appear as though they’ve been verified by security scanners, BleepingComputer …
Cyber Insurance Claims Increased by 12% in First Half of 2023, Attacks More Frequent and Severe Than Ever
The latest cyber claims report from Coalition, a digital risk insurance provider, finds a 12% increase in cyber insurance claims in the first …
[Cybersecurity Awareness Month] Frankenphisher – The Monster of Social Engineering Artificial Intelligence
Imagine an artificial intelligence (AI) system developed by a mad scientist to leverage the full capabilities of Large-Language-Models (LLM).
[HEADS UP] If You're a LastPass User, You May be the Next Phishing Email Target
Cybercriminals are not holding back on LastPass users as a new phishing campaign has recently launched with the intent to steal your data.
New Threat Actor Impersonates the Red Cross to Deliver Malware
Researchers at NSFOCUS are tracking a phishing campaign by a new threat actor called “AtlasCross” that’s impersonating the Red Cross in order …
[LIVE DEMO] Are Your Users Making Risky Security Mistakes? Deliver Real-Time Coaching in Response to Risky User Behavior with SecurityCoach
Do you need an easy, automated way to provide real-time feedback the moment your users make risky mistakes to help reinforce the training …
Exploring the DORA: Key Takeaways from the New EU Financial Sector Risk Regulation
When asked why he robbed banks, Willie Sutton, one of the first fugitives named to the U.S. FBI’s most wanted list, reportedly replied, “Because …
Why BJ Fogg and Daniel Kahneman Are Must-Knows for Every Network Security Pro
You're no stranger to the complexities of safeguarding your organization's digital assets. But have you considered the human element in your …
Ukrainian Military Targeted in Sophisticated Phishing Attack Using Drone Manuals
Securonix is tracking a phishing campaign that’s targeting the Ukrainian military with malware-laden attachments posing as drone instruction …
Practical Insights To Improve Security Awareness in Higher Education
I am a strong believer that understanding cybersecurity as part of an organization-wide process is of the utmost importance.
Deepfakes: The Threat to Reality and How To Defend Against It
Deepfakes have emerged as a serious concern in the digital landscape, presenting a significant threat to truth and trust.
New Wave of Hospitality Phishing Attacks: Compromise User Credentials, Then Go Phish
The hospitality sector is seeing a new wave of phishing attacks. These new attacks are more plausible because they begin with compromised …
Organizations Starting to Understand the Impact of Ransomware, But Their Efforts Not Enough to Overcome Infostealer Malware
Recent findings in a SpyCloud report shows companies are starting to recognize and shift their priorities to defend against ransomware …
MFA Defenses Fall Victim to New Phishing-As-A-Service Offerings
ZeroFox warns that phishing-as-a-service (PhaaS) offerings are increasingly including features to bypass multi-factor authentication.
[NEW RELEASE]: Unleash the Power of Cybersecurity Education with KnowBe4’s 'Hack-A-Cat' on Roblox
What do cheese, fish and cybersecurity training have in common? Each of these comes together to help keep kids informed about cyber threats …
Cybercriminals Use Google Looker Studio to Host Crypto Scam to Steal Money and Credentials
Security researchers at Check Point have discovered yet another attack that leverages legitimate web applications to host attacks in order to …
Tools From Cybercrime Software Vendor W3LL Found to be Behind the Compromise of 56K Microsoft 365 Accounts
A new report uncovers the scope and sophistication found in just one cybercrime vendor’s business that has aided credential harvesting and …
[YIKES] AI Now Enables Subliminal Image "Inception"
Seen Christopher Nolan's movie Inception? If you haven't, it's about a thief who is given the task of planting an idea into the mind of a CEO.…
Chinese Spies Infected Dozens of Networks With Thumb Drive Malware
WIRED just published an article that made me both disappointed and surprised at the same time. Security researchers found USB-based Sogu …
New SEC Rules Add Challenges in Uncertain Cyber Insurance Market
[BUDGET AMMO] Jeremy King is a partner at Olshan Frome Wolosky. He wrote an article for Bloomberg where he analyzed cyber risk management …
Vanishing Act: The Secret Weapon Cybercriminals Use in Your Inbox
Researchers at Barracuda describe how attackers use legitimate email inbox rules to control compromised accounts and evade detection.
Scam-as-a-Service Classiscam Expands Impersonation in Attacks to Include Over 250 Brands
Now entering its third year in business, the phishing platform, Classicam, represents the highest evolution of an “as a service” cybercrime, …
USPS Customers Become the Latest Target of the Chinese Smishing Group Called “Smishing Triad”
A new SMS-based phishing attack uses a smishing kit-as-a-service to impersonate the U.S. Postal Service.
Tighter Policies Mixed with Higher Costs Are Creating a Cyber Insurance Gap
New data on the state of cyber insurance shows that it’s becoming more difficult to get a policy, and the organizations obtaining one share …
TikTok Impersonations of Elon Musk Scam Victims of Their Bitcoin
There’s been a surge of Elon Musk-themed cryptocurrency scams on TikTok, BleepingComputer reports. The scammers inform the victims that they …
Data Breach Costs Rise, But Cybersecurity Pros Still Take Risks
The latest data from IBM shows that the average cost of a data breach has gone up by 2% to a whopping $4.45 million. You would think that in …
China's Cyber Offensive: FBI Director Reveals Unmatched Scale of Hacking Operations
WASHINGTON – In a startling revelation, FBI Director Chris Wray disclosed at a recent conference that China's cyber espionage capabilities are…
Romance Scams That Run Your Crypto Wallet Dry
Scammers are using dating sites to lure victims into phony cryptocurrency investment schemes, according to Sean Gallagher at Sophos.
The International Joint Commission Falls Victim to Ransomware Attack; 80GB Of Data Stolen
The International Joint Commission (ICJ), an organization that handles water issues along the Canada–United States border, was hit by a …
[New PhishER Feature] Immediately Add User-Reported Email Threats to Your M365 Blocklist
Now there's a super easy way to keep malicious emails away from all your users through the power of the KnowBe4 PhishER platform!
Mark Cuban’s MetaMask wallet drained nearly $900,000 in suspected phishing attack
Dallas Mavericks owner and well-known investor Mark Cuban reportedly lost nearly $900,000 in a phishing attack targeting his MetaMask …
The BISO Secret Weapon: Enhancing Collaboration for Cybersecurity and Business Growth with Nicole Dove
Do you want to bridge the gap between IT, cybersecurity, and the business to enhance collaboration and integration? Are you seeking a solution…
91% of Cybersecurity Professionals Have Experienced Cyber Attacks that Use AI
A new report takes an exhaustive look at how cybersecurity professionals see the current and future state of attacks, and how well vendors are…
New Phishing Attack Uses Social Engineering to Impersonate the National Danish Police
A malwareless and linkless phishing attack uses sextortion and the threat of legal action to get the attention of potential victims and get …
Deepfakes More Common So Bolster Your Defenses
The United States FBI, NSA, and CISA have released a joint report outlining the various social engineering threats posed by deepfakes.
New Scam Impersonates QuickBooks to Steal Credentials, Extract Money
Establishing urgency through a false need to “upgrade” or lose services, this new attack takes advantage of the widespread use of the popular …
Microsoft (Once Again) Tops the List of Most Impersonated Brands in 2023
Out of the over 350 brands regularly impersonated in phishing attacks, Microsoft continues to stand out because they provide attackers with …
Board Members' Lack of Security Awareness Puts Businesses at Risk of Cyber Attacks, Finds Savanti Report
A report from cybersecurity consultancy Savanti reveals that board members are facing challenges in understanding cyber risks, and this has …
No Dice for MGM Las Vegas as It Battles Fallout from Ransomware Attack After a 10-minute Vishing Scam
Four days later, $52 million in lost revenues and counting, a cyber attack on MGM Resorts International, a $14 billion Las Vegas gaming empire…
MGM Suffers Ransomware Attack that Started with a Simple Helpdesk Call
As the aftermath unfolds, the details around the recent attack on MGM Resorts, providing crucial insight into the attacks impact, who’s …
Can Someone Guess My Password From the Wi-Fi Signal On My Phone?
Cybercriminals can't ascertain your phone password just from a Wi-Fi signal, but they can come close according to a method described in a …
Can You Guess Common Phishing Themes in Southeast Asia?
Researchers at Cyfirma outline trends in phishing campaigns around the world, finding that Singapore is disproportionately targeted by …
AP Stylebook Data Breach Compromises Customer Personal Information
The Associated Press (AP) has disclosed a data breach affecting the legacy AP Stylebook website that led to phishing attacks against impacted …
Phishing Scammers are Using Artificial Intelligence To Create Perfect Emails
Phishing attacks have always been detected through broken English, but now generative artificial intelligence (AI) tools are eliminating all …
Cybercriminals Selling "Golden Tickets" to Phish Microsoft 365... $500,000 in Sales in 10 Months
In the movie, "Willy Wonka and the Chocolate Factory," kids unwrap chocolate bars in hopes of winning a golden ticket, giving the holder an …
Microsoft Teams Phishing Campaign Distributes DarkGate Malware
Researchers at Truesec are tracking a phishing campaign that’s distributing the DarkGate Loader malware via external Microsoft Teams messages.
[dot]US Domain Exploited for Phishing
The Interisle Consulting Group has published a paper looking at the phishing landscape in 2023, KrebsOnSecurity reports. Notably, Interisle …
Organizations Tie Executive Pay to Cybersecurity Performance Hoping To Enhance Protection Against Hackers
Organizations have started to recognize the importance of tying executive pay to cybersecurity metrics. This practice is gaining traction …
New Telekopye Phishing Toolkit Uses Telegram-Based Bots To Turn Novice Scammers into Experts
The Telekopye toolkit allows scammers to create phishing websites, send fraudulent SMS messages and emails, and target popular Russian and …
Brand Impersonation Hits a New High with as Many as 73 Lookalike Domains Per Brand
The use of lookalike domains has reached critical mass with not just one counterfeit website, but many.
Ransomware Attacks Speed up 44% Leaving Less Time for Detection and Response
New data suggests that the gangs and toolkits behind current ransomware attacks are materially improving their abilities, resulting in a …
Hacking Your Digital Identity: How Cybercriminals Can and Will Get Around Your Authentication Methods
Inadequate authentication measures leave your digital identity vulnerable to cybercriminals. Tools like multi-factor authentication, …
Social Engineering Seeks Okta Credentials
Identity and authentication management provider Okta has warned of social engineering attacks that are targeting IT workers in an attempt to …
CISA Says to Exercise Caution For Disaster-Related Malicious Scams
The US Cybersecurity and Infrastructure Security Agency (CISA) has warned that scammers are exploiting the recent hurricanes that have hit the…
How Secure Is Your Authentication Method?
I frequently write about authentication, including PKI, multi-factor authentication (MFA), password managers, FIDO, Open Authentication, and …
Nearly One-Quarter of Financial-Themed Spam Emails are Phishing Attacks
While spam tends to be dismissed as being more an annoyance, new research shows that there is a very real and ever-present threat in emails …
Cyberattacks Targeting Government Agencies and Institutions Increases in Q2 by 40%
New data shows a massive uptick in attacks across all industries, but a particularly worrisome growth in interest in targeting the public …
New “Early Warning” System in the U.K. Tips Off Ransomware Targets
British Intelligence has come up with a potentially very effective means to disrupt ransomware attacks, but there seems to still be a few …
New Adversary in the Middle Platform Circumvents MFA Protections “At Scale”
As Phishing as a Service (PhaaS) kits continue to evolve, news like recent attacks using the Greatness toolkit demonstrate how easy it is for …
You Asked and Here It Is! KnowBe4's New Content Manager Feature is Unveiled
We heard you, and we're thrilled to tell you about the all-new Content Manager feature for KMSAT!
Labor Day Alert: Mobile Phishing Attacks on the Rise for Remote Employees
A recent survey by Lookout, Inc. warns for a specific attack vector as Labor Day approaches. The study shows that 85% of enterprise employees …
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human …
Customers of Cryptocurrency FTX are Target of Phishing Emails
Customers of the bankrupt cryptocurrency exchange FTX are already receiving phishing emails following a breach of personal data held by …
Open Redirect Flaws: The Newest Phishing Trick
No surprise: phishing attacks are on the rise, and a new technique is becoming increasingly popular: open redirect flaws. These flaws allow …
Quishing: QR Codes as Phishbait
Researchers at Trustwave are tracking an increase in the use of QR codes to spread phishing links.
Case Study: LoanLogics Combined Compliance & Security Awareness Training to Improve Security Culture
In the drive to build a strong security culture, security awareness and compliance training should work hand in hand.
Trends in Business Email Compromise
Researchers at Trustwave have published a report outlining trends in business email compromise (BEC) attacks, finding that these attacks …
Use KnowBe4’s New Callback Phishing Feature to Boost Your Organization's Security Awareness
What's the Deal with Callback Phishing?
Your KnowBe4 Fresh Content Updates from August 2023
Check out the 21 new pieces of training content added in August, alongside the always fresh content update highlights, events and new features.
Duolingo Users Should Be on the Lookout for Targeted Phishing Attacks
Users of the language learning app Duolingo should be wary of targeted phishing attacks following a recent data leak, according to Anthony …
Data Breaches Involving Social Engineering Attacks Take Longer to Identify and Contain
Continuing coverage of IBM’s recently-released Cost of a Data Breach report, we focus on the impact attacks involving social engineering have …
Ransomware Attacks Rise 69% and 1500 Organizations Feel the Hurt
A new report from Rapid7 has found that the number of ransomware attacks increased by 69% in the first half of 2023. Rapid7 incident response …
Social Engineering Is the Number One Cybersecurity Problem by Far
The number one way that hackers and malware compromise people, devices, and networks is social engineering. No one argues that anymore, but it…
LinkedIn Deception: How a Chinese Spy Tricked Thousands of UK Officials
In last few years, cyber espionage has taken a new form. A recent investigation by The Times has unveiled a Chinese intelligence officer's …
Phishing Tops the List as the Most Costly Initial Attack Vector in Data Breaches
After you come to grips with the massive average cost of a data breach to an enterprise organization measured in the millions, it’s time to …
Data Breach Costs in Healthcare Rise 53% to More than Double the Average
It appears that one of the most regulated industries also holds the title for the highest average data breach costs – coming in at just under …
Deceptive Links, Brand Impersonation, and Identity Deception Top the List of Phishing Attack Tactics
As phishing attacks continue to dominate as an initial attack vector, new data shows that attackers maintain the use of tried-and-true …
Phishing Campaigns Targeting Microsoft Login Credentials Jump an Unprecedented 6100%
Monitoring of traffic to phishing pages hosted on the free hosting service Cloudflare R2 show an unheard of spike of 6100%, many going …
Scammers Impersonate the Australian Tax Office
The Australian Taxation Office (ATO) has warned of an increase in SMS and email phishing attacks targeting taxpayers, News.com.au reports. The…
[Eye-Opening] Increase of Phishing Attacks in Australia Should Alarm Organizations
Phishing attacks are on the rise in Australia, the Australian Broadcasting Corporation (ABC) reports.
Bloomberg Reports: Stealth QR Code Phishing Attack On Major US Energy Company
During my two years as the CEO of a Public Company, Bloomberg became one of my go-to sources for financial news. I am still subscribed and …
Not Another Voter Registration Scam (But It Looks Like One)
The UK government’s voter registration website is causing confusion again, according to Ax Sharma at BleepingComputer. The site, hosted at a …
Ransomware Attacks Surge as Generative AI Becomes a Commodity Tool in the Threat Actor’s Arsenal
According to a new report, cybercriminals are making full use of AI to create more convincing phishing emails, generating malware, and more to…
Online Scams Targeting Individuals Double in a Single Quarter as Global Risk Rises
New analysis of the second quarter of this year makes it clear that individuals and organizations alike are at an increasing risk of web- and …
Social Media Platforms Become Half of all Phishing Attack Targets
Social platforms are the current favorite target of cybercriminals, displacing financial institutions, providing cybercriminals with …
Cybercriminals May Already Have Hacked Your LinkedIn Account
New reports show many LinkedIn users have reported complaints about accounts being taken over by bad actors.
Ransomware's Paradox: Why Falling Monetization Rates Are Accompanied by Soaring Ransom Payments - A Must-Read Analysis.
Grab a cup of coffee, and let's talk about something that's been making waves in the cybersecurity world: ransomware. You've probably heard …
Ransomware Distributed by Fake Tripadvisor Reviews
The Knight ransomware-as-a-service offering (formerly known as “Cyclops”) is using phony TripAdvisor complaints to deliver its malware, …
[FREE RESOURCE KIT] Cybersecurity Awareness Month Kit 2023 Now Available
Get the resources you need to help keep your users safe from malicious social engineering attacks during this year's Cybersecurity Awareness …
KnowBe4 Celebrates Winning a Tech Cares Award From TrustRadius 2023
For the fourth consecutive year, we received a Tech Cares Award from TrustRadius! This fourth annual award celebrates companies that have gone…
Beware of Clickbait PDF Phishing Attacks Lurking in Search Results
We previously reported independently on PDF-based phishing attacks skyrocketing and the rise of SEO attacks. A recent research study found …
Gootloader Malware Uses Social Engineering to Target Law Firms (or their Clients)
Law firms are being targeted by a large number of social engineering attacks involving the Gootloader malware delivery tool, according to …
AI's Role in the Next Financial Crisis: A Warning from SEC Chair Gary Gensler
TL;DR - The future of finance is intertwined with artificial intelligence (AI), and according to SEC Chair Gary Gensler, it's not all …
[Live Demo] Boost Your Email Security Defense - PhishER Plus to the Rescue!
Now there's a super easy way to keep malicious emails away from all your users through the power of KnowBe4 PhishER Plus!
Be Aware of SEO and Waterhole Attacks
Most social engineering scams search out their potential victims, often sending emails to known email addresses, sending chat messages to them…
Number of Named Ransomware Victim Organizations Jumps 64% in One Quarter
The second quarter of this year has become the focus of some new firsts in ransomware attacks, according to new data from cybersecurity vendor…
Salesforce Becomes the Latest Platform to Unwittingly Aid Phishing Scammers
Cybercriminals used the legitimacy of Salesforce’s email gateway to bypass security scanners and target Meta customers in an effort to steal …
Comcast: 9 out of 10 Attempts to Breach Customer Networks Start with a Phish
The latest data from Comcast Business’ analysis of over 23.5 billion cyber attacks on their business customers shows the importance and role …
AI's Role in Cybersecurity: Black Hat USA 2023 Reveals How Large Language Models Are Shaping the Future of Phishing Attacks and Defense
At Black Hat USA 2023, a session led by a team of security researchers, including Fredrik Heiding, Bruce Schneier, Arun Vishwanath, and Jeremy…
Black Hat: "Five cyber phases of Russia's hybrid war"
The Cyberwire reported: "Victor Zhora, deputy chairman and chief digital transformation officer at Ukraine's State Service of Special …
Australians Reporting Alarming Number of Losses to Vishing and Smishing Scams
We know that scam calls (aka vishing) and scam SMSs (aka smishing) are out of control, and for most unaware Australians, they continue to …
Record ¥3 bil stolen via phishing in Japan in 1st half of 2023
A record 2,322 scams in Japan to steal internet banking IDs and passwords have resulted in unauthorized money transfers totaling a record of …
Wordfence Becomes the Latest Brand to be Impersonated Putting 800 Million Sites at Risk
With its wide use and trusted state among WordPress developers and website admins, a new campaign impersonating the website security brand …
New PCI Password Requirements Could Be the Impetus for Credential Harvesting Scams
As the retirement countdown for the current version of PCI is now less than six months, a new standard for password length, complexity, and …
Scammers Exploit Twitter’s Transition to “X”
Scammers are taking advantage of Twitter’s rebranding to “X,” according to Stephanie Adlam at Gridinsoft. A phishing campaign is targeting …
KnowBe4’s Interactive Phishing Analysis Center: Keep Your Finger On The Pulse
As a security awareness practitioner, keeping your pulse on industry - and geographical - benchmarking data and best practices is always a …
Most Organizations Using Weak Multifactor Authentication
Most organizations are still using weak forms of multi-factor authentication (MFA), a survey by Nok Nok has found. These forms of MFA can be …
5 Intriguing Ways AI Is Changing the Landscape of Cyber Attacks
In today's world, cybercriminals are learning to harness the power of AI. Cybersecurity professionals must be prepared for the current threats…
[INFOGRAPHIC] Q2 2023 Top-Clicked Phishing Test Results Favor HR-Related Subjects
KnowBe4's latest reports on top-clicked phishing email subjects have been released for Q2 2023. We analyze 'in the wild' attacks reported via …
GitHub Warns of Social Engineering Campaign Targeting Employees in the Technology Industry
A few weeks ago, GitHub posted on their blog a recent security alert that should have any organization in the tech industry worried.
Fraud Masquerades as Anti-Fraud
Many of us have received a phone call or other notification from a credit card company telling us that they’ve detected suspicious activity on…
Data Theft Extortion Attacks Rise 25 Percent in Just One Quarter and Take Top Attack Spot
A recap of Q2 from Cisco Talos’ incident response services provides insight into exactly what kinds of attacks are being seen in the field, …
Vendor Email Compromise Attacks Use the Same Playbook for Multiple Attacks
Seeking very large paydays, Vendor Email Compromise (VEC) threat actors are finding out what works and repurposing their content and processes…
Phishing Attacks Continue to Use Attachments as HTML Files Containing Java Dominate
As traditional phishing attack attachment types like Office documents dwindle in use, threat actors look for new effective ways to use email …
[New Product] Supercharge Your Anti-Phishing Defense with KnowBe4’s PhishER Plus!
Staying one step ahead of cybercriminals is absolutely vital in today’s threat landscape. That's why we're thrilled to introduce PhishER Plus,…
WIRED: "This Disinformation Is Just For You."
WIRED just came out with an article that spells out the coming tsunami of highly targeted disinformation. here is a short summary and the …
New AI Bot FraudGPT Hits the Dark Web to Aid Advanced Cybercriminals
Assisting with the creation of spear phishing emails, cracking tools and verifying stolen credit cards, the existence of FraudGPT will only …
Russian Hackers Breached Government Agencies' MFA Using Microsoft Teams: Is Your Business Next?
Microsoft's recent blog post raised eyebrows through the cybersecurity community. State-backed hackers linked to Russia, known as APT29 or …
Boarding Pass Selfies and Cybersecurity Don't Mix
There is no such thing as a vacation for cybercriminals. We recently released our top summer cybersecurity travel tips to help keep you safe. …
Advanced Phishing Campaign Exploits 3rd Parties
Researchers at BlueVoyant warn that attackers are increasingly adding an extra step to their phishing campaigns, impersonating third-parties …
The Dark Side of AI: Unmasking its Threats and Navigating the Shadows of Cybersecurity in the Digital Age
Artificial Intelligence (AI) has come roaring to the forefront of today’s technology landscape. It has revolutionized industries and will …
The Urgent Need For Cyber Resilience in Healthcare
A US hospital closed two years after a ransomware incident, highlighting that the health sector continues to be under threat.
KnowBe4 Chooses Drata as Their Exclusive GRC Partner
Drata is KnowBe4’s preferred compliance automation platform for KnowBe4 customers.
Bad Actor Uses Fake Android Chat to Install Malware
Researchers at CYFIRMA warn that the Bahamut threat actor is using a malicious Android app to deliver malware.
A Long-Running Credential Phishing Expedition
Researchers at Akamai describe a credential phishing campaign that’s been running since at least March 2022. Due to the volume of traffic to …
Amazon Sends Email to Customers on Common Scam Tactics
We've reported on several Amazon scams, but for once, there is positive news. Amazon sent an email Thursday morning highlighting the top scams…
CISA Discovers Spear Phishing and Valid Account Compromise Are the Most Common Attack Vectors
The US Cybersecurity and Infrastructure Security Agency (CISA) has found that compromise of valid accounts and spear phishing attacks were the…
Heads Up: Google Inactive Account Deletion Notifications
Google announced an update to their inactive account policies in May. Accounts that have been inactive for a period of two years or more will …
Researchers uncover surprising method to hack the guardrails of LLMs
Researchers from Carnegie Mellon University and the Center for A.I. Safety have discovered a new prompt injection method to override the …
Your KnowBe4 Fresh Content Updates from July 2023
Check out the 28 new pieces of training content added in July, alongside the always fresh content update highlights, events and new features.
SEC Implements New Rule Requiring Firms to Disclose Cybersecurity Breaches in 4 Days
What happened? The SEC (Securities and Exchange Commission) has introduced new rules that require public companies to be more transparent …
Facebook Scams Impersonate AI Tools
Fraudsters are spreading scams on Facebook that pose as ads for legitimate AI tools, according to researchers at Check Point. The Facebook …
Russia-Based Global Cybersecurity Vendor Group-IB Exits the Russian Market
Amid potential concerns by governments, customers, and prospects about ties with the Russian government, the cybersecurity vendor Group-IB …
Phishing Email Attack Numbers “Decline” While Malware Volumes Increase 15%
New data focused on the first half of the year shows some anomalies. Phishing attacks are slowing down… that is, until you dive into the …
How KnowBe4 Can Help You Fight Spear Phishing
This blog was co-written by KnowBe4's Data-Driven Defense Evangelist Roger A. Grimes and Chief Learning Officer John Just. Social engineering…
[Live Demo] Customizing Your Compliance Training to Increase Effectiveness
Linking compliance training to specific outcomes is hard. Compliance training has a reputation for being challenging for organizations to …
New IBM report reveals the cost of a data breach now tops $4.45 million
IBM Security has released its annual Cost of a Data Breach Report, revealing that the global average cost of a data breach reached $4.45 …
Barbie-Related Scams Emerge After Recent Movie Release
Scammers are taking advantage of the popularity of the Barbie movie, according to researchers at McAfee.
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human …
The Secret's Out: Researchers Reveal Backdoor in Emergency Radio Encryption
For over 25 years, a technology utilized for vital data and voice radio communications globally has remained under wraps, preventing in-depth …
Phony Browser Updates Deliver NetSupport Trojan Using Social Engineering Tactics
A new social engineering campaign tracked as “FakeSG” is distributing the NetSupport remote access Trojan (RAT) via phony browser updates, …
FBI Warns of Increased Tech Support Scams Using Snail Mail
The US Federal Bureau of Investigation (FBI) has warned of an increase in tech support scams that attempt to trick users into sending cash via…
Save $200 on Your Security Awareness and Culture Professional (SACP) Certification
H Layer Credentialing is launching an updated exam form with new content and they need YOUR help! They are looking for professionals …
Microsoft was the Most Impersonated Brand in Q2, 2023
Microsoft was the most impersonated brand in phishing attacks during Q2, 2023, according to Check Point’s latest Brand Phishing Report.
European Union Healthcare Sees the Number of Cyber Incidents Double in 2023
A new report focused on the healthcare sector sheds light on the state of cyber attacks in the European Union, including the types of attacks,…
Business Email Compromise Now Has a $50 Billion Price Tag
The latest data from the FBI’s Internet Crime Complaint Center (IC3) ups the estimate for the cost of losses and exposure through business …
The Number of Data Compromises Jumps 50% in H1 2023, Outpacing Every Year on Record
New data from the Identity Theft Resource Center (ITRC) covering the first half of this year shows a significant rise in the number of …
Kevin David Mitnick (Aug 6, 1963 - July 16, 2023)
The only constant is change. That is true for physics, for organizations, and for us humans. People join and leave teams, and of course also …
Threat Actors Add ".Zip" Domains to Phishbait
Cybercriminals are exploiting the introduction of “.ZIP” as a new generic Top-Level Domain (gTLD) to launch phishing attacks, according to …
[INFOGRAPHIC] KnowBe4’s Content Library by the Numbers
KnowBe4 offers the world’s largest library of always-fresh security awareness and compliance training content that includes assessments, …
WormGPT, an "ethics-free" Cyber Crime text generator
CyberWire wrote: "Researchers at SlashNext describe a generative AI cybercrime tool called “WormGPT,” which is being advertised on underground…
[LIVE DEMO] Are Your Users Making Risky Security Mistakes? Deliver Real-Time Coaching in Response to Risky User Behavior with SecurityCoach
Do you need an easy, automated way to provide real-time feedback the moment your users make risky mistakes to help reinforce the training …
KnowBe4 Wins 2023 Top Workplaces for Technology Award
KnowBe4 ranks number one overall on the 2023 Technology Top Workplaces list for the third consecutive year and earns national recognition as …
Ransomware Crypto Payments Are on the Rise While the Rest of Crypto Crime is on the Decline
New insight from blockchain analysis company, Chainalysis, shows that activity involving known ransomware crypto addresses has grown over the …
Nearly One-Quarter of All Emails Are Considered to be Malicious
The quantity of emails involved in scams and cyber attacks continues to grow as credential theft and response-based phishing persist as top …
Banking Detail Malvertising Attack Disguises Itself as a Foolproof USPS Google Ad
A new scam aimed at stealing your credit card and banking information has reared its’ ugly head as a completely legitimate ad that is likely …
[Discovered] An evil new AI disinformation attack called 'PoisonGPT'
PoisonGPT works completely normally, until you ask it who the first person to walk on the moon was.
Tailgating Through Physical Security Using Social Engineering Tactics
Researchers at Check Point outline various forms of tailgating attacks. These attacks can allow threat actors to bypass physical security …
Two-Thirds of Ransomware Attacks Against Manufacturing Resulted in Encrypted Data
As the rate of ransomware attacks steadily increased over time, there are clear indicators as to how these attacks are starting and, …
Phishing Attacks Employing QR Codes Are Capturing User Credentials
Using a new twist to bypass detection from security solutions, cyber attacks are now employing what will be construed as a benign image whose …
Launch Of New Meta Thread App Spawns Hundreds Of Spoof Domains
Researchers at Veriti have observed hundreds of spoofed domains following Meta’s launch of its Threads social media platform.
Three Key Takeaways From the Newly Adopted EU-US Data Privacy Framework You Need To Know
On July 10th, the EU Commission adopted anadequacy decision for the proposed EU-U.S. Data Privacy Framework. This is exciting news for …
Phishing Campaigns Are Now Targeting the Hospitality and Tourism Ponds
A phishing campaign is targeting the tourism and hospitality industries, according to researchers at Votiro.
Australia’s National Anti-Scam Centre: Prevention Is Better Than the Cure
Australia officially launched their National Anti-Scam Centre this week. With more than AUD $3.1 billion lost each year, Australians need …
Job Recruitment Scams Rising Due to Social Engineering
Job scams are a rising form of socially engineered cybercrime. And while it’s easy to imagine the trouble they cause individuals who …
New Phishing Benchmarks Unlocked: Is Your Organization Ahead of the Curve in 2023
Cybercriminals continue to rely on proven attack methods while developing new ways to infiltrate digital environments and break through your …
The Number of Phishing Attack Cases in Singapore Jump by 185%
The latest data provided by the Singapore Cyber Emergency Response Team (SingCERT) shows the number of attacks trending in the wrong …
U.K. Twitter Impersonation Hacker Sentenced to Prison in the U.S.
The British national responsible for hacking into and impersonating high-profile individuals as part of a crypto theft scheme has been …
Free Unsolicited Smartwatch in the Mail and I’m in the Military? What Could Possibly Go Wrong???
From the “shaking our heads” files comes the story of how threat actors compromised military personnel mobile devices, credentials, accounts …
Camaro Dragon APT Group Continues to Employ USB Devices as Initial Attack Vector
Apparently expanding efforts outside of Southeast Asian countries, this threat group’s known malware has shown up in a European healthcare …
Email-Based Cyber Attacks in Europe Increase 7-Fold in Just One Year
An abnormally massive focus on business email compromise attacks in Europe has fueled an equally large growth in overall email attacks there, …
Amazon Prime Day Alert: Beware of Fake Logins, Gift Card Scams
A new threat alert from ConsumerAffairs and TrendMicro proves more than just shoppers will take advantage of Amazon’s upcoming Prime Day.
Microsoft Teams Cyber Attack Exploit Tool Relies on Social Engineering to Deliver Malware
If your organization uses Microsoft Teams, then you definitely want to hear about a new way bad actors are exploiting this newly discovered …
New Report Shows Social Engineering and Business Email Compromise Attacks Have Drastically Increased in 2023
Email-based social engineering attacks have risen by 464% this year compared to the first half of 2022, according to a report by Acronis. …
Nerve Center: Protect Your Network Against New Ransomware Strains with Our Latest RanSim Update
Ransomware continues to be a major threat for all organizations and, according to the Verizon 2023 Data Breach Investigations Report, is still…
Threat Actors are Using Image-Based Phishing Emails to Lure Victims
Attackers are increasingly using images in phishing to evade text-based security filters, according to researchers at INKY.
Japan's Largest Port is the Latest Victim of a Ransomware Attack
The largest port in Japan, Nagoya, is now the most recent victim of a ransomware attack.
CyberheistNews Vol 13 #27 [Heads Up] Massive Impersonation Phishing Campaign Imitates Over 100 Brands and Thousands of Domains
CyberheistNews Vol 13 #27 | July 5th, 2023 [Heads Up] Massive Impersonation Phishing Campaign Imitates Over 100 Brands …
KnowBe4 Named a Leader in the Summer 2023 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR)
We are excited to announce that KnowBe4 has been named a leader in the Summer 2023 G2 Grid Report for Security Orchestration, Automation, and …
KnowBe4 Named a Leader in the Summer 2023 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares Security Awareness Training (SAT) …
The Better Business Bureau Warns of Process-Server Phishbait
The Better Business Bureau (BBB) has warned of a scam in which attackers pose as process servers in order to steal information and commit …
[FREE Resource Kit] July Is Ransomware Awareness Month
July is Ransomware Awareness Month, and we’ve got you covered with free resources!
Your KnowBe4 Fresh Content Updates from June 2023
Check out the 34 new pieces of training content added in June, alongside the always fresh content update highlights, events and new features.
Use of Crypto Mining Pools to Launder Ransom Funds Grows 100,000% Over 5 Years
New analysis shows sources of cryptocurrency being placed into mining pools with huge deposits that make it easier for cybercriminals to make …
HTML Files Top the List as the Most Commonly Used Malicious Attachment
As executables and scripts are unable to bypass security solutions as attachments, cybercriminals turn to HTML as a means of obfuscation and …
Iranian Threat Actor Charming Kitten Using Spear Phishing Campaign To Distribute Malware
The Iranian threat actor Charming Kitten is launching sophisticated spear phishing attacks to distribute a new version of its POWERSTAR …
The face of 2023's cyber-threat landscape was an alarming surge in ransomware and phishing attacks
When KnowBe4 went public in April 2021, I got to know a select group of analysts that served as co-managers on our IPO. These professionals …
National Cyber Security Centre Notes UK Law Firms are Main Target for Cybercriminals
In the most recent Cyber Threat report from the National Cyber Security Centre (NCSC), it is clear that UK law firms are a gold mine for …
Newly Discovered Phishing Attacks Target Bank Customers
First National Bank has warned of an increase in phishing and smishing attacks, IT-Online reports.
Massive Impersonation Phishing Campaign Imitates over 100 Brands and Thousands of Domains
A year-long phishing campaign has been uncovered that impersonates 100+ popular clothing, footwear, and apparel brands using at least 10 fake …
CyberheistNews Vol 13 #26 [Eyes Open] The FTC Reveals the Latest Top Five Text Message Scams
CyberheistNews Vol 13 #26 | June 27th, 2023 [Eyes Open] The FTC Reveals the Latest Top Five Text Message Scams The U.S. …
Russian Threat Actor Targets Ukraine Government And Military With Spear Phishing Emails
Russia’s APT28 (also known as “Fancy Bear” or “BlueDelta”) is using spear phishing to compromise Ukrainian government and military entities, …
New Singapore Cyber Landscape 2022 Report Shows Russia-Ukraine Conflict, Phishing and Ransomware Attack Increases, and Much More
The “Singapore Cyber Landscape (SCL) 2022” reviews Singapore’s cybersecurity situation in 2022 against the backdrop of global trends and …
Unleashing the Power of Incident Reporting: Strengthening Security and Compliance
Whether it is reporting a phishing email or something that might be illegal that a coworker is doing, your employees should be a strong last …
New Cryptocurrency Coinbase Phishing Campaign Uses Social Engineering
A phishing campaign is impersonating cryptocurrency trading platform Coinbase, Tech.co reports. Crypto trader Jacob Canfield described the …
SolarWinds' Head Refuses to Back Down Amid Potential US Regulatory Action over Russian hack
According to an internal email obtained by CNN, the CEO of SolarWinds informed employees on Friday that the company plans to vigorously defend…
Want To Stop All Scams? Here Is How!
There are many ways to be socially engineered and phished, including email, websites, social media, SMS texts, chat services, phone calls and …
“Picture in Picture” Phishing Attack Technique Is So Simple, It Works
Using credibility-building imagery and creating a need for the user to click what may or may not be perceived as an image is apparently all it…
Banking and Retail Top the List of Industries Targeted by Social Media Phishing Attacks
Using an external platform trusted by potential victims is proving to be a vital tool in the cybercriminal’s arsenal. New data shows the state…
Half of Business Leaders Believe Users Aren’t Security Aware, Despite Most Having a Program in Place
New data shows that even with the majority of organizations experiencing cyber attacks, three hours of security awareness training simply …
Extremely Persistent Threat Group Demonstrates a Strong Understanding of the Modern Incident Response Frameworks
A threat actor tracked as “Muddled Libra” is using the 0ktapus phishing kit to gain initial access to organizations in the software …
Is AI-Generated Disinformation on Steroids About To Become a Real Threat for Organizations?
A researcher was alerted to a fake website containing fake quotes that appeared to be written by himself. The age of generative artificial …
The FTC's 5 Most Common Text Scams
The U.S. Federal Trade Commission (FTC) has published a data spotlight outlining the most common text message scams in 2022. Phony bank fraud …
KnowBe4’s 2023 Phishing By Industry Benchmarking Report Reveals that 33.2% of Untrained End Users Will Fail a Phishing Test
Cybercriminals still know that the easiest way to successfully infiltrate an organization is through its people.
CyberheistNews Vol 13 #25 [Fingerprints All Over] Stolen Credentials Are the No. 1 Root Cause of Data Breaches
CyberheistNews Vol 13 #25 | June 20th, 2023 [Fingerprints All Over] Stolen Credentials Are the No. 1 Root Cause of Data …
New Social Engineering Tactic Uses PDFs in Business Email Compromise Attacks
Legitimate services can be exploited in social engineering, including business email compromise (BEC) attacks. Researchers at Check Point …
Breakdown of an Impersonation Attack: Using IPFS and Personalization to Improve Attack Success
Details from a simple impersonation phishing attack show how well thought out these attacks really are in order to heighten their ability to …
UK Attacker Responsible for a Literal “Man-in-the-Middle” Ransomware Attack is Finally Brought to Justice
The recent conviction of a U.K. man for cyber crimes committed in 2018 brings to light a cyber attack where this attacker manually performed …
New Survey Shows 40% of People Searching for a Job Encountered a Scam
A survey by PasswordManager.com has found that one in three job seekers has fallen for, and responded to, fake job scams over the past two …
[INFOGRAPHIC] KnowBe4’s SecurityCoach: Top 10 Risky Behaviors
Real-time security coaching helps improve your organization’s security culture by enabling real-time coaching of your users in response to …
France Accuses Russia of Spoofing Foreign Ministry Website in ‘Typosquatting’ Campaign
The French government is taking a stand against the increasing threat of digital warfare. Publicly accusing Russia of conducting an extensive …
Takeaways From a Threat Intelligence Specialist on Artificial Intelligence Being a 'Double-Edged Sword'
While artificial intelligence (AI) has been the hot topic of this year, a theme that I continue to see is that AI is being used for good …
Cybercriminals Spoof German Media Anga Com Conference in New Phishing Campaign
A phishing campaign is spoofing the major German media conference Anga Com, according to Jeremy Fuchs at Avanan.
85% of Organizations Have Experienced At Least One Ransomware Attack in the Last Year
Ransomware attacks are as pervasive as ever, with new data demonstrating just how impactful the attacks really are.
State-Based Cyber Attacks Continue to Be a Thorn in the Cyber Insurer's Side
As government-sponsored and widespread vulnerability attacks continue to result in larger damages, cyber insurers are looking for …
Microsoft Describes a Sophisticated Phishing Campaign that Targeted Several Financial Organizations
Microsoft describes a sophisticated phishing campaign that targeted several financial organizations.
CyberheistNews Vol 13 #24 [The Mind's Bias] Pretexting Now Tops Phishing in Social Engineering Attacks
CyberheistNews Vol 13 #24 | June 13th, 2023 [The Mind's Bias] Pretexting Now Tops Phishing in Social Engineering Attacks…
A Master Class on Cybersecurity: Roger Grimes Teaches Password Best Practices
What really makes a “strong” password? And why are you and your end-users continually tortured by them? How do hackers crack your passwords …
Half of U.K. Companies Have Been a Cyber Attack Victim in the Last Three Years
New data puts the spotlight on the human factor in U.K. cyber attacks, where users continue to be susceptible to social engineering, creating …
Forrester: AI, Cloud Computing, and Geopolitics are Emerging Cyberthreats in 2023
Wouldn’t it be great if your cybersecurity strategy only had to focus on just a few threats? Sigh… if only life were that easy. But new …
Organizations Take 43 Hours to Detect an Spear Phishing Cyber Attack
New data makes it crystal clear that spear phishing is a real problem… and organizations may not properly be prepared to detect and address it.
How NK's Cyber Criminals Stole 3 Billion in Crypto To Fund Their Nukes
The Wall Street Journal today revealed that North Korea's hacker army managed to steal a huge amount of cryptocurrency amounting to $3 billion…
Verizon: Stolen Credentials Tops the List of Threat Actions in Breaches
Verizon's DBIR always has a lot of information to unpack, so I’ll continue my review by covering how stolen credentials play a role in attacks.
[SCAM OF THE WEEK] Summer Scams Your Users Should Watch Out For
While your users are getting ready for their next beach vacation, cybercriminals are preparing for their opportunity to strike. Check Point …
Why Companies Have Great Success Training Employees With Simulated Phishing Tests
We occasionally learn of articles and papers that claim that security awareness training and/or simulated phishing campaigns are not …
Verizon: Pretexting Now Tops Phishing in Social Engineering Attacks
The New Verizon DBIR is a treasure trove of data. As we covered here, and here, people are one of the most common factors contributing to …
Verizon: 74% of Data Breaches Involve the “Human Element”
People are one of the most common factors contributing to successful data breaches. Let’s dive in deeper into the latest Verizon Data-Breach …
Smishing Campaign Expands to the Middle East
A Chinese-speaking phishing gang has expanded its targeting from the Asia-Pacific region to the Middle East, researchers at Group-IB have …
Verizon: Email Reigns Supreme as Initial Attack Vector for Ransomware Attacks
My analysis of this year’s newly-released Verizon Data Breach Investigations Report begins with ransomware findings that point back to users …
Why Do You Still Need Security Awareness Training If You Use Phishing-Resistant MFA?
For years, KnowBe4 has been a long-time proponent of everyone using PHISHING-RESISTANT multi-factor authentication (MFA) whenever possible.
North Korean Phishing Campaign Targeting Think Tanks, Academics and Media
The U.S. and South Korean governments have issued a joint advisory outlining a North Korean phishing campaign, The Register reports. The …
CyberheistNews Vol 13 #23 [Wake-Up Call] It's Time to Focus More on Preventing Spear Phishing
CyberheistNews Vol 13 #23 | June 6th, 2023 [Wake-Up Call] It's Time to Focus More on Preventing Spear Phishing Fighting …
[FBI ALERT] Skin Deep: The Scary Reality of New Deepfake-Enabled Sextortion
Today, the FBI alerted warned against a new even more disgusting type of sextortion. Previously, these schemes involved coerced or stolen …
New Phishing Campaign Uses Hyperlinked Images for Fake Gift Cards and Promotions
A phishing campaign is using hyperlinked images in order to trick users into visiting malicious sites, according to Jeremy Fuchs at Avanan. …
Be a Certified Security Awareness and Culture Professional (SACP)™
All, I thought it was necessary to have an independent, vendor-neutral Cert so we would have a real Certified Security Awareness and Culture …
Verification and Deepfake Fraud Trends in North America
Forced verification fraud and deepfake fraud are on the rise in the US and Canada, according to researchers at Sumsub. Pavel Goldman-Kalaydin,…
Warning: Sharing Data with ChatGPT Can Be Misused Outside Your Organization
A new study found that ChatGPT can accurately recall any sensitive information fed to it as part of a query at a later date without controls …
Protecting Patient Data: The Importance of Cybersecurity in Healthcare
As digital transformation continues to shape the healthcare industry, it is crucial for healthcare organizations to prioritize cybersecurity. …
[Wake-Up Call] It's Time to Focus More on Preventing Spear Phishing
Fighting spear phishing attacks is the single best thing you can do to prevent breaches.
CyberheistNews Vol 13 #22 [Eye on Fraud] A Closer Look at the Massive 72% Spike in Financial Phishing Attacks
CyberheistNews Vol 13 #22 | May 31st, 2023 [Eye on Fraud] A Closer Look at the Massive 72% Spike in Financial Phishing …
Spear Phishing Trends in 2023
50% of organizations surveyed were victims of spear phishing attacks in the last twelve months, according to a new report from Barracuda. The …
Russian Ransomware Cybercriminal Behind $200 Million in Damages is Sanctioned by the U.S. Government
The U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) has identified and designated Mikhail Matveev for his role in …
AI Voice-Based Scams Rise as One-Third of Victims Can’t Tell if the Voice is Real or Not
As audio deepfake technology continues to go mainstream as part of the evolution in AI-based tools, new data shows there are plenty of victims…
The Bookmark Trap: How Discord Admins Fell Prey to Social Engineering
Brian Krebs wrote: "A number of Discord communities focused on cryptocurrency have been hacked this past month after their administrators were…
[EPIC AI FAIL] Lawyer cites fake cases invented by ChatGPT
Found this highly amusing article: Legal Twitter is having tremendous fun right now reviewing the latest documents from the case Mata v. …
Tips from Customer Panel on Combining Security Awareness and Compliance Culture Training
At KB4-CON 2023, we had a customer panel that I hosted discussing the connection between security and compliance training content when trying …
“Magic Link” Phishing Attacks Scamming Users With Fake McAfee Renewals
Threat actors are using encoded phishing links to evade security filters, according to Jeremy Fuchs at Avanan. The phishing emails purport to …
[Mastering Minds] China's Cognitive Warfare Ambitions Are Social Engineering At Scale
As the world continues to evolve, so does the nature of warfare. China's People's Liberation Army (PLA) is increasingly focused on "Cognitive …
Your KnowBe4 Fresh Content Updates from May 2023
Check out the 20 new pieces of training content added in May, alongside the always fresh content update highlights, events and new features.
Verizon Sends New Smishing Warning
Verizon has renewed its warnings to customers about the threat of smishing, a social engineering approach that relies upon texts as opposed to…
[SEG Headache] More Than Half of Cybersecurity Leaders Say That Too Many Phishing Attacks Get Through
Egress, a cybersecurity company that provides intelligent email security, recently released their Email Security Risk Report 2023.
Financial Fraud Phishing Attacks Increase 72% In One Year; Financial Industry Takes the Brunt
With attackers knowing financial fraud-based phishing attacks are best suited for the one industry where the money is, this massive spike in …
BatLoader Malware is Now Distributed in Drive-By Attacks
Malign persuasion can take many forms. We tend to hear the most about phishing (malicious emails) or smishing (malicious texts). Other threats…
More Than Half of all Email-Based Cyberattacks Bypass Legacy Security Filters
New data shows that changes in cybercriminals’ phishing techniques are improving their game, making it easier to make their way into a …
[Hands-On Defense] Unpatched Software Causes 33% of Successful Attacks
As you all know, KnowBe4 frequently promotes security awareness training and we also mention that unpatched software is a distant number two …
CyberheistNews Vol 13 #21 [Double Trouble] 78% of Ransomware Victims Face Multiple Extortions in Scary Trend
CyberheistNews Vol 13 #21 | May 23rd, 2023 [Double Trouble] 78% of Ransomware Victims Face Multiple Extortions in Scary …
[Microsoft Warning] A 38% Spike In Business Email Compromise with new Cybercrime-as-a-Service
Microsoft has observed a thirty-eight percent increase in cybercrime-as-a-service (CaaS) offerings for launching business email compromise …
AI-generated Disinformation Dipped The Markets Yesterday
The Insider reported that an apparently AI-generated photo faking an explosion near the Pentagon in D.C. went viral. The Arlington Police …
[New & Improved] QR Code Phishing with Snail Mail Postcards
One of KnowBe4's long-term employees just send me a picture this morning of a postcard that sure looks like it's phishing, the good …
[Free Tool] Find out who falls victim to QR code phishing attacks with our QR Code Phishing Security Test
According to QRTIGER, an online QR code generator company, dynamic QR code scans increased 433% globally from 2021 to 2022. In 2022, the FBI …
New Top-Level Domains as Potential Phishing Risk
Google has recently introduced a set of new top-level domains: .dad, .esq, .prof, .phd, .nexus, .foo, .zip and .mov. They’re now available for…
Cyber Insurance: Is Paying a Ransom Counter-Productive?
Food for thought as discussed on May 18, 2023, an article posted in The Australian Insurance Council: Banning paying a ransom to cyber hackers…
Phishing Tops the List Globally as Both Initial Attack Vector and as part of Cyberattacks
A new report covering 13 global markets highlights phishing prevalence and its role in cyber attacks when compared to other types of attacks.
New “Greatness” Phishing-as-a-Service Tool Aids in Attacks Against Microsoft 365 Customers
This new phishing toolkit is rising in popularity for its effective realism in impersonating not just Microsoft 365, but the victim …
Large-Scale "Catphishing" that Targets Victims Looking for Love
For all the recent focus on artificial intelligence and its potential for deepfake impostures, the boiler room is still very much active in …
KnowBe4 Celebrates Success of 60,000-Customer Milestone
We are thrilled to announce we have reached a milestone of 60,000 customer organizations globally, consisting of tens of millions of end …
The Number of Phishing Attacks Continues to Grow at a Rate of 150% Per Year
The latest Phishing Activity Trends Report from the Anti-Phishing Working Group (APWG) shows an unrelenting upward trend in the number of …
CyberheistNews Vol 13 #20 [Foot in the Door] The Q1 2023's Top-Clicked Phishing Scams | INFOGRAPHIC
CyberheistNews Vol 13 #20 | May 16th, 2023 [Foot in the Door] The Q1 2023's Top-Clicked Phishing Scams | INFOGRAPHIC …
The Face Off: AI Deepfakes and the Threat to the 2024 Election
The Associated Press warned this week that AI experts have raised concerns about the potential impact of deepfake technology on the upcoming …
The State of Organizational Cyber Defenses Impacts Cyber Insurance Availability, Cost, and Terms
A new report highlights the direct connection between how strong your organization’s security stance is and how easy it is to obtain cyber …
FTC Warns of MetaMask and PayPal Phishing Campaigns
The US Federal Trade Commission has issued an alert warning of phishing campaigns that are impersonating PayPal and the MetaMask cryptowallet.
78% of Ransomware Victim Organizations Encounter Additional Threats-Turned-Extortions
New data sheds light on how likely your organization will succumb to a ransomware attack, whether you can recover your data, and what’s …
Ransomware Gangs are “Big Game Hunting” as Victim Org Sizes and Ransom Payments Continue to Rise
Midsize and enterprise organizations take notice: the average and median amount of a ransom payment and the median size of the victim …
Munich Re: "3x growth estimated in cyber crime costs over the next 4 years"
As cyber attacks continue to grow in sophistication and frequency, cyber insurers are expecting their market to double in the next two years.
Spain’s National Police Take Down a Phishing Gang
A phishing (by email) and smishing (by SMS text) operation in Madrid, Seville and Guadalajara has been taken down by the National Police of …
Cyber Insurance Demand Grows as Cybercrime is Expected to Rise to $24 Trillion by 2027
As cyber attacks continue to grow in sophistication, frequency, cyber insurers are expecting their market to double in the next two years.
U.K. Advance Fee Scams Increase by Over 600% in Less Than Two Years
New data from the U.K.’s Office of National Statistics shows that this often overlooked scam has grown significantly in interest – likely …
Number of Ransomware Victim Organizations Nearly Doubles in March
New data shows a resurgence in successful ransomware attacks with organizations in specific industries, countries and revenue bands being the …
King Charles Coronation Results in a Surge in Themed Scam Sites
The once-in-a-lifetime royal occurrence sparked countless websites designed to steal personal information and credit card details, causing …
Business Email Compromise and “Confidential” Mergers and Acquisitions
A newly identified criminal organization has been observed running a large number of business email compromise (BEC) scams. Since February …
KnowBe4 Earns 2023 Top Rated Award from TrustRadius
We are proud to announce that TrustRadius has recognized KnowBe4 with a 2023 Top Rated Award.
[Finger on the Trigger] How the FBI Nuked Russian FSB's Snake Data Theft Malware
The Five Eyes member nations' cybersecurity and intelligence agencies dismantled the infrastructure of the Snake cyber-espionage malware that …
Q1 2023 Top-Clicked Phishing Report [INFOGRAPHIC]
KnowBe4's latest reports on top-clicked phishing email subjects have been released for Q1 2023. We analyze 'in the wild' attacks reported via …
More InterPlanetary File System Services Use Also Means Phishing Abuse by Cybercriminals
The InterPlanetary File System (IPFS), a distributed file-sharing system that represents an alternative to the more familiar location-based …
CyberheistNews Vol 13 #19 [Watch Your Back] New Fake Chrome Update Error Attack Targets Your Users
CyberheistNews Vol 13 #19 | May 9th, 2023 [Watch Your Back] New Fake Chrome Update Error Attack Targets Your Users …
Dallas Police Department is the Latest Victim of a Ransomware Attack
Unfortunately ransomware attacks have taken another victim. The City of Dallas recently confirmed that their police department suffered a …
Comprehensive Anti-Phishing Mitigations: A Quick Overview
The evidence is clear – there is nothing most people and organizations can do to vastly lower cybersecurity risk than to mitigate social …
Blocking Social Engineering by Foreign Bad Actors: The Role of the New Foreign Malign Influence Center
The U.S. government created a new office to block disinformation. The new Foreign Malign Influence Center (FMIC) oversees efforts that span …
[Eye Opener] HTML Phishing Attacks Surge by 100% in 12 Months
The Cyberwire reported: "Barracuda released a study this morning indicating that HTML attacks have doubled since last year.
A Master Class on IT Security: Roger Grimes Teaches You Phishing Mitigation
Phishing attacks have come a long way from the spray-and-pray emails of just a few decades ago. Now they’re more targeted, more cunning and …
[New Feature] Show Your C-Suite the ROI of Security Awareness Training with KnowBe4 Executive Reports
Do you spend too much time creating custom security awareness reports for your C-suite or board of directors? If so, we’re happy to share our …
CNBC: Why Nearly 80% of Leaders are Increasing Cybersecurity Spend
According to a recent EY survey, nearly 80% of business leaders are increasing their cybersecurity investment in the next six to 12 months.
Response-Based Business Email Compromise Contributes to 97% of Attacks
The malwareless and seemingly benign nature of business email compromise emails, mixed with impersonation techniques, are difficult to spot as…
Global Cyber Attacks Continue to Rise as Q1 Sees a 7% Increase
New data highlights just how frequently cyber attacks are attempted and organizations are impacted - and the numbers are far more surprising …
Ransomware Attacks Surge 91% in a Single Month to Reach an All-Time High
March saw a huge jump in ransomware compared to January and February, signifying that organizations should expect to see a lot more of these …
Walmart Jumps to Top of the List of the Worlds Most Impersonated Brands Used in Phishing Attacks
Walmart’s rise to become the brand most likely to be impersonated in Q1 of this year is a real problem.
Malware Downloads Facilitated by Social Engineering
The most common route for malware infections remains social engineering in its various forms: phishing, vishing, etc. Such approaches take …
[May the 4th] How Security Awareness Training Could Have Saved the Death Star
It's May the 4th, a holiday that celebrates our love for a galaxy far, far, away - Star Wars! I can't help but share some cybersecurity …
[FREE RESOURCE KIT] New Password Security Resource Kit to Celebrate World Password Day!
It's World Password Day! This holiday is to ensure everyone always practices good password hygiene. This year, we wanted to share the best …
WSJ: "Merck’s Insurers On the Hook in $1.4 Billion NotPetya Attack, Court Says"
I get the WSJ Cybersecurity newsletter, which by the way is warmly recommended. Kim Nash today reported a shocker which will make everyone's …
[Feet on the Ground] Stepping Carefully When Making an AI Your BFF
Bloomberg's Brad Stone wrote an op-ed covering this topic. In the past month, a chatbot called "My AI" or "Sage" has appeared as a new friend …
Fake Chrome Update Error Messages
Compromised websites (legitimate sites that have been successfully compromised to support social engineering) are serving visitors fake Google…
CyberheistNews Vol 13 #18 [Eye on AI] Does ChatGPT Have Cybersecurity Tells?
CyberheistNews Vol 13 #18 | May 2nd, 2023 [Eye on AI] Does ChatGPT Have Cybersecurity Tells? Poker players and other …
The Two Best Things You Can Do To Protect Yourself and Organization
Since the beginning, two types of computer attacks (known as initial root cause exploits) have composed the vast majority of successful …
Phishing as an Espionage Tactic for Cybercriminals
Phishing is a familiar criminal tactic. It’s also used by intelligence services for cyber espionage campaigns. On Friday, April 28th, 2023, …
Phishing Attack Frequency Rises Nearly 50% as Some Sectors Increase by as Much as 576%
New data provides a multi-faceted look at the changing face of phishing attacks. This data includes who’s being targeted, the tactics being …
Automate Reporting for Security Awareness Training Events and Suspicious Email Remediation Management with Cortex XSOAR and KnowBe4
Security teams face unique challenges in today’s rapidly-changing landscape of phishing, malware, and other social engineering and …
Your KnowBe4 Fresh Content Updates from April 2023
Check out the 19 new pieces of training content added in April, alongside the always fresh content update highlights, events and new features.
Heart of the Matter: How LLMs Can Show Political Bias in Their Outputs
Wired just published an interesting story about political bias that can show up in LLM's due to their training. It is becoming clear that …
[Eyes Wide Shut] Fed Powell's Call with Russian Pranksters Exposed as Social Engineering
It was all over the news. Fed's Jerome Powell was social engineered by Russian pranksters posing as Zelensky.
Does ChatGPT Have Cybersecurity Tells?
Poker players and other human lie detectors look for “tells,” that is, a sign by which someone might unwittingly or involuntarily reveal what …
Latest QBot Attacks Use a Mixture of PDF Attachments and Windows Scripting Host Files to Infect Victims
QBot malware seems to be outliving its competitors through innovative new ways to socially engineer victims into helping install it.
Scammers Impersonate Zelle via the Lure of “Getting Paid” to Get Paid Themselves
A new impersonation scam targets users of the popular pay platform under the guise of the victim having money coming to them and with the goal…
Despite a Majority of Organizations Believing They’re Prepared for Cyber Attacks, Half Were Still Victims
A new survey points to an overconfidence around organization’s preparedness, despite admitting to falling victim to ransomware attacks – in …
Organizations Have No Idea of a Data Breach’s Root Cause in 42% of Reported Cases
New data shows how poorly organizations are at identifying – let alone removing – an attacker's foothold, putting themselves at continued risk…
Recruiting Money Mules
Money mules play a subordinate but important role in the criminal economy. They’re used to move stolen funds around, a low-level version of …
Fake Meta Tech Support Profiles for Fraud
Researchers at Group-IB have found an extensive campaign in which criminal operators have created a large number of fake Facebook profiles …
CyberheistNews Vol 13 #17 [Head Start] Effective Methods How To Teach Social Engineering to an AI
CyberheistNews Vol 13 #17 | April 25th, 2023 [Head Start] Effective Methods How To Teach Social Engineering to an AI …
Another Perspective on ChatGPT's Social Engineering Potential
We’ve had occasion to write about ChatGPT’s potential for malign use in social engineering, both in the generation of phishbait at scale and …
[Heads Up] The New FedNow Service Opens Massive New Attack Surface
You may not have heard of this service planned for July 2023, but it promises a massive new social engineering attack surface. This is from …
FBI Warns of Sextortion Scams that Yield a New Equally Scam-Like Service: Sextortion Assistance
A FBI bulletin highlights a new twist in the sextortion game: companies claiming to assist with addressing sextortion who use deceptive social…
Phishing for Credentials in Social Media-Based Platform Linktree
Social media is designed of course to connect, but legitimate modes of doing so can be abused. One such case of abuse that’s currently running…
More Companies with Cyber Insurance Are Hit by Ransomware Than Those Without
In an interesting twist, new data hints that organizations with cyber insurance may be relying on it too much, instead of shoring up security …
OpenAI Transparency Report Highlights How GPT-4 Can be Used to Aid Both Sides of the Cybersecurity Battle
The nature of an advanced artificial intelligence (AI) engine such as ChatGPT provides its users with an ability to use and misuse, …
Nearly One-Half of IT Pros are Told to Keep Quiet About Security Breaches
At a time when cyber attacks are achieving success in varying degrees and IT pros are keeping quiet about resulting breaches, there is one …
Phishing Email Volume Doubles in Q1 as the use of Malware in Attacks Slightly Declines
New data shows that cybercriminals started this year off with a massive effort using new techniques and increased levels of attack …
Guarding Against AI-Enabled Social Engineering: Lessons from a Data Scientist's Experiment
The Verge came out with an article that got my attention. As artificial intelligence continues to advance at an unprecedented pace, the …
That Email Isn’t from the New Jersey Attorney General
Earlier this month, state employees in the US state of New Jersey began receiving emails that falsely represented themselves as originating …
KnowBe4 Named a Leader in the Spring 2023 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR)
We are excited to announce that KnowBe4 has been named a leader in the Spring 2023 G2 Grid Report for Security Orchestration, Automation, and …
[Arm and a Leg] Cyber Insurers Are Worried About The Long-tail Cost of Attacks
[BUDGET AMMO] James Rundle at the The Wall Street Journal today published a very interesting article about the long-term costs of cyber …
London NatWest Bank Warns Customers of Alarming Impersonation Scams
National Westminster Bank, the London-based bank familiarly known as NatWest, has warned its customers to be on the alert for emails …
KnowBe4 Named a Leader in the Spring 2023 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares Security Awareness Training (SAT) …
CyberheistNews Vol 13 #16 [Finger on the Pulse]: How Phishers Leverage Recent AI Buzz
CyberheistNews Vol 13 #16 | April 18th, 2023 [Finger on the Pulse]: How Phishers Leverage Recent AI Buzz Curiosity leads…
Indian Rail Passenger Ticketing Platform Warns of Online Fraud
The Indian Railway Catering and Tourism Corporation (IRCTC), described as “a popular platform used by a significant number of Indians for …
[Head Start] Effective Methods How To Teach Social Engineering To An AI
Remember The Sims? Well Stanford created a small virtual world with 25 ChatGPT-powered "people". The simulation ran for 2 days and showed that…
Affinity Phishing Attacks Use Social Engineering Tactics to Prey on Victims
Affinity phishing scams are ones in which criminals cultivate trust in their prospective victims by trading on common background, either real …
Large Language Models Will Change How ChatGPT and Other AI Tools Revolutionize Email Scams
The use of Large Language Models (LLMs) is the fine tuning AI engines like ChatGPT need to focus the scam email output to only effective …
‘Support’ Tops the List of Combosquatted Domains Used in Phishing Attacks
A method used in domain impersonation attacks, combosquatting aids the threat actor by using a modified domain name to further increase the …
Recent Artificial Intelligence Hype is Used for Phishbait
Anticipation leads people to suspend their better judgment as a new campaign of credential theft exploits a person’s excitement about the …
Win The AI Wars To Enhance Security And Decrease Cyber Risk
With all the overwrought hype with ChatGPT and AI…much of it earned…you could be forgiven for thinking that only the bad actors are going to …
CyberheistNews Vol 13 #15 [The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency Scams
CyberheistNews Vol 13 #15 | April 11th, 2023 [The New Face of Fraud] FTC Sheds Light on AI-Enhanced Family Emergency …
Top Takeaways You Could be Missing Out on my Upcoming Ransomware Master Class
There is no doubt that ransomware is one of the top cybersecurity challenges of our lifetime. Survey after survey has revealed senior …
[Free Tool] See Which Users Are Susceptible to Risky Security Behavior with SecurityCoach Free Preview!
The human factor is involved in 82% of data breaches, according to the 2022 Verizon Data Breach Investigations Report. Cybercriminals use …
[Jaw-Dropper] FTX's Cybersecurity Was Hilariously Bad
4/11/2023 - Gizmodo just dropped this eye-roll inducing news. The disgraced crypto exchange had no dedicated cybersecurity staff and …
Alarming Tax Phishing Campaign Targets US with Malware
Researchers at Securonix are tracking an ongoing phishing campaign dubbed “TACTICAL#OCTOPUS” that’s been targeting users in the US with …
[INFOGRAPHIC] The Forrester Total Economic Impact™ of KnowBe4 by the Numbers
KnowBe4 commissioned Forrester Consulting to conduct a Total Economic ImpactTM study* examining the potential Return on Investment (ROI) …
Your KnowBe4 Fresh Content Updates from March 2023
Check out the 49 new pieces of training content added in March, alongside the always fresh content update highlights, events and new features.
Recently Exposed North Korean Threat Actor APT43 Targeting Organizations With Spear Phishing
Google’s Threat Analysis Group (TAG) has published a report describing the activities of “ARCHIPELAGO,” a subset of the North Korean …
New Emotet Phishing Campaign Pretends to be the IRS Delivering W-9 Forms
A newly documented phishing campaign demonstrates how timely themes can be impactful in creating a successful attack that gets the recipient …
FBI: Business Email Compromise Attacks Are Being Used to Make Bulk Goods Purchases from Vendors
A new public service announcement focuses on a specific form of BEC attack using little more than a spoofed domain and common vendor payment …
1 in 8 Email Threats Now Make It Past Email Security Solutions
Phishing attacks that can evade detection by email scanners are improving their chances of reaching the inbox, thanks to an increase in the …
"We are hurtling toward a glitchy, spammy, scammy, AI-powered internet."
This MIT Technology Review headline caught my eye, and I think you understand why. They described a new type of exploit called prompt injection.
FBI: 870 Critical Infrastructure Organizations Were the Victim of Ransomware in 2022
The FBI’s newly-released report shows just how ransomware continues to plague critical infrastructure sectors, despite the U.S. government’s …
That’s Not Actually Mr. Musk, That's a Scam
A school principal in Volusia County, Florida has resigned after sending $100,000 to a scammer posing as Elon Musk, WESH 2 News reports. Dr. …
A Master Class on IT Security: Roger Grimes Teaches Ransomware Mitigation
Cybercriminals have become thoughtful about ransomware attacks; taking time to maximize your organization’s potential damage and their payoff.…
How Long Does It Take To Recover From a Ransomware Attack?
When I was in my 30s, I woke up one morning with a terrible pain shooting down one side of my back and around the side. The pain was so …
Scareware From a Phony Ransomware Group
BleepingComputer reports that a cybercriminal gang is sending phony ransomware threats to prior victims of ransomware attacks. The gang, which…
Italy Bans ChatGPT: A Portent of the Future, Balancing the Pros and Cons
In a groundbreaking move, Italy has imposed a ban on the widely popular AI tool ChatGPT. This decision comes in the wake of concerns over …
CyberheistNews Vol 13 #14 [Eyes on the Prize] How Crafty Cons Attempted a 36 Million Vendor Email Heist
CyberheistNews Vol 13 #14 | April 4th, 2023 [Eyes on the Prize] How Crafty Cons Attempted a 36 Million Vendor Email …
Social Engineering Attacks Utilizing Generative AI Increase by 135%
New insights from cybersecurity artificial intelligence (AI) company Darktrace shows a 135% increase in novel social engineering attacks from …
Latitude Forced To Stop Adding New Customers in Aftermath of Breach
Looks like Latitude Finance is trying to give consumers more "latitude" in their exposure to cyber risks. The Australian finance company …
Ukrainian Police Take Down Cybercrime Ring
The Cyber Police of Ukraine have arrested twelve alleged members of an organized cybercrime group that’s stolen approximately $4.3 million …
Mid-Sized Businesses Lack the Staffing, Expertise, and Resources to Defend Against Cyberattacks
Mid-sized businesses – those with 250 to 2000 employees – don’t appear to have what they need to fend off attacks in a number of critical ways.
Majority of Government Employees are Partially Working Virtually Despite Increased User-Related Cyber Risks
New global data shows that those government employees that work solely in the office are the new minority, IT lacks visibility, and user …
Fake ChatGPT Scam Turns into a Fraudulent Money-Making Scheme
Using the lure of ChatGPT’s AI as a means to find new ways to make money, scammers trick victims using a phishing-turned-vishing attack that …
The New Face of Fraud: FTC Sheds Light on AI-Enhanced Family Emergency Scams
The Federal Trade Commission is alerting consumers about a next-level, more sophisticated family emergency scam that uses AI that imitates the…
Artificial Intelligence Makes Phishing Text More Plausible
Cybersecurity experts continue to warn that advanced chatbots like ChatGPT are making it easier for cybercriminals to craft phishing emails …
The Pope, Puff Jackets and Money going POOF!
You have probably seen it. Pope Francis in a designer puff jacket. It fooled millions of people. Culture writer Ryan Broderick called it the …
Australian Police Arrest Business Email Compromise (BEC) Operators
The Australian Federal Police (AFP) have arrested four alleged members of an organized crime group known for carrying out business email …
[LIVE DEMO] Are Your Users Making Risky Security Mistakes? Deliver Real-Time Coaching in Response to Risky User Behavior with SecurityCoach
Do you need an easy, automated way to provide real-time feedback the moment your users make risky mistakes to help reinforce the training …
The FBI's Public Service Warning of Business Email Compromise
The US FBI is warning of business email compromise (BEC) attacks designed to steal physical goods. While BEC attacks are typically associated …
[Eyes Only] New Deepfake Pr0n Site Visits Skyrocket
This is a disgusting topic. It's also a very high social engineering risk. I will keep this post safe-for-work, which is not easy. NBC news …
Confessions of a Former 'The Inside Man' Skeptic
I remember sitting in Stu Sjouwerman’s office with Perry Carpenter and myself being pitched a drama series about cyber security by Jim Shields…
KnowBe4 Debuts Season 5 of Netflix-Style Security Awareness Series - ‘The Inside Man’
We’re thrilled to announce the long-awaited fifth season of the award-winning KnowBe4 Original Series - “The Inside Man” is now available in …
CyberheistNews Vol 13 #13 [Eye Opener] How to Outsmart Sneaky AI-Based Phishing Attacks
CyberheistNews Vol 13 #13 | March 28th, 2023 [Eye Opener] How to Outsmart Sneaky AI-Based Phishing Attacks Users need to…
Oversharing Is a Risk to Information Security
Younger employees need to be wary of oversharing company information on social media, according to John Karabin, senior director of …
Stay Ahead of the Game: Protect Yourself From Trojanized Chat Apps Targeting WhatsApp and Telegram Users
It seems that once again bad actors have found a new way to infect our devices with malware. This time, they are using a devious little trick …
New Vendor Email Compromise Attack Seeks $36 Million
The details in this thwarted VEC attack demonstrate how the use of just a few key details can both establish credibility and indicate the …
Ransomware Data Theft Extortion Goes up 40% to 70% From ‘21 to ’22
A report from Palo Alto Networks’ Unit 42 found that data theft extortion occurred in 70% of ransomware attacks in 2022, compared to 40% in …
The Dangers of Vishing Campaigns and How To Protect Yourself
In recent years, cybercrime has evolved to become more sophisticated than ever before. One of the up and coming methods used by criminals is …
[Live Demo] Customizing Your Compliance Training to Increase Effectiveness
Linking compliance training to specific outcomes is hard. Compliance training has a reputation for being challenging for organizations to …
[Security Masterminds] Unlock Maximum Cybersecurity: 3 Crucial Steps to Enhance Your Capabilities, Coverage, and Culture
Do you ever feel like you are always playing catch up regarding cybersecurity? That it is a never-ending game; no matter what you do, you are …
Users Clicking on Multiple Mobile Phishing Links Increases 637% in Just Two Years
New data shows that phishing mobile devices as an attack vector is growing in popularity – mostly because it’s increasingly working... in …
Cyber Insurers Quietly Remove Coverage for Social Engineering and Fraudulent Instruction Claims
As cyber insurers become more experienced in what kinds of claims are being presented, and the threat action details therein, specific types …
Half of Organizations Report at Least Monthly Outages from Cyberattacks
New data on the current state of cybersecurity shows that organizations are experiencing challenges, falling behind, and seeing the impact of …
Facebook and Microsoft Top the List of Most Impersonated Brands in 2022
As scammers continue to see massive returns on their phishing attacks, the use of impersonation with well-known brands continues to circle …
When a USB Flash Drive is Actually a Bomb
A journalist based in Ecuador recently used a USB flash drive that was actually a legitimate bomb.
Identifying AI-Enabled Phishing
Users need to adapt to an evolving threat landscape in which attackers can use AI tools like ChatGPT to craft extremely convincing phishing …
The Future of Cyber Attacks? Speed, More Speed
I get asked all the time to “predict” the future of cybercrime. What will be the next big cyber attack? What will be the next paradigm …
An Overview of Silicon Valley Bank Themed Social Engineering
Researchers at ReliaQuest warn that organizations should continue to be on the lookout for social engineering attacks related to Silicon …
CyberheistNews Vol 13 #12 [Heads Up] This Week's New SVB Meltdown Social Engineering Attacks
CyberheistNews Vol 13 #12 | March 21st, 2023 [Heads Up] This Week's New SVB Meltdown Social Engineering Attacks On …
Bill 96 in Québec Brings Up Important Point About Training in Native Language Everywhere
A new law in Québec, Canada, that goes into effect this June will require all policies and training materials assigned to employees within …
[Eye Popper] The AI Genie Has Escaped: Stanford copied ChatGPT for a few hundred bucks
Yikes. Loz Blain at NewAtlas just reported that Stanford has copied the ChatGPT AI for less than $600. The article started out with: …
Report Shows Business Email Compromise (BEC) Attacks Increase and Phishing Used as Initial Attack Vector in the Last Year
Secureworks has published a report looking at cybercrime over the course of 2022, finding that business email compromise (BEC) attacks nearly …
Warning Customers About Social Engineering.
It’s a familiar story: scam artists impersonate a trusted brand, a trusted business or a trusted authority in emails and on bogus sites …
A 240% Rise in Dynamic Phishing
Attackers are increasingly using techniques to prevent their phishing pages from being detected by security firms, a new report from …
[Black Eye] The Lesson We Learned. Don't Let this Happen to You. #DMARC
Mea Culpa. When you make a mistake, admit you made a mistake.
Phishing Attacks Top List of Initial Access Vectors with Backdoor Deployment as Top Objective
New data looking back at the cyber attacks observed in 2022 shows that phishing continues to dominate as initial access brokers seem to be …
92% of Organizations Have Fallen Victim to Phishing as Nearly Every Org is Concerned with Email Security
New data shows that not only has just about every organization experienced a successful phishing attack, but that they are also paying the …
Understanding DMARC Better
I talk and present often about DMARC (and SPF and DKIM), including here. A lot of people who think they understand how DMARC works, do not …
[FREE RESOURCE KIT] New Phishing Security Resource Kit Now Available!
Phishing emails increase in volume every month and every year, so we created this free resource kit to help you defend against attacks. …
A Rise in Dynamic Phishing
Attackers are increasingly using techniques to prevent their phishing pages from being detected by security firms, a new report from …
79% of Employee-Reported Phishing Emails Go Completely Undetected by Cybersecurity Solutions
As cybercriminals increasingly turn to malwareless phishing attacks, the ability for security solutions to correctly identify a malicious …
Three-Quarters of Organizations Have Experienced an Increase in Email-Based Threats
New data on the state of email security shows that nearly every organization has been the target of a phishing attack as attacks increase in …
University of Sydney Gives Students and Staff Advice on Avoiding Social Engineering Scams
The University of Sydney has issued advice to help students and staff avoid falling for social engineering attacks.
Season 5 of ‘The Inside Man’ From KnowBe4 Is Less Than a Month Away!
We’re thrilled to announce that Season 5 of the award-winning Knowbe4 Original Series - “The Inside Man” is less than a month away!
Newest FBI Report Shows $10B in Losses Last Year Due to Internet Scams
The 2022 Internet Crime Report by the FBI reported at least $10.3 billion in losses due to internet scams last year.
5 Reasons Why SecurityCoach Is Awesome
I’ve been doing computer security for over 34 years and in that time, I haven’t seen a lot of game-changing products. What I have seen is a …
CyberheistNews Vol 13 #11 [Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
CyberheistNews Vol 13 #11 | March 14th, 2023 [Heads Up] Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising …
Threat Actors are Using FINRA Impersonation For Their Attacks
DomainTools warns that a sophisticated West Africa-based fraud group is impersonating the Financial Industry Regulatory Authority (FINRA) to …
Microsoft Warns of Business Email Compromise Attacks Taking Hours
According to Microsoft's Security Intelligence team, a recent business email compromise attack (BEC) has shown that threat actors are …
[Heads Up] The SVB Bankruptcy Is A Social Engineering Bonanza
Saturday March 11, 2023 -- Over the last 24 hours, the Federal Deposit Insurance Corporation has established the FDIC Bank of Santa Clara …
The interesting history and origin of the word "Bankruptcy"
Regarding the current SVB meltdown, the English word "bankruptcy" has its roots in medieval Italy. It comes from the word "banca rotta," which…
One-Quarter of Users Fall for Online Scams Despite an Overconfidence in an Ability to Spot Them
A new survey of individuals across seven countries shows that users may have had luck on their side, as a majority aren’t sure about their …
Google: Analysis of Cyberattacks Targeting Ukraine Shed Light on What a Cyberwar Strategy Looks Like
A look back at the last year of attacks on Ukraine by Google’s Threat Analysis Group (TAG) provides insight into attacks on NATO countries to …
Use of Malware Decreases in Cyber Attacks as Exploit Usage Skyrockets
New data on cyberattacks from last quarter provides a lens of what kinds of attack techniques to expect to see from cyber attackers this year.
The Education Sector Must Act Now
The education sector remains vulnerable as ransomware shame sites continue to feature teaching institutions from around the world. Some of the…
Phishing for Ring Customers
INKY warns that a phishing campaign is targeting users of the Ring video security system. The scammers are sending brief phishing emails …
Three-Quarters of Vulnerabilities Used in Ransomware Attacks Were Discovered Before 2020
Despite a lot of focus on phishing and remote access as initial access vectors, new data shows the use of vulnerabilities is not only on the …
Half of all Sites Used in Phishing Attacks Impersonate Financial Institutions
As credential theft-focused phishing attacks continue to assist initial access brokers, new data shows banking fraud continues to be a …
Google Phishing Pages Jump 1,560% YoY
Vade has released a report looking at phishing trends in 2022. The researchers say the top three most-impersonated brands last year were …
Employees Are Feeding Sensitive Biz Data to ChatGPT, Raising Security Fears
Robert Lemos at DARKReading just reported on a worrying trend. The title said it all, and the news is that more than 4% of employees have put …
[SCAM OF THE WEEK] Is ChatGPT Your Next Financial Advisor?
ChatGPT, an artificial intelligence (AI) chatbot created by OpenAI, has risen in popularity since its release last year. Now, cybercriminals …
CyberheistNews Vol 13 #10 [Eye Opener] BusinessWeek: The Satellite Hack Everyone Is Finally Talking About
CyberheistNews Vol 13 #10 | March 7th, 2023 [Eye Opener] BusinessWeek: The Satellite Hack Everyone Is Finally Talking …
Three out of Four Organizations Have Experienced a Successful Email-Based Attack as Impacts Increase
New data shows just how impactful these attacks are, with 98% of victim organizations reporting some form of impact from email-based cyber …
Coping With “Double-Extortion” Royal Ransomware
The US Cybersecurity and Infrastructure Security Agency (CISA) and the FBI last week issued a joint advisory on Royal ransomware. Royal is …
Ransomware Attacks on Industrial Infrastructure Climb 87% Despite Security Improvements to ICS Environments
Since the goal of ransomware is to initially disrupt operations, the targeting of industrial control systems has been an increasing focus for …
Executive Impersonation Business Email Compromise Attacks Go Beyond English Worldwide
Despite hearing mostly about BEC attacks in English-speaking countries, analysis of new attack groups highlight the threat of these kinds of …
A Master Class on Cybersecurity: Roger Grimes Teaches Data-Driven Defense
Even the world’s most successful organizations have significant weaknesses in their cybersecurity defenses, which determined hackers can …
Your KnowBe4 Fresh Content Updates from February 2023
Check out the 24 new pieces of training content added in February, alongside the always fresh content update highlights, events and new …
Financial Services Sector at Risk of More Significant Impacts of Email-Based Cyberattacks
Financial services businesses are already in the sights of cybercriminals, and understanding how cyberattacks impact this sector specifically …
CISA's latest ransomware warning promotes fighting social engineering at the top of the document, once again
So, today CISA released another ransomware notice. The Cybersecurity and Infrastructure Security Agency is an agency of the United States …
5 Ways PhishER Saves You Time and Money
Time is the one resource you never get back. Cutting the amount of time between the moment your user reports a suspicious email and when your …
Customer Care Numbers as Phishbait
Researchers at CloudSEK have published a report looking at fraudulent customer service phone numbers in India. The researchers found around …
[Eye Opener] Businessweek: The Satellite Hack Everyone Is Finally Talking About
This morning, Bloomberg News pointed at a brand new article at BusinessWeek, one of their media properties. This is an excellent article that …
Remote Workers Significantly Increase the Cost of Remediating Email-Based Cyberattacks as Costs Average $1 Million
With the average cost of the most expensive successful email attack at over $1 million, it’s necessary to begin to zero in on where the …
NameCheap’s SendGrid Email Account Compromised, Used to Send Phishing Emails
Since phishing attacks need legitimacy to increase their deliverability, this latest twist shows how phishing scammers and hackers are working…
Business Email Compromise Gang Gets Jail Time for Stealing Millions
An international cybercriminal operation responsible for millions of dollars in business email compromise (BEC) scams has finally been …
Blind Eagle Goes Phishing
BlackBerry has published a report on a threat actor, Blind Eagle, also known as APT-C-36, which has been operating against targets in Ecuador …
CyberheistNews Vol 13 #09 [Eye Opener] Should You Click on Unsubscribe?
CyberheistNews Vol 13 #09 | February 28th, 2023 [Eye Opener] Should You Click on Unsubscribe? By Roger A. Grimes. Some …
GLBA and Other Regulations Wake Up to the Importance of Security Awareness Training With June 9, 2023 Deadline
Most computer security practitioners have understood for many years the importance of having an aggressive security awareness training …
Thousands of NPM Packages Used to Spread Phishing Links
Researchers at Checkmarx warn that attackers uploaded more than 15,000 packages to NPM, the open-source repository for JavaScript packages, to…
Malware Report: The Number of Unique Phishing Emails in Q4 Rose by 36%
With nearly 280 million phishing emails detected by just one vendor, and the increase in the number of unique emails, organizations have a lot…
W-2s Are Just the Beginning of Tax-Related Scams This Year
Email scammers can’t pass up a tried and true theme that is almost guaranteed to produce results. And with W-2 forms being sent out, it marks …
Ransomware Attacks Using Extortion Tactics Reaches Critical Mass at 96% of all Attacks
New cyber attack data from 2022 is providing insight into what to expect in 2023, including ransomware campaigns.
28% of Users Open BEC Emails as BEC Attack Volume Skyrockets by 178%
New data shows users aren’t scrutinizing emails used in business email compromise (BEC) attacks, allowing critical changes in banking details …
What Is a Good Survey Rating for Security and Compliance Training?
We received great feedback from many of you after sharing data about completion percentages last month so much that we thought, “What other …
Coinbase Attack Used Social Engineering
Coinbase describes a targeted social engineering attack that led to the theft of some employee data. The attacker first sent smishing messages…
Should You Click on Unsubscribe?
Some common questions we get are “Should I click on an unwanted email’s ’Unsubscribe’ link? Will that lead to more or less unwanted email?”
Do Not Let Ransomware Steal the Show – Business Email Compromise Is the Biggest Threat You Must Prepare For!
When it comes to cybersecurity, ransomware is the rockstar of threats. But taking a peek behind the curtain, business email compromise (BEC) …
A Special Case of Business Email Compromise
Cloudflare warns that business email compromise (BEC) phishing has assumed a new form: vendor email compromise (VEC). The classic BEC case …
CyberheistNews Vol 13 #08 [Heads Up] Reddit Is the Latest Victim of a Spear Phishing Attack Resulting in a Data Breach
CyberheistNews Vol 13 #08 | February 21st, 2023 [Heads Up] Reddit Is the Latest Victim of a Spear Phishing Attack …
Corporate Transitions Represent Times of Heightened Danger
When should organizations be on guard against social engineering? Always, of course, but there are certain times when they should be …
The Curse of Cybersecurity Knowledge
The curse of knowledge is a cognitive bias that occurs when someone is trying to communicate information to another person, but falsely …
Will AI and Deepfakes Weaken Biometric MFA
You should use phishing-resistant multi-factor authentication (MFA) when you can to protect valuable data and systems. But most biometrics and…
[HEADS UP] Russian Hacker Group Launches New Spear Phishing Campaign with Targets in US and Europe
The Russian-based hacking group Seaborgium is at it again with increased spear phishing attacks targeting US and European countries in the …
[LIVE DEMO] Are Your Users Making Risky Security Mistakes? Deliver Real-Time Coaching in Response to Risky User Behavior with SecurityCoach
Do you need an easy, automated way to provide real-time feedback the moment your users make risky mistakes to help reinforce the training …
Security Awareness: The Top Trend of 2023
The Dutch organization Supply Value (a specialist in network optimalisation) together with the website Computable, published an article on …
[INFOGRAPHIC] 9 Cognitive Biases Hackers Exploit the Most
Cybersecurity is not just a technological challenge, but increasingly a social and behavioral one.
New Survey Reveals Employees are the Attack Surface
A survey by Tanium has found that IT security professionals in the UK say that 64% of avoidable cyber attacks are due to human error, which …
Reddit is the Latest Victim of a Spear Phishing Attack Resulting in a Data Breach
There is a lot to learn from Reddit's recent data breach, which was the result of an employee falling for a “sophisticated and …
FTC: Romance Scams Cost U.S. Victims a Total of $1.3 Billion
Seemingly repeating the previous year, the FTC’s latest report highlights that nearly 70,000 people reported being the victim of a romance …
Deepfake Crackdown After 4Chan Users Make Celebrity Voices Say Racist, Transphobic, and Violent Things
As deepfake technology continues to improve, creators of deepfake technology seek to lock down and safeguard the use of their technology after…
CyberheistNews Vol 13 #07 [Scam of the Week] The Turkey-Syria Earthquake
CyberheistNews Vol 13 #07 | February 14th, 2023 [Scam of the Week] The Turkey-Syria Earthquake Just when you think they …
Cybercriminals are Using Geotargeted Phishing to Target Victims
Attackers are abusing a legitimate service called “GeoTargetly” to launch localized phishing attacks, according to Jeremy Fuchs at Avanan. …
Spear Phishing Attacks Increase 127% as Use of Impersonation Skyrockets
Impersonation of users, domains, and brands is on the rise, as is the use of malicious links, in response to security vendors improving their …
U.K. Citizens See 82% Increase in Advanced Fee Scams in the Last Year
In the wake of the rising cost of living, new scams targeting those in less-than-optimal financial situations based on “deprived” areas …
Hackers Work Around ChatGPT Malicious Content Restrictions to Create Phishing Email Content
Active discussions in hacker forums on the dark web showcase how using a mixture of the Open AI API and automated bot from the Telegram …
Be Wary of Survey Scams
Online surveys are too often scams designed to steal personal or financial information, warns Phil Muncaster at ESET. Muncaster explains that …
[HEADS UP] If You're a Fan of 'The Last of Us' You May be Targeted for These Campaigns
The success of the TV adaption of this PlayStation game 'The Last of Us' has been a huge hit for fans. Unfortunately, this new series has …
Do Not Fall Victim to Cyber Attacks – Find Out What the Latest Hiscox Report Reveals!
Insurance provider Hiscox has published its fifth annual cyber readiness report, which has some eye-opening statistics.
[Scam Of The Week] The Turkey-Syria Earthquake
Just when you think they cannot sink any lower, criminal internet scum is now exploiting the recent earthquake in Turkey and Syria.
Thinking Critically About Your Online Behavior
Employees need to adjust their mindsets in order to defend themselves against social engineering attacks, according to Jonathon Watson at …
How Artificial Intelligence Can Make or Break Cybersecurity
With the introduction of OpenAI's Chat GPT, artificial intelligence is no longer considered part of science fiction. It has presented a new …
[New Feature] Immediately Add User-Reported Email Threats to Your Microsoft 365 Blocklist from Your PhishER Console
Now there’s a super easy way to keep malicious emails away from your users through the power of the KnowBe4 PhishER platform!
A Close Call – PayPal Scam Warning
On Sunday, I received an urgent message from a friend. PayPal had sent him an email saying that a co-worker had sent him money. This was not …
Students Phished with Bogus Job Offers
A phishing campaign is targeting college students with phony part-time job opportunities, according to Jeremy Fuchs at Avanan. The emails …
Your KnowBe4 Fresh Content Updates from January 2023
Check out the 39 new pieces of training content added in January, alongside the always fresh content update highlights, events and new features.
Yahoo Suddenly Rises in Popularity in Q4 to Become the Most Impersonated Brand in Phishing Attacks
Completely absent from the top 10 brands for more than two years, Yahoo’s impersonation may indicate that scammers are looking for new attack …
Initial Access Brokers Leverage Legitimate Google Ads to Gain Malicious Access
A threat actor tracked as DEV-0569 appears to be using a combination of Google Ads and impersonated websites to compromise credentials and …
BEC Group Launches Hundreds of Campaigns
A business email compromise (BEC) gang has launched more than 350 attacks against organizations in the US, according to researchers at …
KnowBe4 Wins Winter 2023 "Best of" Awards From TrustRadius in Multiple Categories
KnowBe4 is proud to be recognized by TrustRadius in the “Best Of” Awards for overall, best feature set, best relationship, and best value for …
Artificial Intelligence, ChatGPT and Cybersecurity: A Match Made in Heaven or a Hack Waiting to Happen?
Artificial intelligence (AI) is no longer science fiction.
Scammers Impersonate Financial Advisors Through Social Media Platforms
A large scam campaign is targeting users on LinkedIn and other social media platforms posing as financial advisors, according to researchers …
Travel-Themed Phishing Attacks Lure Victims with Promises of Free Tickets, Points, and Exclusive Deals
New analysis of December and January emails shows massive spikes in attacks aimed at stealing personal information and credit cards under the …
OneNote Attachments Used as Phish Hooks
Threat actors are using malicious attachments in OneNote in order to distribute malware, BleepingComputer reports. The attackers attach VBS …
Ransomware Targets are Getting Larger and Paying More as Fewer Victims Are Paying the Ransom
New data showcasing the state of ransomware shows that while organizations are likely getting better at recovery (and not paying the ransom), …
Microsoft OneNote Attachments Become the Latest Method to Spread Malware
With Microsoft disabling macros by default on Office documents, cybercriminals are left needing another means to launch malware that’s …
Alert: Refund Scam Targeting Federal Agencies via RMM Software
At least two federal civilian agencies were the unfortunate victims of a refund scam campaign, perpetrated through the use of remote …
Russian and Iranian Spear Phishing Campaigns are Running Rampant in the UK
The UK’s National Cyber Security Centre (NCSC) has described two separate spear phishing campaigns launched by Russia’s SEABORGIUM threat …
Hacker's Movie Guide: The Complete List of Hacker and Cybersecurity Movies
Is alert fatigue getting to you? I found a guide that allows you some well-deserved personal downtime, and still has something to do with work…
Stu's Law: "You get the future you ignore"
I have read a lot of Sci-fi. Thousands of books actually. You can't help but start recognizing patterns. One of my favorite movies is Blade …
What is a Good Completion Percentage for Security and Compliance Training?
Completion percentages on compliance and security training campaigns have become a popular topic of discussion.
How Does Quantum Impact Passwords?
Yeah, quantum computers are likely to be able to crack passwords from every angle.
Do Not Get Fooled Twice: Mailchimp's Latest Breach Raises Alarm Bells – Protect Yourself Now!
For the second time in less than a year, Mailchimp has found itself in a precarious situation, having to admit that it has been breached. It …
[Security Masterminds] Breaking It Down to Bits & Bytes: Analyzing Malware To Understand the Cybercriminal
In our latest episode of Security Masterminds, we have the pleasure of interviewing Roger Grimes, Data-Driven Defense Evangelist for KnowBe4, …
Phishing Campaign Impersonates Japanese Rail Company
Researchers at Safeguard Cyber describe a phishing campaign that’s posing as a Japanese rail ticket reservation company.
2022 Report Confirms Business-Related Phishing Emails Trend [INFOGRAPHIC]
KnowBe4's latest reports on top-clicked phishing email subjects have been released for 2022 and Q4 2022. We analyze 'in the wild' attacks …
New QR Code Phishing Campaign is Impersonating the Chinese Ministry of Finance
Researchers at Fortinet warn that a phishing campaign is impersonating the Chinese Ministry of Finance. The phishing emails contain a document…
Cybercrime The World’s Third Largest Economy After the U.S. and China
Cybersecurity Ventures released a new report that showed cybercrime is going to cost the world $8 trillion USD in 2023.
Ransomware Has SMBs Reprioritizing Their Cybersecurity Spending to Combat Attacks
New data shows that SMBs can clearly see where they have cybersecurity issues and are taking great strides to put their devoted budget to …
The Current State of Cybersecurity Should Fear AI Tools Like ChatGPT
Malicious use of the text-based AI has already begun to be seen in the wild, and speculative ways attackers can use ChatGPT may spell …
Blank-Image Attacks Impersonate DocuSign
An unusual phishing technique has surfaced this week. Avanan, a Check Point Software company, released a blog Thursday morning detailing a new…
[Eye Popper] Ransomware Victims Refused To Pay Last Year
Finally some good news from the ransomware front! Despite bad actors launching a number of ransomware campaigns throughout 2022, …
How South Africa's Largest Law Firm Was Fined R5.5m for Not Educating Customers
Africa’s largest law firmordered to pay R5.5 million to a woman who fell victim to a hacking syndicate. When Judith Hawarden was buying a …
Phishing For Industrial Control Systems
Mandiant has published a report describing phishing emails that have breached organizations in the industrial sector. Mandiant explains that …
The Amazing Thing Is that DHL Phishing Campaigns STILL Work
Researchers at Armorblox warn that a phishing campaign is impersonating DHL with fake shipping invoices.
Spear Phishing Campaign Targets Southeast Asia
Researchers at Group-IB are tracking a previously unknown threat actor dubbed “Dark Pink” that’s using spear phishing attacks to target …
Cybercriminals Mimic Victim Website to Publish Exfiltrated Data on the Public Web
In a new twist, threat actors use a typo squatted domain name to increase the chances that stolen data will be seen by the general public …
Government, Higher Ed, School Districts, and Healthcare Continue to be Victims of Ransomware Attacks
An analysis of the publicly-accessible data on ransomware attacks shows that these sectors that were a primary target of ransomware in 2021 …
Cyberinsurer Beazley Introduces a $45M Cyber Catastrophe Bond to Offset Risk
In a move designed to protect the insurer and allow for more cyber policies to be issued, this bond is new to cyberinsurance, but not to …
KB4-CON 2023 Agenda is Now Available!
Exciting news! We just released our full conference agenda for KB4-CON 2023, happening April 24-26 in Orlando, Florida. We’ve brought back …
Is Your Organization’s Password Complexity Requirement Strong Enough? Probably Not
Is your organization’s password complexity strong enough?
[INFOGRAPHIC] PhishER by the Numbers
PhishER, KnowBe4’s industry-leading Security Orchestration, Automation and Response (SOAR) platform, takes an otherwise complicated and …
[New Feature] Continuously Monitor for Any Detected Password Vulnerabilities Within Your User Base with PasswordIQ
We’re thrilled to announce that the power of KnowBe4’s most popular free password security tool has been brought to your KnowBe4 console as a …
Check Point Software: "2022 Saw A Huge Rise In Cyberattacks"
Techradar reported that cyberattacks saw a significant rise in 2022, mostly due to the increase in organizations going virtual to combat the …
[Ache In the Head] The Problems With Your Not-So-Secure Email Gateway
I have been doing some research on Secure Email Gateways. The picture is not that pretty. Below I will summarize what I found.
[Heads Up] Phishing Attacks Are Now The Top Vector For Ransomware Delivery
Phishing attacks are now the top vector for ransomware delivery, according to researchers at Digital Defense. Phishing emails can be highly …
Government Workers as Phishing Targets
Government workers are prime targets for social engineering attacks, according to Kaitlyn Levinson at GCN. Attackers use different tactics to …
21% of federal agency passwords cracked in their security audit
Some excellent work here. An internal US Government agency audit audit showed that a fifth of passwords were easy to crack. Their recently …
Italian Cybercriminal Pleads Guilty to Phishing for Book Manuscripts
An Italian citizen named Filippo Bernardini has pleaded guilty in New York to stealing more than a thousand unpublished book manuscripts from …
Password Managers Can Be Hacked Lots of Ways and Yes, You Should Still Use Them
The recent hack (at least 7th) of the LastPass password manager has lots of people wondering if they should use a password manager.
The Good, the Bad and the Truth About Password Managers
We strongly recommend that you use a password manager to reduce password reuse and improve complexity, but you may be wondering if it’s really…
Phishing in the Service of Espionage
Reuters describes a cyberespionage campaign carried out by the hitherto little-known threat group researchers track as "Cold River." The group…
A Look Back at Mobile Government Cyberattacks Shows Increased Attacks and Weaker Security
A rise in the reliance on unmanaged mobile devices, matched with a lack of patching and increased attacks seeking solely to steal credentials …
Ransomware and Fraudulent Funds Transfer are the Two Main Drivers of Cyber Loss
Representing more than half of all cyber loss, new data shows these attacks all begin with employees falling for social engineering, phishing,…
New Crypto Scam Targets Flipper Zero Buyers Impersonating Legitimate Shops
Interest in the handheld open-source multi-function cybersecurity tool by techies has risen to a new campaign seeking to steal crypto funds …
Phishing Campaigns Impersonate the UK Government
The UK’s National Cyber Security Centre (NCSC) has outlined the top six most impersonated UK government agencies in 2022. The most …
These grim figures show that the ransomware problem isn't going away
ZDNet summarized the problem as follows: "Up to 1,981 schools, 290 hospitals, 105 local governments and 44 universities and colleges were hit …
Using AI Large Language Models to Craft Phishing Campaigns
Researchers at Check Point have shown that Large Language Models (LLMs) like OpenAI’s ChatGPT can be used to generate entire infection chains,…
There is a New Trend in Social Engineering with a Disgusting Name; "Pig-butchering"
The technique began in the Chinese underworld, and it amounts to an unusually protracted form of social engineering. The analogy is with …
Finance and Insurance Is the Sector Most Impacted by Data Breaches In 2022
Analysis of the year’s breaches shows Finance and Insurance businesses are the most targeted and have lost a material count of records as a …
One Out of 10 Threats Still Make It All the Way to the Endpoint
Despite good intentions, layered security measures, and efficacy claims by security solution vendors, new data shows that email-based threats …
Your KnowBe4 Fresh Content Updates from December 2022
Check out the 36 new pieces of training content added in December, alongside the always fresh content update highlights and new features.
Phishing Activity Rose 130% in the Second Half of 2022, Representing Three-Quarters of All Email-Based Attacks
New data focused on cyberattacks in the second half of the year-to-date shows phishing taking the overwhelming lead as the initial attack …
[Heads Up] LastPass Attack Could Supercharge Spear Phishing Attacks
By Roger A. Grimes. KnowBe4 recommends that everyone use a password manager to create and use strong passwords as a part of their password …
[Eye Opener] Insurance policy doesn’t cover ransomware attack, Ohio Supreme Court says
Dec. 27, 2022, The Ohio Supreme Court ruled in favor of an insurance company, determining that its contract to cover any direct physical loss …
Attackers Pose as Facebook Support Using Legitimate Facebook Posts to Bypass Security Solutions
Impersonating Facebook using its own platform against them, a new phishing attack takes advantage of victim’s inability to distinguish …
QBot Malware Attacks Use SVG files to Perform HTML Smuggling
QBot malware phishing campaigns have adopted a new distribution method using SVG files to perform HTML smuggling that locally creates a …
Microsoft Warns of Signed Drivers Being Used to Terminate AV and EDR Processes
The malicious abuse of several developer program accounts in Microsoft’s Windows Hardware Developer Program allowed threat actors to have …
The Number of Phishing Attacks Grows 15% in One Quarter, Reaching an All-Time High
New data shows that while ransomware remains somewhat flat, massive increases in business email compromise and response-based email attacks …
New Polymorphic Wiper Malware Leaves Attacked Environments “Unrecoverable”
As an apparent method of political commentary on the war in Ukraine, the new Azov wiper uses a mix of intermittent overwriting and trojanizing…
Spear Phishing Campaign Targets Japanese Political Organizations
Researchers at ESET warn that a Chinese-speaking threat actor dubbed “MirrorFace” targeted Japanese political organizations with spear …
"How I lost my dog and almost my Google credentials..."
A well-trained Knowster posted: "I lost my dog this weekend and my mother in law was trying to be helpful and put my real phone number on a …
KnowBe4 Named a Leader in the Winter 2023 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR)
We are excited to announce that KnowBe4 has been named a leader in the Winter 2023 G2 Grid Report for Security Orchestration, Automation, and …
KnowBe4 Named a Leader in the Winter 2023 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares Security Awareness Training (SAT) …
Ivanti Report Shows Cybersecurity Practitioners Concentrating on Right Threats
A recent Ivanti report shows cybersecurity practitioners getting more focused on the threat landscape, but defenders may need to hone their …
’Tis the season for Scam-Folly Fa La La La La
The festive season is my favorite time of the year. It is a time to celebrate and reconnect with our family, friends and community and the one…
XLL Files Used to Deliver Malware
Attackers are using XLL files to embed malicious code in Office documents, according to researchers at Cisco Talos. Microsoft is phasing out …
Now BEC Attacks Steal Physical Goods
The Federal Bureau of Investigation (FBI), the Food and Drug Administration Office of Criminal Investigations (FDA OCI), and the US Department…
Social Engineering, Money Mules, and Job Seekers
A small town in Manitoba, WestLake-Gladstone (population about 3300), fell victim to a social engineering campaign. The municipal government …
Hospitals Warned of Royal Ransomware Attacks by U.S. Department of Health
This brand new ransomware gang is on the attack and, despite them being new to the game, are coming out of the gate attacking the healthcare …
Less Than One-Third of Organizations Leverage Multiple Authentication Factors to Secure Their Environment
Demonstrating a complete lack of focus on the need for additional authentication factors, surprising new data highlights a material security …
Ten Charged with BEC Healthcare Scheme That Took More than $11 Million
Tricking five state Medicaid programs, two Medicare Administrative Contractors, and two private health insurers, the scammers posed as …
Cybersecurity Experts Weigh in on Modern Email Attacks
Abnormal Security’s CISO, Mike Britton consolidates some of the best advice from a three-part webinar series on the current state of risk …
Interest in Infostealer Malware Within Cyberattacks Spikes as MFA Fatigue Attacks Increase
New analysis of dark web forums shows an increase in discussions around the use of infostealer malware as part of both the first attack within…
October and November Have Been the Two Busiest Months for Ransomware
Trending data going back to January of 2020 shows that ransomware attacks are continually increasing in number with unusual highs in the 4th …
Utility Bill is the New Phishbait for Cybercriminals
An SMS phishing (smishing) campaign is impersonating utility providers in the US, Cybernews reports. Researchers at Enea AdaptiveMobile …
Look Out For Scammers This Holiday Season on Social Media
You know how some gifts are insanely sought after each year, selling out in mere minutes? Well, these are great tools for scammers, especially…
Ughh. FBI’s Vetted Threat Sharing Network ‘InfraGard’ Hacked
Investigative reported Brian Krebs reported December 13, 2022 that "InfraGard, a program run by the U.S. Federal Bureau of Investigation (FBI)…
CISA Phishing Infographic Contains a Lot of Good Information
On December 8th, the Cybersecurity & Infrastructure Security Agency (CISA) released a great phishing infographic about data collected, …
[CASE STUDY] New-school Approach to Training and Simulated Phishing Shines Over Traditional LMS
A U.S.-based enterprise manufacturing organization cut their Phish-prone Percentage™ (PPP) by more than 80% after five months using the …
[EYE OPENER] How ChatGPT Can Be Used For Social Engineering
ChatGPT could give Google a serious run for its money. We are not quite there yet, but the capabilities are rapidly improving. Just have a …
Incident Response Actions are Systematically Reverse by Hackers to Maintain Persistence
Analysis of attacks on two cellular carriers have resulted in the identification of threat actions designed to undo mitigations taken by …
New Modular Attack Chain Found That Allows Attackers to Change Payloads Mid-Breach
We’ve long known developers of cyberattacks to be crafty and focus a lot of energy on obfuscation, but a new attack can shift gears midstream,…
Scammer Group Uses Business Email Compromise to Impersonate European Investment Portals
A sophisticated scammer group has stolen at least €480 million from victims in France, Belgium, and Luxembourg since 2018, according to …
[Eye Opener] Cybersecurity Resilience Emerges as Top Priority as 62% of Companies Say Security Incidents Impacted Business Operations
Cisco's annual Security Outcomes Report shows executive support for a security culture is growing. The report identifies the top seven success…
Cyber Insurers Focus on Catastrophic Attacks and Required Minimum Defenses as Premiums Double
Recent attacks are helping cyber insurers better understand what security strategies need to be in place and how to price policies based on …
Archives Overtake Office Documents as the Most Popular File Type to Deliver Malware
Taking the lead over the use of Word, Excel, PDF, and other office-type documents in attacks, new data shows that files like ZIP and RAR have …
Ransomware, Ransom-war and Ran-some-where: What We Can Learn When the Hackers Get Hacked
Ransomware strikes organizations almost every two seconds. Tales of bad actors doing their worst fill the InfoSec news cycle, but what happens…
Russian Threat Actor Impersonates Aerospace and Defense Companies
A Russia-linked threat actor tracked as TAG-53 is running phishing campaigns impersonating various defense, aerospace, and logistic companies,…
Holiday Shopping Scams Online Are Too Good to be True
It's three weeks before Christmas, and the latest video game console is getting harder and harder to find in stores. You've checked all the …
CyberheistNews Vol 12 #49 [Keep An Eye Out] Beware of New Holiday Gift Card Scams
CyberheistNews Vol 12 #49 | December 6th, 2022 [Keep An Eye Out] Beware of New Holiday Gift Card Scams By Roger A. Grimes Every …
Credential Phishing with Apple Gift Card Lures
A phishing campaign is impersonating Apple and informing the user that their Apple account has been suspended due to an invalid payment …
Inside NATO’s Efforts To Plan For A Future Cyberwar
Maggie Miller at Politico had the scoop: "TALLINN, Estonia — Some 150 NATO cybersecurity experts assembled in an unimposing beige building in …
New Threat Group Already Evolves Delivery Tactics to Include Google Ads
Delivering an equally new Royal ransomware, this threat group monitored by Microsoft Security Threat Intelligence has already shown signs of …
Latest Netflix-Impersonated Phishing Attacks Surge in Frequency by 78% Since October
Using a mix of invisible and lookalike characters, this phishing attack attempts to get past security scanners by obfuscating both email …
It’s Official: COVID-related Phishing is Dead as Scammers Return to Impersonating Famous Brands
New analysis of spam and malicious emails show the all but nonexistence of COVID-esque impersonation of government and pharm entities in lieu …
Ransomware Attacks on Holidays and Weekends Increase and Take a Greater Toll on Organizations
With 97% of U.S. organizations experiencing a ransomware attack over a weekend or on a holiday, the impacts on response and recovery time are …
Your KnowBe4 Fresh Content Updates from November 2022
Check out the 55 new pieces of training content added in November, alongside the always fresh content update highlights and new features.
Spoofing-as-a-Service Site Taken Down
Law enforcement authorities across Europe, Australia, the United States, Ukraine, and Canada have taken down a popular website used by …
Beware of Holiday Gift Card Scams
Every holiday season brings on an increase in gift card scams. Most people love to buy and use gift cards. They are convenient, easy to buy, …
Quiet Quitting Can Potentially Lead to Insider Security Risks
The phenomenon known as “quiet quitting,” in which employees become disengaged from their work while formally remaining in their jobs, can …
Merriam-Webster has announced "gaslighting" as the 2022 word of the year
Merriam-Webster has announced "gaslighting" as the 2022 word of the year. One definition of gaslighting is "to manipulate (someone) into …
Users Can Engage with Training Anytime with KnowBe4's Mobile Learner App
We’re excited to introduce a new way for your users to engage with KnowBe4 security awareness and compliance training anytime and anywhere …
There’s No Such Thing as a Free Yeti, Only Social Engineering Tactics
It’s easy to think of the typical online holiday scam as something that affects mostly individuals. Sad, maybe, and unfortunate, but not …
WhatsApp data breach sees nearly 500 million user records up for sale
Craig Hale at Techradar reported: "A post on a “well-known hacking community forum” claims almost half a billion WhatsApp records have been …
[Send This To Your Users] 5 Top Scams To Watch Out For This Holiday Season
Here is a 3-minute article that we suggest you copy/paste and send to all your users as part of your ongoing security culture campaign. "The …
Cybersecurity incidents cost organizations $1,197 per employee, per year
This statistic is alarming and underscores the importance of having a robust cybersecurity program in place. According to the Ponemon …
A Recent, Complex, Ransomware Campaign
Microsoft has observed a threat actor that’s been running a phishing campaign since August 2022. The threat actor, which Microsoft tracks as …
New Instagram Support Phishing Attack Fakes “Unusual Logon” Experience Well Enough to Fool Victims
Long gone are the days of tacky landing pages that barely impersonate a brand; threat actors are improving their social engineering game well …
Image-Based Phishing and Phone Scams Continue to Get Past Security Scanners
Using the simplest tactic of not including a single piece of content that can be considered malicious, these types of scams are making their …
World Cup Phishing Attacks Doubled And Will Increase
Researchers at Trellix revealed that phishing email attacks targeting users in the Middle East doubled in October 2022 ahead of the World Cup …
MFA Fatigue Attacks
Researchers at Specops Software describe a technique attackers are using to bypass multi-factor authentication (MFA). In an article for …
4 out of 10 Emails are Unwanted as nearly 40% of all Attacks Start with Phishing
New data focused on emails sent through Microsoft 365 highlights the methods used to ensure a successful attack beginning with a malicious …
10 Million Health Records from Australian Insurer Medibank are Leaked After Refusing to Pay the Ransom
The aftermath of a ransomware attack last month demonstrates just how bad an attack can get when the cybercriminals don’t get what they want.
2022 Black Friday and Cyber Monday Scams
In years gone by, Black Friday was a 24-hour rush to the shops (you remember those places with actual people and merchandise that you could …
This New Phishing Kit Flies Under the Radar of Antivirus Software
Akamai researchers have discovered a new phishing campaign that targets United States consumers with fake holiday offers, TechRadar reports. …
Over One-Third of Companies Who Pay the Ransom are Targeted for a Second Time
Despite the somewhat logical notion that once you’ve paid the ransom, the attack is over, new data shows that paying the ransom doesn’t help …
Retailers: Credential Harvesting Attacks Are the “Big Thing” This Year for the Holiday Season
New data polled from analysts and members of the retail industry about their security focus is this holiday season reveals the kinds of …
Discover 5 Major Threats to Your Digital Supply Chain and How to Reduce Your Vendor Risk
You’ve heard that vendor dependencies are ripe for malicious abuse and you have read the stories where vendors were used to exploit and …
Phishing Attacks Misuse Microsoft Dynamics 365 Customer Voice Functionality to Hide Malicious Links
Leveraging a legitimate feature of Dynamics 365, threat actors are able to obfuscate the malicious nature of the email within content that …
Valid Accounts Rank as the Top Initial Access Infection Vector, Putting a Spotlight on Credentials
As ransomware, business email compromise, and phishing attacks continue to escalate, new data sheds light on where organizations need to focus…
Ransomware Attacks on UK Organizations are Not Being Reported Enough, Clouding Impact
A new report from the UK’s National Cyber Security Center highlights the current state of threats in the UK, with particular focus on …
Cyber Insurance Rates Begin to Stabilize as Insurers Gain Better Insight into Cyberattacks
The latest data shows that historically massive rate increases seen over the last few years are beginning to come down, primarily due to …
Holiday Package or Scam Message? Clickers Beware
As we enter the holiday season, we start getting bombarded with amazing offers and often take advantage of not only grabbing ourselves a …
Watch Out For This Tricky New Tactic Called Clone Phishing
Researchers at Vade Secure describe a type of phishing attack dubbed “clone phishing,” in which attackers follow up a legitimate email from a …
FBI director says he's 'extremely concerned' about China's ability to weaponize TikTok
Suzanne Smalley at Cyberscoop reported: "FBI Director Christopher Wray told Congress on Tuesday he is “extremely concerned” that Beijing could…
[SCAM OF THE WEEK] Phishing Campaign Targets Crypto Users
Major cryptocurrency company FTX recently filed for bankruptcy, and there's a big phishing campaign on the loose targeting FTX users.
Fangxiao Domain-Spoofing for Revenue
Researchers at Cyjax describe a large phishing campaign being run by a China-based financially motivated threat actor called “Fangxiao.” The …
[FREE Resource Kit] Stay Safe This Holiday Season with KnowBe4
It's the best time of the year! But also, it's the busiest time for cybercriminals. Since your users will be distracted with seasonal …
“Hired Hand” in the Kingdom of Saudi Arabia Uses Domain Spoofing
Sometimes a social engineering campaign has a clear geographical focus, often shaped by language, holidays, or current events. In this case, …
The Rise in Unwanted Emails, Now Found to be Nearly 41%
How many business emails do the recipients actually want? Or, conversely, how many of them are unwanted? A study by Hornetsecurity looked at …
[HEADS UP] FBI Warns of Tech Support Scams That Impersonate Payment Portals for Fake Refunds
In the latest FBI warning, cybercriminals are now impersonating financial institutions' refund payment portals. This effort is to contain …
Phishing Campaign Abuses Microsoft Customer Voice
Researchers at Avanan warn that a phishing campaign is using Microsoft’s Dynamic 365 Customer Voice feature to send malicious links. Customer …
Three-Quarters of Employees Feel It’s the Company’s Job to Ensure Security, Despite Three-Quarters Also Personally Experiencing a Cyberattack
Even with employees seeing cyberattacks first-hand and understanding the seriousness of such attacks, organizations have a culture problem …
Ransomware Attacks Targeting Manufacturing are up 52% Over the Course of 12 Months
While every sector is taking strides to improve their security stances against ransomware and other cyberattacks, the latest data shows that …
Cyberattacks Globally Increased by 28% in the Third Quarter of 2022 as the Average Org Experiences Over 1,100 Attacks Weekly
Check Point Research provides highlights that color the third quarter of 2022, painting a picture of increases in attack frequency and …
Here Is What You Can Do To Inspect SMS URL Links Before Clicking
Phishing via Short Message Service (SMS) texts, what is known as smishing, is becoming increasingly common (some examples are shown below). …
Cookie-stealing Feature Added by Phishing-as-a-Service Provider To Bypass MFA
The Robin Banks phishing-as-a-service platform now has a feature to bypass multi-factor authentication by stealing login session cookies, …
[EYES OUT] This Scary Strain of Sleeper Ransomware Is Really a Data Wiper in Disguise
This Data wiper replaces every other 666 bytes of data with junk. Techradar reported that a new data-wiping malware has been detected, …
PhishER Turns Golden Hour Into Golden Minute
Hospital emergency rooms around the world are fine-tuned to meet the requirements of the “Golden Hour”. The Golden Hour is a well-accepted …
New Business Email Compromise Gang Impersonates Lawyers
A criminal gang is launching business email compromise (BEC) attacks by posing as “real attorneys, law firms, and debt recovery services.” The…
[HEADS UP] Australia Continues to be Vulnerable to Cybercrimes as Half a Billion Has Been Lost to Scammers
Australia is the new hot spot for cyber attacks. The Australian Cyber Security Centre (ACSC) recently reported that Australia has been …
[New Product] Users Making Security Mistakes? Coach Them in Real-Time with SecurityCoach.
We are thrilled to announce a brand-new product designed to help you develop a strong security culture. SecurityCoach enables real-time …
Russian trolls and bots are back, targeting Tuesday’s U.S. midterms.
Steven Lee Myers at the NYT had the scoop on this typical Russian influence operation which really is social engineering at scale: "The user …
DHL Tops the List of Most Impersonated Brand in Phishing Attacks
As scammers shift their campaigns and learn from their successes, new data shows that the global delivery service is the current brand of …
New LinkedIn-Impersonated Phishing Attack Uses Bad Sign-In Attempts to Harvest Credentials
With compromised LinkedIn credentials providing cybercriminals with ample means to socially engineer business contacts, this campaign is a …
Number Matching Push-Based MFA Is Only Half the Solution
When push-based multifactor authentication (MFA) first came out, I was a big fan. I promoted it as a strong and safe MFA option in my book, …
Phishing for Feds: Credential-Harvesting Attacks Found in New Study
A study by researchers at Lookout has found that credential-harvesting phishing attacks against US government employees rose by 30% last year.…
FBI: Watch Out for Student Loan Forgiveness Scams!
Scammers are taking advantage of the victims desire to take advantage of debt cancellation up to $20,000 – with the only one cashing in being …
CheckPoint Warns of Black Basta Ransomware as the Number of Victim Organizations Increases by 59%
This latest “new kid on the block” is gaining momentum and – according to CheckPoint – seeing successes with their attacks globally, calling …
CISA Warns of Daxin Team Ransomware Group Targeting the Healthcare and Public Health Sector via VPNs
This new group makes the case that – as with any market – cybercriminals will focus on a niche sector they are experts on in order to improve …
KnowBe4 Wins 2022 "Best Software" Awards From TrustRadius in Multiple Categories
KnowBe4 is proud to be recognized by TrustRadius in the first-ever “Best Software” Awards for overall, mid-size, and enterprise in the …
Hacking Biometrics: If You Thought Your Fingerprints Were Safe, Think Again!
When you think of using biometric technology as part of your multi-factor authentication process, you assume these attributes are safe. …
Phishing-Resistant Does Not Mean Un-Phishable
Human societies have a bad habit of taking a specific, limited-in-scope fact and turning it into an overly broad generalization that gets …
[Scam of The Week] New Phishing Email Exploits Twitter’s Plan to Charge for Blue Checkmark
Michael Kan at PCMag had the scoop: A hacker is already circulating one phishing email, warning users they'll need to submit some personal …
What Happens to an Organisation When It Has No Security Culture?
Let’s begin by looking at what culture is and why it matters. Culture is tacit and elusive in its very nature. It is often unspoken, based on…
Australia's Lacking Cybersecurity Workforce Results to a Influx in Attacks
Australia has now become the newest target for attacks in part due to a overworked cybersecurity workforce that are not able to stop these bad…
[WARNING] Micro Transactions Lead to a Drained Bank Account
Our friend R. Friederich at Marshalsec sent us this warning...
LinkedIn Phishing Attack Bypassed Email Filters Because it Passed Both SPF and DMARC Auth
Researchers at Armorblox have observed a phishing campaign impersonating LinkedIn. The emails inform the user that their LinkedIn account has …
[EYE OPENER] Phishing Attacks 61% Up Over 2021. A Whopping 255 Million Attacks This Year So Far
Security Magazine wrote this week about the recent eye opening SlashNext State of Phishing report. "SlashNext analyzed billions of link-based…
The Number of Vulnerabilities Associated with Ransomware Grows 426% Over Three Years
With only 57 vulnerabilities tied to ransomware back in 2019, the most recent data from security vendor Ivanti shows that number predicted to …
Ransomware Attacks Via RDP Drop Significantly as Phishing Continues to Dominate
Since 2018, remote desktop compromise (RDP) and phishing have battled for dominance as the primary initial attack vector in ransomware …
Over Two-Thirds of Organizations Have No Ransomware-Specific Incident Response Playbook
A newly released report on ransomware preparedness shows organizations are improving their security stance in comparison to last year, but …
Your KnowBe4 Fresh Content Updates from October 2022
Check out the 29 new pieces of training content added in September, alongside the always fresh content update highlights and new features.
Stolen Devices and Phishing
Researchers at Cyren describe a phishing attack that resulted from the theft of a stolen iPad. The iPad was stolen on a train in Switzerland, …
[APPLY TODAY] Security Awareness Training Eligible for $185 million DHS Cybersecurity Grant Opportunity
The Department of Homeland Security (DHS) is providing $185 million of grant money this year to U.S. states and territories to bolster their …
KnowBe4 Top-Clicked Phishing Email Subjects for Q3 2022 [INFOGRAPHIC]
KnowBe4's latest quarterly report on top-clicked phishing email subjects is here. We analyze 'in the wild' attacks reported via our Phish …
Passkeys Are Being Pushed in a Big Way
There is a good chance that you and nearly everyone else will be using passkeys in the near future.
Don’t Let High-Tech Distract You from Low-Tech
Deepfakes, the realistic and thoroughly convincing fabrication of imagery, video, and audio that fakes the identity of some person in ways …
[Eye Opener] Work In IT? You Get Attacked Much More Than Other Employees
We received an interesting email from Elevate Security you need to be aware of. Their recent research showed: "Social engineering attacks are …
Major UK Outsourcer Hit With Multi-Million Dollar Fine Due to a Phishing Attack
Britain's data watchdog has fined major construction group Interserve with a £4.4m fine. This was due to a cyber attack stole personal and …
Phishing for Student Email Accounts
University student accounts are being exploited for business email compromise. Researchers at Avanan have observed a rise in attacks that …
BazarCall Expands Callback Phishing Campaigns to Include More Support Sites and Malicious Tactics
The king of callback phishing campaigns has evolved their methods to include better phishing emails, phone call scams, and final payloads to …
New Credential Harvesting Scam Impersonates Google Translate to Trick Victims
In an interesting twist, this latest scam identified by security researchers at Avanan attempts to establish legitimacy by making the victim …
[INFOGRAPHIC] 10 Tips for Running a Successful Compliance Training Program
Compliance training is often seen as a chore that organizations need to just get through. That said, compliance cannot simply be ignored. A …
New Phishing Attack Attempts to Steal Social Security Numbers
A phishing campaign is impersonating the US Social Security Administration (SSA) in an attempt to steal Social Security numbers, according to …
Phishing Targets US Election Workers
Researchers at Trellix warn of phishing attacks targeting election workers in advance of the US midterm elections. These attacks spiked ahead …
Scary Metaverse - Cybersecurity Risk Implications
The Metaverse, while still a concept at the moment, consists of the possibilities that arise when you combine the advances and affordability …
New COVID-19 Phishing Wave Misuses Google Forms to Steal Victim Information
This new credential harvesting scam impersonates a real U.S. Government COVID-related grant program to harvest credentials and personal …
91% of Organizations are Concerned About Ransomware Attacks in 2022
With ransomware attacks becoming more frequent, evasion getting more sophisticated, and ransoms increasing, new data shows organizations …
[HEADS UP] South African Post Office Sends Warning of Targeted Phishing Attacks
The South Africa Post Office (SAPO) recently warned customers of phishing emails to portray the post office. These cybercriminals are asking …
WSJ: "Cybersecurity Tops the CIO Agenda as Threats Continue to Escalate"
Steven Rosenbush at the WSJ reported: "Chief information officers say cybersecurity once again will be their top investment priority in 2023, …
Name-and-Shame Scams on Discord
Scammers are sending Discord messages with phony accusations to trick users into clicking on phishing links, according to Shan Abdul at …
How To Stop Job Scams
I am reading and hearing about a ton of job scams these days. So many, I wondered how anyone could get a real job or employee, especially in …
Sloppy but Dangerous: Fake Ransomware
Conventional ransomware encrypts the victims’ files and holds them hostage, unavailable to their owners, promising to provide a decryptor once…
Cyberattacks are the biggest risk to the UK financial system – Bank of England research
Cyberattacks are the biggest risk to the UK financial system, according to new research from the Bank of England.
New Phishing Campaign Uses Office Docs to Install Cobalt Strike Beacon
Under the guise of determining applicant eligibility for a U.S. federal government job, this latest phishing attack plants the seed for a …
Cyber-Zombie Apocalypse: Ransomware Gangs Continue to Come Back from the Dead
With ransomware gangs making so much money and then dropping off the face of the earth, what’s the motivation to come back to life and …
German Hackers Arrested for Stealing €4 Million in 7-Month Banking Phishing Scams
The recent arrest demonstrates how very small and unsophisticated a cybercriminal team can be to launch a very successful phishing campaign …
Small Business Grants as Phishbait
INKY has published a report on the use of small business grants as phishing lures. Scammers are impersonating the US Small Business …
Scams, Scams, Everywhere!
Scammers have been around as long as history has been recorded. Think about the famous ‘Trojan Horse’ for example. A perfect scam that allowed…
A New Phishing-as-a-Service Kit
Researchers at Mandiant have published an analysis of a phishing-as-a-service kit called “Caffeine,” which further lowers the bar for …
79 Million Malicious Domains Flagged in the First Half of 2022
Security researchers at Akamai identify an average of 13 million newly observed domains (NOD) each month this year, representing about 20% of …
Three-Quarters of Ethical Hackers Can Collect and (Potentially) Exfiltrate Data in 10 Hours or Less
New insight from the SANS Institute surveying 300 ethical hackers sheds some light on how they perceive your security stance – and how easy it…
Encrypted Files are the Overwhelming Way Organizations “Detect” Ransomware Attacks
New analysis of cyberattacks shows that organizations aren’t able to properly detect ransomware attacks, resulting in a majority of victims …
Could 100% of Phishing Be Eliminated One Day?
Occasionally you will hear people or organizations claiming that they are on the verge of eliminating all social engineering from reaching …
[Heads Up] Almost 19 percent of phishing emails bypass Microsoft Defender
Check Point Software is one of the world's best-known and largest infosec companies. In September 2021 they acquired email security company …
[Head Scratcher] The cyber insurance market is badly broken. But why exactly?
Greg Noone at the Techmonitor site covered this problem early October 2022, starting with a horror story.
KnowBe4 Celebrates Winning a Tech Cares Award From TrustRadius 2022
For the third consecutive year, we received a Tech Cares Award from TrustRadius! This third annual award celebrates companies that have gone …
Cybercriminal Faces Prison Time Over Romance Scams and Business Email Compromise Attacks
A man from Atlanta, Georgia has been convicted of running romance scams and business email compromise attacks that netted him over $9.5 …
Phishing Do's & Don'ts
Here are some do’s and don'ts for your phishing simulation exercises.
IRS Warns of A Spike in Smishing Attacks
The US Internal Revenue Service (IRS) has issued an alert warning of a significant rise in text message phishing scams (smishing) …
FCC Warns of Post-Hurricane Scams
The US Federal Communications Commission (FCC) offers advice on how to avoid falling for scams that follow in the wake of natural disasters …
KnowBe4 Named a Leader in the Fall 2022 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares Security Awareness Training (SAT) …
KnowBe4 Named a Leader in the Fall 2022 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR)
We are excited to announce that KnowBe4 has been named a leader in the Fall 2022 G2 Grid Report for Security Orchestration, Automation, and …
Cyber Risk Remains Top Concern for Businesses with a Distinct Lack of Unpreparedness
New insight from over 1200 businesses paints a picture of how organizations believe they are ready for an attack and are definitely focused on…
One-Fourth of Organizations Have Been Victim to a Ransomware Attack with 59% Starting with Email
New analysis highlights just how prevalent ransomware attacks are today, how material the impacts are, whether organizations get their data …
[HEADS UP] The Old "Nigerian Prince Scam" resurfaces as "Russian Billionaire Fraud"
Scammers continue to get creative when it comes to current events - and this new scam is no exception.
German Police Collar Alleged Phishing Cybercriminals
The Bundeskriminalamt (BKA), Germany's federal criminal police, raided three homes on Thursday, September 29th, in the course of an …
Trend Micro Reports Stolen Identities And Deepfakes
Researchers at Trend Micro warn that the social engineering potential of deepfakes is becoming an increasing concern. Deepfakes have already …
Reshaping the Threat Landscape: Deepfake Cyberattacks Are Here
Jai Vijayan, Contributing Writer at Dark Reading correctly stated: "It's time to dispel notions of deepfakes as an emergent threat. All the …
Response-Based Phishing Scams Targeting Corporate Inboxes Hit New Records
Setting a record for both highest count and share in volume with other types of phishing scams, response-based attacks are at their highest …
Your KnowBe4 Fresh Content Updates from September 2022
Check out the 35 new pieces of training content added in September, alongside the always fresh content update highlights and new features.
Social Engineering and Bogus Job Offers
Researchers at SentinelOne have warned that North Korea’s Lazarus Group is using phony Crypto.com job offers to distribute macOS malware. The …
A Master Class on Cybersecurity: Roger Grimes Teaches Password Best Practices
What really makes a “strong” password? And why are you and your end-users continually tortured by them? How do hackers crack your passwords …
American Airlines Traces Breach to Phishing Incident
American Airlines has disclosed that an attacker used phishing attacks to breach the company’s systems, BleepingComputer reports.
Top 5 Deepfake Defenses
Imagine you're on a conference call with your colleagues. Discussing the latest Sales numbers. Information that your competitors would love to…
87% of Organizations Rank Cyberattacks as the Number One Threat to Their Business
New data sheds a shocking light on just how inexperienced organizations are today in addressing cybersecurity needs – and the impact attacks …
FBI: Cyber Criminals Will Continue Targeting Healthcare Payment Processors Through Phishing Campaigns and Social Engineering
Despite the pandemic being largely considered over, a recent Private Industry Notification focused on the Healthcare industry indicates that …
Fake Emails Purporting to be from UK Energy Regulator
A phishing campaign is impersonating UK energy regulator Ofgem, according to Action Fraud, the UK’s cybercrime reporting centre.
Try the New Compliance Audit Readiness Assessment Today for the HIPAA Security Rule
When it's time to complete a compliance audit of your cybersecurity readiness plan, are you thinking, "Ugh, is it that time again?"
Recent Optus Data Breach Teaches the Importance of Recognizing Social Engineering
Optus, one of Australia's largest telecommunications companies, recently suffered a data breach that affected over 9.8 million customers.
Sentence in a Catphishing Case
A convict serving twenty-five years in South Carolina for voluntary manslaughter and attempted armed robbery, Darnell Kahn, has now also been …
You Need Aggressive Cyber Training, Not "So, So" Training
According to nearly every study conducted over the last decade, social engineering is involved in the vast majority of cyber attacks. The …
Retail is in Trouble: 77% Of Retail Organizations Have Been Hit by Ransomware
With Retail seeing and feeling the impact of more ransomware attacks than nearly every other industry, a new report focuses in on what the …
“Browser-in-the-Browser” Phishing Technique Spotted in New Steam Account Attack
Luring victims using a realistic- and legitimate-looking fake browser window to steal Steam accounts, this new type of social engineering may …
Phishing Campaign Targets GitHub Users
GitHub has issued an alert warning of a phishing campaign targeting users by impersonating the popular DevOps tool CircleCI, BleepingComputer …
[New Feature] Managing Your Risk and Compliance Tasks Just Got Easier with KCM’s Jira Integration
We’re thrilled to announce that Atlassian Jira integration support is now available with KnowBe4’s KCM GRC platform.
Security Practices Are Improving, But Cybercriminals Are Keeping Up
A survey by GetApp has found that the number of organizations using phishing simulations has risen from 30% in 2019 to 70% in 2022. Despite …
Phishing Attacks Reach an All-Time High, Quadrupling That of Early 2020
New quarterly data from the Anti-Phishing Working Group shows unprecedented phishing activity with increases in BEC, use of social media, …
Do Not Use Easily Phishable MFA and That Is Most MFA!
Everyone should use multifactor authentication (MFA), where they can, to protect valuable information. Everyone!
Social Engineering Targets Healthcare Payment Processors
The US Federal Bureau of Investigation (FBI) has issued an alert warning of an increase in phishing and other social engineering attacks …
[HEADS UP] Bank of America Warns About Recent Scams That Request Zelle Payment Due to 'Suspicious Activity'
Bank of America recently sent a customer service email warning users to watch out for this new phishing attack.
Uber security breach 'looks bad', caused by social engineering
iIt was all over the news, but ZDNet's Eileen Yu was one of the first. -- "Hacker is believed to have breached Uber's entire network in a …
Phishing from a French Government Career Website
Attackers are exploiting a legitimate French government website to send phishing messages, according to researchers at Vade. The website, Pôle…
[MSP News] Manage Your Multiple KnowBe4 Accounts Faster with Managed Training and Phishing Rolled Into One
You wanted the ability to manage both phishing and training campaigns across multiple KnowBe4 accounts, and we listened!
Cisco Attempt Attributed to Lapsus$ Group
Security researchers at Cisco Talos have issued an update on the cyberattack Cisco sustained earlier this year. The attack began with a …
Unconventional Security Awareness Advice
October is Cybersecurity Awareness Month, and you are undoubtedly being bombarded with some fantastic advice on how to stay cyber safe.
[HEADS UP] Online Scams on Queen Elizabeth's Death is Here
The Sun just reported that experts are sending a warning about online scams in relation to Queen Elizabeth's passing.
Scammer Continues Phishing From Prison
Dutch authorities have announced that an imprisoned scammer was running a phishing operation from his jail cell, Cybernews reports. The crook …
Ransomware Gangs Improve Attack Speed and Evade Detection with New "Intermittent Encryption" Tactic
As ransomware gangs look for new ways to improve their execution, this relatively new encryption tactic has been gaining popularity in …
Striving for 100% Completion Rates: Getting Compliance on Your Compliance Training
You might think 100% completion rates on any employee training sounds too good to be true. But, getting compliance on your compliance training…
Report: 80% of Phishing Attacks Leverage Legitimate Web Infrastructure and Services
Threat actors are taking advantage of every free tool and service they can to improve their changes of successfully fooling security …
Gaming-Related Phishing Trends
Researchers at Kaspersky have found that the vast majority of gaming-related malware lures are targeted at Minecraft players. Roblox came in …
PwC: More Frequent Cyber Attacks Tops the List of Business Risk for Executives
New data from PwC provides insight into what aspects of the business are executives focused on, worried about, and seeing as future challenges…
Singapore: Top Ten Scams in the First Half of 2022 Cost Over $227 Million, Scam Frequency Rises by 94%
Queries of reported cases to Singapore Police reveal a rise in scam costs by 59% as phishing cases double and job-related scams increase 7x …
Request a Demo of KnowBe4's PhishER Platform and Get Your Free Hat!
Phishing is still the No. 1 attack vector. Your users are exposed to malicious email daily. They can now report those to your Incident …
[New Training] Give Your Employees the Know-How to Have the Tough Conversations with New Compliance Plus Training
We’re thrilled to announce a brand new microlearning, TV-like production quality series of compliance content now available in the Compliance …
New Phishing-as-a-Service Platform
Researchers at Resecurity have discovered a new Phishing-as-a-Service (PhaaS) platform called “EvilProxy” that’s being offered on the dark …
Combatting Rogue URL Tricks: Quickly Identify and Investigate the Latest Phishing Attacks
Everyone knows you shouldn’t click phishy links. But are your end users prepared to quickly identify the trickiest tactics bad actors use …
Spear Phishing Campaign Targets Financial Institutions in African Countries
Researchers at Check Point have discovered a spear phishing campaign dubbed “DangerousSavanna” that's targeting financial entities in at least…
CyberheistNews Vol 12 #36 [Eye Opener] So, Your MFA Is Phishable, What to Do Next?
1-Time Passcodes Are a Corporate Liability. Department of Homeland Security Fraud Warning. Email not …
Building a Security Culture With Behavior Design
Anyone who has run security awareness programs for a while knows that changing human behaviour is not an easy task. And that sometimes the …
Register for KB4-CON EMEA 2022 Now!
Once again we are hosting a special KB4-CON Virtual Summit for all of our customers and partners in Europe, the Middle East, and Africa with …
REvil Springs Back to Life and Hits a Fortune 500 Company
The previously-thought defunct cybercriminal gang appears to not only reopened for business but has re-established themselves as a major …
The Number of Phishing Attack Cases in Japan Hit an All-Time High
The number of reported cases of phishing to Japan’s Council of Anti-Phishing reached over 100,000 in July, just as a notice of scams …
Instagram Phishing: Scammers Exploit Instagram Verification Program
Researchers at Vade warn that an email phishing campaign is informing users that their Instagram account is eligible to receive a blue …
Fraud Warning from DHS OIG
The Department of Homeland Security’s Office of the Inspector General (DHS OIG) has issued an alert to warn that scammers are posing as DHS …
Your KnowBe4 Fresh Content Updates from August 2022
Check out the 50 new pieces of training content added in August, alongside the always fresh content update highlights and new features.
So, Your MFA is Phishable, What To Do Next
We’ve written a lot about multi-factor authentication (MFA) not being the Holy Grail to prevent phishing attacks, including here:
Lost in Translation? New Cryptomining Malware Attacks Based in Turkey Cause Suspicion
Researchers at Check Point warn that attackers based in Turkey are distributing cryptomining malware via free software distribution websites, …
Phishing Attacks Leveraging Legitimate SaaS Platforms Soars 1100%
As threat actors look for ways to evade detection by security solutions, the use of cloud applications has seen a material jump in the last 12…
Phishing and Malicious Emails Are Still the Primary Initial Attack Vector
As cybercriminals continue to evolve their techniques, they continue to rely on phishing as the most successful tried and true method of …
LockBit Ransomware Group Steps Up Their Game with Triple Extortion as the Next Evolution
After suffering a taste of their own medicine as part of a response effort from victim organization Entrust, LockBit appears to have bounced …
[KREBS ON SECURITY] How 1-Time Passcodes Became a Corporate Liability
[The following article is at it appears at Krebs on Security here.] Phishers are enjoying remarkable success using text messages to steal …
The Extent of Social Engineering
Researchers at NordVPN have published the results of a survey that found that 84% of Americans have experienced some form of social …
Researchers warn of darkverse emerging from the metaverse
ARN just reported: "The metaverse is seen by many companies as a great business opportunity and for new ways of working. Security provider …
The Crypto Collapse Will Only Add Fuel to the Cyberattack Fire
Despite the crypto market’s loss of over $1 trillion in value since the beginning of the year, the value of the digital currency isn’t what …
BlackByte Ransomware Gang Comes Back to Life with a New Extortion Strategy
First debuted in July 2021, this ransomware gang that engages in their own attacks and offers a RWaaS model, has come back into the limelight …
Phishing Remains the Initial Infection Vector in 78% of Attacks Against OT-Heavy Industries
Companies heavily reliant on operational technology (OT) to function are just as much a target as businesses relying in traditional IT and are…
Report: Deepfakes Used in Scams
Scammers created a deepfake video of Patrick Hillmann, Chief Communications Officer at cryptocurrency exchange Binance, in order to scam …
[HEADS UP] Highly Sophisticated Job Offer Scam
If you've been approached by recruiters on LinkedIn for a potential job opportunity, you may want to pay attention to this recent scam.
State-Based Cyberattacks to be Excluded from Lloyd’s of London Cyber Insurance Policies
As cyber insurers evolve their understanding of the cyber attack landscape, who’s responsible, and what’s at stake, a logical next step is …
Dueling Clauses, or, not all Fraud is the Same
There are, famously, three things you can do with risk: accept it, mitigate it, or transfer it. And you transfer risk by buying insurance …
[BUDGET AMMO] Companies Are Ditching Cybersecurity Insurance as Premiums Rise, Coverage Shrinks
As the CEO of a public InfoSec company I have a variety of news sources. One of these is called '"The Information" which covers in-depth tech …
Teach Two Things to Decrease Phishing Attack Success
We know everyone is busy. Everyone already has too much on their plate and is trying to learn as much as they can every day.
Vishing is a Rising Threat to the Enterprise
Most of us are all too familiar with vishing, the scam voice calls that offer to erase your credit card debt, to extend your automobile …
On this Carousell Ride, the Crooks Take the Brass Ring.
In a variation on a recently seen theme in which scammers pose as buyers on e-commerce platforms, victims in Singapore are being taken in by …
[FREE RESOURCE KIT] Cybersecurity Awareness Month 2022 Now Available
Cybersecurity Awareness Month is right around the corner, and we’ve got you covered! Your complimentary resource kit for 2022 is now available.
[Whoa] Ransomware Strains Almost Double in Six Months from 5,400 to 10,666
A recent report from FortiGuard Labs saw ransomware variants double in total so far compared to 2021, and the year is not over yet.
Piggybacking: Social Engineering for Physical Access
Tailgating or piggybacking is an old but effective social engineering technique to gain physical access to restricted areas, according to …
One-Third of Organizations Experience Ransomware Attacks At Least Weekly
New data shows attempted ransomware attacks are occurring far more frequently while a lack of confidence is found in security measures and …
Impersonation Phishing Attacks Increase as Credentials Take the Lead as the Primary Target
New data shows an upswell of email-based cyberattacks, with over 256 brands being impersonated, as social media, Microsoft, shipping, and …
Hybrid Vishing Attacks Increase 625% in Q2
Reaching a six-quarter high in Q2, hybrid vishing attacks have increased six times that of the hybrid-vishing attacks experienced in Q1 2021.
Organizations Holding Cyber Insurance Policies May Get Stuck with the Bill in a Phishing Loss
Plenty of new anecdotal and legal case-based stories are demonstrating that just because your organization has a policy doesn’t mean it’s …
Social Engineering for Espionage and Influence
Microsoft has disrupted operations carried out by a Russian government-aligned threat actor tracked as “SEABORGIUM.” The threat actor uses …
More Super Targeted Spear Phishing Ahead
Hardly a day goes by without a news alert about the latest HUGE data breach. It’s so commonplace today that it rarely rates showing at the top…
Children of Conti go Phishing
Researchers at AdvIntel warn that three more ransomware groups have begun using the BazarCall spear phishing technique invented by the Ryuk …
Initial Access Broker Phishing
Cisco has disclosed a security incident that occurred as a result of sophisticated voice phishing attacks that targeted employees, according …
U.S. Government Warns of Increased Texting Scams as Mobile Attacks are Up 100%
Cyberattacks via SMS messaging are on the rise, and are having such an impact, the Federal Communications Commission has released an advisory …
Massive Network of Over 10,000 Fake Investment Sites Targets Europe
Using a mix of compromised social media accounts, social engineering, call center agents, and some convincing websites, this latest scam seeks…
Phishing-as-a-Service Platform “Robin Banks” Helps Cybercriminals Target Customers of Financial Institutions
Initial Access Brokers (IABs) are one of the new breeds of cybercrime services. But this newest PhaaS platform makes it easy for anyone to …
92% of Organizations Have Experienced a Security Incident as a Result of an Email-Borne Threat
New data shows that not only are email-borne threats increasing, but that current integrated cloud email security solutions do little to …
New Paypal Phishing Scam Uses “Legitimate” Invoices to Reach Victim Inboxes
Newer phishing scams are looking for ways to make legitimate websites do the work of delivering malicious messages to unsuspecting victims – …
SolidBit Ransomware Targets League of Legends Players
Researchers at Trend Micro warn that a SolidBit ransomware variant is being distributed via fraudulent software targeting video game players …
Recent Cisco Hack by Ransomware Group Started Because of a Phishing Attack
In a recent article by Forbes, Cisco confirmed that they were hacked by a ransomware group as the group of cybercriminals published a partial …
The Top 8 Most Common Types of DNS Records
This article is a good technical overview of DNS that can help you prevent spoofing. This is a cross-post from the EasyDMARC blog, a new …
DPRK Operators Impersonate CoinBase
North Korea’s Lazarus Group is running a new phishing campaign targeting Coinbase accounts, BleepingComputer reports. The threat actors are …
New Phishing Campaign is Now Targeting Coinbase Users
If you're a Coinbase user, you are most likely the next target of a new phishing campaign. Cybercriminals have managed to infiltrate …
Hacking the Hacker: Assessing and Addressing Your Organization’s Cyber Defense Weaknesses
Cybercriminals are out there, watching and waiting for the perfect opportunity. They are gathering information about your organization and …
Cash App Scams Strikes Again With New Types of Attacks
TradeArabia has published a report about common scams on CashApp, explaining that scammers frequently take advantage of CashApp promotions, …
New Research Shows Social Engineering and Phishing are the Top Threats
According to the CS Hub Mid-Year Market Report 2022, new findings shows that 75% of survey respondents believe that social engineering and …
Twilio hacked by phishing campaign targeting internet companies
Communications giant Twilio has confirmed hackers accessed customer data after successfully tricking employees into handing over their …
WSJ: "Cyber Insurance Prices Soar"
The WSJ reported Aug 8, 2020: It is becoming more expensive and difficult for companies to get or renew cyber insurance. The price of U.S. …
Cybercriminals Go to College with New Phishing Attacks
The summer is winding up, and the traditional academic year is approaching. And amid the welcomes from the deans of students, the activities …
LinkedIn Continues its Reign as the Most-Impersonated Brand in Phishing Attacks
As cybercriminals look for novel and effective ways to gain entrance to a victim network, LinkedIn is proving to be fruitful enough to keep …
Ransomware Attack Downtime Costs in the U.S. Rise to Nearly $160 Billion
New data based on tracked, publicly-confirmed ransomware attacks shows that downtime – and the associated cost – is increasing at an alarming …
Open Redirects Exploited for Phishing
Attackers are exploiting open redirects to distribute links to credential-harvesting sites, according to Roger Kay at INKY. The attackers are …
KnowBe4 Wins Multiple Summer 2022 "Best of" Awards From TrustRadius
KnowBe4 is proud to be recognized by TrustRadius with the Summer Best of Awards in three categories for the Security Awareness Training …
On-Demand Webinar: New 2022 Phishing By Industry Benchmarking Report: How Does Your Organization Measure Up
As a security leader, you have a lot on your plate. Even as you increase your budget for sophisticated security software, your exposure to …
Labor Market Social Engineering: Supply-Side and Demand-Side
We’re accustomed to social engineering being used for credential theft and business email compromise. We’re also accustomed to hearing about …
New Data Breach Extortion Attack Begins with a Fake Duolingo or MasterClass Subscription Scam
The cybercriminal gang, dubbed ‘Luna Moth’ uses a sophisticated mix of phishing, vishing, remote support sessions, and remote access trojans …
Security and Gender: The Gaps Are Not Where You Expect
The 2022 KnowBe4 Women’s Day Survey interviewed more than 200 women from across the technology industry in South Africa to find out more about…
Cyber Insurance Expected to Continue to Rise as Sophistication and Cost of Ransomware Attacks Increase
New data about the state of cyber insurance shows that given the current loss ratios by insurers – and the reasons behind those losses – will …
Experian Customer “Impersonation” Account Takeover Uncovered by KrebsOnSecurity
After a few notifications of a potential problem with Experian by his readership, Brian Krebs and team checked out Experian’s account signup …
A Widespread, Multistage Investment Scam
A complex and ambitious investment scam has used more than 10,000 domains to induce speculators to give up not just funds, but personal …
Happy 23rd Annual SysAdmin Day from KnowBe4!
It's been 23 years of celebrating all of our fellow System Administrators! Your hard work on daily maintenance of your company's day-to-day …
Your KnowBe4 Fresh Content Updates from July 2022
Check out the thirteen new pieces of training content added in July, alongside the always fresh content update highlights and new features.
Phishing-Based Data Breaches Take 295 Days to Contain as Data Breaches Soar to $4.91 Million
Fresh data on data breach costs from IBM show phishing, business email compromise, and stolen credentials are the longest data breaches to …
Beware of Sophisticated Malicious USB Keys
Malicious USB keys have always been a problem. There is almost no professional penetration testing team that does not drop a handful of USB …
Spear Phishing Campaign Targets Facebook Business Accounts
Researchers at WithSecure have discovered a spear phishing campaign targeting employees who have access to Facebook Business accounts. The …
IBM: Phishing is the Most Common Way to Gain Access to Victim Networks
New research from IBM shows four reasons why phishing attacks are still effective and remains the primary attack vector in 41% of cyberattacks.
Microsoft 365 Users are Once Again the Target of Phishing Scams using Fake Voice Mail Messages
Using a simple email containing a voice mail attachment, an ingenious phishing attack captures credentials while keeping track of the domains …
Hackers Use Free Email Accounts from QuickBooks to Launch Spoofed Phishing Attacks
A new attack uses one brand email domain to increase the chances of reaching an Inbox, while spoofing another brand to trick users into …
KnowBe4 Top-Clicked Phishing Email Subjects for Q2 2022 [INFOGRAPHIC]
KnowBe4's latest quarterly report on top-clicked phishing email subjects is here. We analyze 'in the wild' attacks reported via our Phish …
Nearly Half of Organizations Have Experienced Vishing
Forty-seven percent of organizations have experienced voice phishing (vishing) attacks over the past year, according to researchers at Mutare.…
New Report Reveals that Ransomware and Business Email Compromise Attacks Cause Nearly 70% of Cyber Incidents
Do you know your organizations true security risk and where to prioritize your resources? A new report from Palo Alto Networks sheds some …
[BEWARE] Microsoft and Facebook are the Most Abused Brands for Phishing Attempts
We all know that big brands can be exploited by bad actors in order to execute successful phishing attacks. Now a new study is showing …
Malvertising With Google Ads
Researchers at Malwarebytes warn that a large malvertising campaign is exploiting Google ads to redirect users to phishing sites.
Reported USB Scam Shows the Importance of Security Awareness Training
Just when you thought scammers couldn't get more tricky in their attacks, this example will prove you wrong.
Ransomware Groups Get Smaller and More Social
The Colonial Pipeline ransomware attack of 2021 put infrastructure operators on notice that they were directly in the crosshairs of big …
Striving for 100% Completion Rates: Getting Compliance on Your Compliance Training
At the last few conferences I have attended and spoken at, including our own KB4-CON 2022, I noticed a question that many people have …
[Heads Up] Huge Losses Caused By Epidemic of ‘Pig Butchering’ Scams
Investigative reporter Brian Krebs reported today that U.S. state and federal investigators are being inundated with reports from people …
Job Seekers and Employers Beware!
With record low unemployment, a tight labor market, and increasing customer demand, everyone says it is an employee’s job market out there. …
FBI Warns of Phony Cryptocurrency Investment Apps
Cryptocurrency investors have lost nearly $43 million to fraudulent cryptocurrency investment apps, according to the US Federal Bureau of …
Cybersecurity Should be an Issue for Every Board of Directors
With so many Boards focused on operations, revenue, strategy, and execution, they completely are forgetting the simple fact that a single …
New Multi-Factor Authentication Prompt “Bombing” Attacks Give Access to Laptops, VPNs, and More
While multi-factor authentication (MFA) significantly reduces an organization’s threat surface by making the stealing of credentials much …
Copyright Claim Email is a LockBit Ransomware Phishing Attack in Disguise
The latest iteration in Copyright Claim scams is an evolution of this repeated attack method that has proven to get the attention – and …
Phishing Kit Imitates PayPal
Researchers at Akamai have discovered a PayPal phishing kit that attempts to steal victims’ identities as well as their financial information.…
Ransomware Group Conti Reaches 40 Successful Attacks in a Single Month
In less than 2 years, the most successful ransomware group to date has reached new levels of campaign and individual attack effectiveness, …
Phishing Attacks are the Most Prevalent Source of Identity-Related Breaches
Cybercriminals almost always need to leverage credentials as part of just about any kind of cyberattack. To no surprise, phishing and social …
Facebook-Themed Scam Aims to Steal Your Credentials
A creative mix of phishing emails, solid social engineering, use of Facebook Messenger, brand and site impersonation, and a sense of urgency …
Hovering Over Links Will Protect You More Than MFA
Microsoft Security recently released a report which detailed a widely successful phishing attack technique used against over 10,000 of its …
Watchdog Uncovers 12% of Google Ads for Student Loan Relief Could be Malicious
You may want to be careful about clicking on a student loan forgiveness ad. The Tech Transparency Project reviewed the top Google searches …
QuickBooks Phishing Scam is Back
Scammers are continuing to abuse the QuickBooks tax accounting software to send phishing scams, according to Roger Kay at INKY.
Hacks That Bypass Multi-Factor Authentication and How to Make Your MFA Solution Phishing Resistant
The average person believes using Multi-Factor Authentication (MFA) makes them significantly less likely to be hacked. That is simply not …
Phishing Attack Steals $8 Million Worth of Cryptocurrency
Scammers stole $8 million worth of Ethereum from users of the Uniswap cryptocurrency exchange, according to Sujith Somraaj at Decrypt. …
KnowBe4’s 2022 Phishing By Industry Benchmarking Report Reveals that 32.4% of Untrained End Users Will Fail a Phishing Test
Once again, the human layer continues to be the most desirable attack vector for cybercriminals. 2022 marks the 5th year KnowBe4 has analyzed …
New Phishing Attacks Shame, Scare Victims into Surrendering Twitter, Discord Credentials
A new wave of social media phishing attacks are now using scare tactics to lure victims into sending their logins.
Callback Malware Campaigns Impersonate CrowdStrike and Other Cybersecurity Companies
CrowdStrike sent the following Tech Alert to their customers
Multi-Medium Phishing Tactics Increase Attack Effectiveness by 300%
New data from IBM shows how attackers are leveraging more than just email to elevate their chances of reaching their malicious goals – and …
All it Takes is “Free” Beer to Steal Your Personal Data
A recent phishing scam impersonating the Heineken beer brand demonstrates how very little effort is needed by scammers to convince victims to …
Amazon Prime Day Phishing
Check Point Research (CPR) observed a 37% increase in Amazon-themed phishing attacks during the first week of July, ahead of Amazon Prime day …
KnowBe4 Named a Leader in the Summer 2022 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR)
We are excited to announce that KnowBe4 has been named a leader in the Summer 2022 G2 Grid Report for Security Orchestration, Automation, and …
KnowBe4 Named a Leader in the Summer 2022 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares Security Awareness Training (SAT) …
[Scam of the Week] Amazon Prime Day or Amazon Crime Day? Don’t Fall Victim to Phishing
As Amazon Prime Day approaches, Checkpoint research is sending a warning that Amazon Prime Day scams will ramp up very soon.
Lessons Learned from a Popular Hotel's Recent Data Breach Involving Social Engineering
This week Marriott International, one of the largest hotel chains, suffered a second data breach of 2022. The breach took place in early June …
One Employee’s Desire for a New Job Cost His Employer $540 million
A “Fake Job” scam allows cybercriminals to gain entrance to the network at Sky Mavis, makers of the game Axie Infinity, and eventually take …
Your KnowBe4 Fresh Content Updates from June 2022
Check out the 68 new pieces of training content added in June, alongside the always fresh content update highlights and new features.
Breaches & Cyberwar Driving Security Culture
Cybersecurity Culture is a hot topic amongst many organisations and security professionals. But what are organisations doing to build a strong…
FBI Issues Warning on China for Attempting to 'Ransack' Western Companies
Bloomberg recently reported that FBI Director Christopher Wray issued a warning to Western companies that China wants to 'ransack' their IP. …
Phishing Campaign Impersonates the UAE
Researchers at CloudSEK have observed a financially motivated phishing campaign that’s impersonating the United Arab Emirates (UAE) Ministry …
Expect More Travel-Themed Phishing Scams as 80% of Americans Plan to Travel
The lure of last-minute deals to get away after staying home for the last 2 years is so strong, scammers are using it to their advantage with …
New WhatsApp Scam Uses Call Forwarding Social Engineering to Hijack Accounts
This is a great example of how even the simplest of social engineering tactics can be used as the first step in a likely-larger scam. In a …
New Phishing Campaign is Targeting TrustWallet With Impersonation Emails
Vade Secure warns that a phishing campaign is targeting TrustWallet cryptocurrency wallet users with phony verification emails.
Ransomware Gang Creates “User-Friendly” Stolen Data Search Site for Employee Victims
In an interesting extortion twist to get ransomware victims to pay up, one gang has created a search site to allow employees to see if their …
Phishing Emails Top the List as the Initial Attack Vector for Ransomware Attacks
The latest data on ransomware trends from backup vendor Veeam demonstrate the impact these attacks have on backups and an organization’s …
Email-Based Threats Double as Malware, Credential Phishing, and BEC Detections Increase
Newly released data from TrendMicro about high-risk email threats in 2021 shows where cybercriminals are placing their focus and where yours …
[FREE Resource Kit] July Is Ransomware Awareness Month
July is Ransomware Awareness Month, and we’ve got you covered with free resources!
New Phishing Campaign Impersonates Canada Revenue Agency
A phishing campaign is impersonating the Canada Revenue Agency (CRA) in an attempt to steal Canadians’ personal information, according to Rene…
[New FBI and CISA Alert] This ransomware strain uses RDP flaws to hack into your network
As of May 2022, MedusaLocker has been observed predominantly exploiting vulnerable Remote Desktop Protocol (RDP) configurations to access …
Celebrity Crypto Scams Just Keep on Getting Worse
Bloomberg News recently reported that fake celebrity-endorsed crypto scams have doubled in the UK this year, and on average scammed victims …
[Heads Up] Online Fraud Now Sky-high With 'Tinder Swindler' Romance Scams Costing Hundreds of Millions
A new article in Bloomberg focused on new sky-high online fraud numbers, they are horrendous. Here is a short summary and I recommend you read…
Wars and Lechery, Nothing Else Holds Fashion for Phishing Attacks
Shakespeare said it first, and things haven’t changed: suffering and desire continue to drive victims to the social engineers. Researchers at …
Bad News to Ransom Payers: 80% of You Will Face a Second Attack Within 30 Days
New insight into what happens during and after a ransomware attack paints a rather dismal picture of what to expect from attackers, your …
80% of Organizations Await “Inevitable” Negative Consequences From Email-Born Cyberattacks
With nearly every organization experiencing some form of phishing attack, new data suggests these attacks are improving in sophistication, …
New Evasive Phishing Techniques Help Cybercriminals Launch “Untraceable” Campaigns
Scary new details emerge of cybercriminals using reverse tunneling and URL shorteners to evade detection by security solutions, allowing them …
Innovative Way to Bypass MFA Using Microsoft WebView2 Is Familiar Nevertheless
An interesting way to bypass multi-factor authentication (MFA) was recently announced by Bleeping Computer. This particular attack method …
FBI Warns of Deepfakes Used to Apply for Remote Jobs
If you're looking for your company's next remote IT position, you may want to think twice before doing so. The FBI recently reported to the …
Try the new Compliance Audit Readiness Assessment today for the NIST Cybersecurity Framework
When it's time to complete a compliance audit of your cybersecurity readiness plan, are you thinking, "Ugh, is it that time again?"
MetaMask Crypto Wallet Phishing
A phishing campaign attempting to steal credentials for MetaMask cryptocurrency wallets, according to Lauryn Cash at Armorblox.
Amazon Prime Day 2022 is Coming: Here are Quick Cybersecurity Tips to Help You Stay Safe
Amazon Prime Days this year are July 12 - 13th 2022. As a result, cybercriminals are taking every step to capitalize on the holiday with new …
Technology, Microlearning, and its Impact on Users and Cybersecurity
Technology is everywhere in society these days from our communication, shopping, and commerce capabilities. Whether email, online purchases, …
Pre-Hijacking of Online Accounts are the Latest Method for Attackers to Impersonate and Target
Rather than run a complex credential harvesting phishing scam, attackers use existing information about their victim and hijack a popular web …
“Failure to Authenticate” Wire Transaction at the Heart of a Cyber Insurance Appeal Case
Lawsuits over denied cyber insurance claims provide insight into what you should and shouldn’t expect from your policy – and that actions by …
Phishing Scammers Leverage Telegraph’s Loose Governance to Host Crypto and Credential Scams
The free and unmonitored webpage publishing platform has been identified as being used in phishing scams dating back as early as mid-2019, as …
Vendor Impersonation Competing with CEO Fraud
Researchers at Abnormal Security have observed an increase in vendor impersonation in business email compromise (BEC) attacks.
[Heads Up] Russia has increases the cyber attacks against countries that help Ukraine
The Wall Street Journal just reported that Russian intelligence agencies have increased the pace of cyberattacks against nations that have …
Spear Phishing Campaign Targets the US Military
Researchers at Zscaler warn that a spear phishing campaign is targeting the US military and other sectors with phishing emails that purport to…
FBI Warns of Fraudsters on LinkedIn
The US FBI has warned that scammers on LinkedIn are a “significant threat,” CNBC reports. Sean Ragan, the FBI’s special agent in charge of the…
KnowBe4 June 2022 Perspective
Information Security is mission-critical today.The global risk situation is higher than ever.Your employees are still your largest attack …
Smishing Text Scams Have Doubled in the Last Three Years
New data shows a rise in the use of text messages as an effective vehicle to connect with potential victims for social engineering scams as …
New PDF-Based Phishing Attack Demonstrates that Office Docs Aren’t Passé – They are Just Obfuscated!
Security researchers have discovered a cunning PDF-based phishing attack that leverages social engineering and PDF prompt specifics to trick …
Over 2000 Social Engineering Scammers Arrested in Multi-Country Crackdown on Fraud, BEC, and Money Laundering
Thousands of members of cybercriminal groups were arrested in a sting that lasted 2 months and involved coordinated efforts of the law …
Vishing Attacks Increase 550% Over Last Year as the Financial Sector Continues to be a Primary Target
Cybercriminals are continuing to bypass the use of malware in favor of response-based and credential-centric social engineering attacks, …
142 Million Customer Records From MGM Resorts Leaked for Free Download
The availability of such a massive number of records at no cost to any cybercriminal interested is a recipe for countless phishing campaigns …
New Phishing Campaign Uses ChatBot Functionality to Build Trust and Steal Credit Card Details
Rather than go for the phishing jugular and point the victim immediately to a webpage to steal credentials or personal details, a new phishing…
The Next Evolution in Cyberattacks You Need to Worry About: AI
New testimony to U.S. Senate Armed Services Committee Subcommittee on Cybersecurity by Microsoft’s Chief Scientific Officer sheds light on …
Less Than 40% of Asia-Pacific Organizations Are Confident to Stop Cyber Threats as 83% Experience At Least One Ransomware Attack a Year
With exactly half of cybersecurity incidents caused by organizations having an outdated security posture, the ability to stop breaches …
Anna Collard, SVP Content Strategy & Evangelist, KnowBe4 Africa Has Been Acknowledged as a Global Influencer in Cyber
IFSEC Global recently acknowledged our very own Anna Collard as a IFSEC Global Influencer in Security for 2022! She was one of the few …
A Closer Look at HR Scams: Does Niceness Have a Downside?
Threat actors are targeting HR employees who are looking to hire new people, according to Lisa Vaas at Contrast Security. As part of their …
Spear Phishing Campaign Targets Former Israeli Officials
An Iranian threat actor is conducting a spear phishing operation against Israeli officials, according to researchers at Check Point. The …
Monkeypox Scams Continue to Increase
Attackers are taking advantage of the current news about monkeypox to trick people into clicking on malicious links, Pickr reports. …
Facebook Phishing Scam Steals Millions of Credentials
Researchers at PIXM have uncovered a major Facebook Messenger phishing scam that’s “potentially impacted hundreds of millions of Facebook …
Approaching Ransomware Victims Privately
Researchers at KELA warn that ransomware gangs are increasingly refraining from mentioning their victims’ names after the initial attack, …
What About Password Manager Risks?
In KnowBe4’s new Password Policy ebook, What Your Password Policy Should Be, we recommend that all users use a password manager to create and …
Karakurt Adds Irritating Phone Calls to its Crimes
The US Cybersecurity and Infrastructure Security Agency (CISA) and its partners have issued a joint alert on Karakurt, a data theft extortion …
Phishing Attacks Reach an All-Time High, More Than Tripling Attacks in Early 2022
Reaching more than 1 million attacks in a single quarter for the first time, new data on phishing attacks in Q1 of 2022 show an emphasis on …
40% of CSOs say Their Organization is Not Prepared for Cyberattacks as Phishing is the Top Likely Cause of Breaches
A new survey of executives sheds light on how well organizations fared with cyberattacks in the last 12 month as well as what attack vectors …
Old Dog, New Trick: Hackers Use Logons in URLs to Bypass Email Scanners
A new phishing method uses a decades-old special URL format to take advantage of how security solutions and email clients interpret URLs, …
“Five Eyes” Nations Cybersecurity Authorities Issue Warning to MSPs of Stepped-Up Cyberattacks
The world’s five leading cybersecurity authorities have again issued a joint report about an increase in malicious cyber activity targeting …
The Good, the Bad, and the Necessary State of Cyber Insurance
New data from security vendor Sophos shows that while the presence of cyber insurance coverage has increased, it’s the experiencing of attacks…
FTC Warns that Scammers are Turning to Cryptocurrencies
The US Federal Trade Commission (FTC) has warned that people have reported losing over $1 billion in crypto to scams since the beginning of …
What is a security tech stack
What is a security tech stack? This is a bare-bones quick overview.
[Live Demo] Ridiculously Easy Security Awareness Training and Phishing
Old-school awareness training does not hack it anymore. Your email filters have an average 7-10% failure rate; you need a strong human …
Homographic Domain Name Phishing Tactics
Bitdefender warns that Microsoft Office applications are vulnerable to phishing tactics that exploit international domain names (IDNs). …
Understanding the Threat of NFT and Cryptocurrency Cyber Attacks and How to Defend Against Them
A growing number of organizations worldwide are utilizing cryptocurrency for a host of investment, operational, and transactional purposes. …
Why We Recommend Your Passwords Be Over 20-Characters Long
KnowBe4 just released its official guidance and recommendations regarding password policy. It has been a project in the works for many months …
Introducing KnowBe4’s Password Policy E-Book
KnowBe4 just released its first e-book covering password attacks, defenses and what your password policy should be. Here is a summary of its …
Your KnowBe4 Fresh Content Updates from May 2022
Check out the 26 new pieces of training content added in April, alongside the always fresh content update highlights and new features.
U.K.’s National Health Service Becomes the Latest Victim of a Credential Harvesting Phishing Operation
Part of a six-month attack, email accounts on the NHS’ Microsoft 365 instance were compromised, resulting in over 1,100 targeted email attacks…
Smishing and Home Delivery
A smishing campaign is impersonating the UK-based delivery company Evri with text messages informing recipients that their package couldn’t be…
SideWinder Targets Pakistani Entities With Phishing Attacks
The India-aligned APT SideWinder is using a variety of social engineering techniques to target Pakistani government and military entities, …
U.K.’s National Health Service Becomes the Latest Victim of a Credential Harvesting Phishing Operation
Part of a six-month attack, email accounts on the NHS’ Microsoft 365 instance were compromised, resulting in over 1,100 targeted email attacks…
Phishing Attacks Rise 54% as the Initial Attack Vector Across All Threat Incidents
As cybercriminal groups hone their craft, one analysis shows them shying away from zero-day exploits, use of valid accounts, and third-party …
The Business (and Success) of Ransomware Explained as a Simple Funnel
The rise of Ransomware-as-a-Service has given rise to a number of more successful groups who have their “business” down to a simple exercise …
Phishing Campaign Targets QuickBooks Users
Accounting software provider Intuit has warned of a phishing scam targeting its customers, BleepingComputer reports. The phishing campaign …
We Do Not Talk Enough About Social Engineering and It’s Hurting Us
One of the most important things I have tried to communicate to audiences since at least the 1990s is how prevalent a role social engineering …
The $44 Billion Smishing Problem and How to Not Be a Victim
Consumer Affairs reported on how big of a problem SMS phishing scams have become, and how it's about to get a lot worse. According to a recent…
Collaring the (Alleged) Leader of a BEC Gang
A joint operation by INTERPOL and the cybercrime unit of the Nigeria Police Force have concluded a yearlong investigation into the …
Verizon: Ransomware Involved in 25% of Data Breaches as Credentials and Phishing are Seen as “Key Paths” for Attack Success
With the much-anticipated annual Verizon Data Breach Investigations Report finally released, we get a view of ransomware from the data breach …
That’s Not Actually Elon Musk
Scammers are using deepfake videos of Elon Musk in an attempt to trick people into handing over cryptocurrency, BleepingComputer reports. The …
New Scam Uses Fraud Support Social Engineering to Take Victims for Thousands of Dollars
A new scam borrows a page from the tech support scams that target older victims telling them potential fraud has been found, offering to …
Phishing Scammers Benefit from Shady SEO Practices to Rank Better Than Legitimate Domains
So-called “Black Hat SEO” services have popped up on Dark Web forums bringing advantageous search results to anyone willing to pay a small …
New IRS Phishing Scam Uses Fake Notices to Steal Microsoft 365 Credentials
Scammers use an “overdue tax bill” along with a sophisticated and obfuscated javascript-based “invoice” attachment to identify targeted …
FBI Director Warns of “Unprecedented” Cyberespionage Attacks Originating in China
FBI Director Christopher Wray highlighted China’s role in cyberespionage in a recent 60-Minutes news segment, saying the level of attacks the …
New Phishing Attack Uses Malicious Chatbot For Real Time Social Engineering
Researchers at Trustwave have observed a phishing campaign that uses a chatbot to add legitimacy to the scam. The chatbot is on a harmless …
Don't Just Have a Compliance Season, Have a Culture of Compliance
“We want compliance training to be impactful like your security awareness training.”
Phishing Attacks Increase by 54% as Initial Attack Vector for Access and Extortion Attacks
New analysis of threat activity for the first quarter of this year shows anyone with access to corporate email is a now on the front lines of …
It's More Than Phishing; How to Supercharge Your Security Awareness Training
Tell people not to click a link, pat each other on the back, and ride off into the sunset. If only security awareness training was that simple…
Phishing Campaign Impersonates Shipping Giant Maersk
Researchers at Vade Secure warn of a large phishing campaign that's impersonating shipping giant Maersk to target thousands of users in New …
WSJ: "Cyber Insurance Went Up A Whopping 92% In 2021"
Whoa Nellie, that's getting to be real money here. This is the kind of thing that starts cutting into your whole IT budget.
Spear Phishing a Diplomat
Researchers at Fortinet observed a spear phishing attack that targeted a Jordanian diplomat late last month. The researchers attribute this …
Why People Fall for Scams
Scammers use a variety of tried-and-true tactics to trick people, according to André Lameiras at ESET. For example, they can easily find …
Think BEC Won’t Cost You Much? How Does $130 Million Sound?
A new lawsuit brings to light the all-too common occurrence of a attack, with this occurring during a business acquisition and costing the …
Homeland Security: U.S. Ransomware Attacks Have Doubled in the Last Year
A March 2022 report from the Senate Committee on Homeland Security and Governmental Affairs zeros in on the growing problem of ransomware and …
Trezor Crypto Wallet Attacks Results in Class Action Lawsuit Against MailChimp Owner Intuit
Months after the MailChimp data breach targeting 102 companies in the crypto sector, a new lawsuit has been filed seeking millions of dollars …
Happy Credit Union Customers Become the Target of Spoofing Scams Due to a Lack of Email Security
Taking advantage of heightened levels of customer trust and satisfaction, along with lowered levels of properly implemented security, credit …
European Wind-Energy Sector Is the Latest Target of Russian State-Sponsored Attacks
While Russia consistently denies any launching of cyberattacks, attack details point to reasonable intent by and cybercriminal ties to the …
Beware of Spoofed Vanity URLs
Researchers at Varonis warn that attackers are using customizable URLs (also known as vanity URLS) on SaaS services to craft more convincing …
KnowBe4 Earns 2022 Top Rated Award from TrustRadius
We are proud to announce that TrustRadius has recognized KnowBe4 with a 2022 Top Rated Award.
Another Report of SEO in Phishing
Researchers at Netskope have observed a 450% increase in phishing downloads over the past twelve months, largely driven by attackers using SEO…
Mustang Panda Uses Spear Phishing to Conduct Cyberespionage
The China-based threat actor Mustang Panda is conducting spear phishing campaigns against organizations in NATO countries and Russia, as well …
CyberheistNews Vol 12 #19 [Heads Up] There is a New Type of Phishing Campaign Using Simple Email Templates
Tricky SMTP Relay Email Spoofing. Man Convicted For 23M Phishing Scam. Email not displaying? | View Knowbe4 …
Wave of Crypto Muggings Hits London's Financial District
Criminals in London are targeting digital currency investors on the street in a wave of “crypto muggings”, with victims reporting that …
Business Email Compromise Shouldn’t Be the Cost of Doing Business
The FBI last week published a public service announcement updating its warnings about the continuing threat of business email compromise (BEC,…
10 of the Craziest Cyberattacks Seen In the Wild and How You Can Avoid Them
It feels like we hear about a new devastating cyberattack in the news every day. And attack methods seem to be proliferating at an exponential…
Your KnowBe4 Fresh Content Updates from April 2022
Check out the 67 new pieces of training content added in April, alongside the always fresh content update highlights and new features.
Cozy Bear Goes Typosquatting
Researchers at Recorded Future’s Insikt Group warn that the Russian threat actor NOBELIUM (also known as APT29 or Cozy Bear) is using …
Microsoft is Leading the Way to a Password-Less Future
As we observe World Password Day to create awareness around the need for password security, Microsoft is looking for frictionless ways to …
SMTP Relay Email Spoofing Technique
Researchers at Avanan have observed a surge in phishing emails that abuse a flaw in SMTP relay services to bypass email security filters.
89% of Organizations Experienced One or More Successful Email Breach Types During the Last 12 Months
With the number of email breaches per year almost doubling in the last three years, organizations still don’t see email security solutions as …
FIN12 Threat Group Speeds Up Ransomware Attacks to Just Two Days After Initial Access
As detection times are reducing across the board, threat groups are improving their craft and are prioritizing speed as the key ingredient in …
Organizations Have a 76% Likelihood of a Successful Cyberattack in the Next Year
New data from TrendMicro and Ponemon shows how almost organizations globally are not fully prepared for the looming threat of almost-certain …
Man Convicted for $23 Million Phishing Scam Against the US DoD
A man in California has been convicted for stealing $23.5 million from the US Department of Defense in a phishing attack. The Justice …
Holding a Great Employee Education Meeting
I recently attended a customer’s annual security awareness training employee event. I have attended a bunch of these over the years and I have…
Phishing Campaign Uses Simple Email Templates
A phishing campaign is using short, terse emails to trick people into visiting a credential-harvesting site, according to Paul Ducklin at …
75% of SMBs Would Only Survive Seven Days or less from a Ransomware Attack
With ransomware attacks on the increase, new data shows a material portion of small and medium business organizations are completely …
Half of IT Leaders Say their Non-Technical Staff are Unprepared for a Cyber Attack
New data shows IT leadership believes users outside of IT create a “continued significant risk to organizations” despite having a layered …
[EYE OPENER] The Ransom Payment is Only 15% of The Total Cost of Ransomware Attacks
As the number of ransomware attacks has increased 24% over the previous year, security researchers estimate the total associated attack costs …
Criminal Gang Impersonates Russian Government in Phishing Campaign
Researchers at IBM Security X-Force are tracking a financially motivated cybercriminal group called “Hive0117” that’s impersonating a Russian …
How Hackers Get Your Passwords and How To Defend Yourself
Despite the world’s best efforts to get everyone off passwords and onto something else (e.g., MFA, passwordless authentication, biometrics, …
Hacking the Hacker: An Inside Look at the Karakurt Cyber Extortion Group
By breaking into an attack server, security researchers have uncovered new details that show the connection between the Karakurt group and …
Nearly all Data Breaches in Q1 2022 Were the Result of a Cyber Attack
New data from the Identity Theft Resource Center shows rises in the number of data compromises following 2021’s record-setting year, all …
Cyber Attacks on the Global Supply Chain Have Increased by 51%
As supply chain vendors become a greater target, the businesses reliant upon them don’t seem to be responding with the appropriate urgency, …
More_eggs Malware Distributed Via Spear Phishing
Threat actors are sending out the stealthy “more_eggs” malware in spear phishing emails that target hiring managers, according to researchers …
Community Associations Confront Social Engineering
It’s not just deep-pocketed corporations that prove attractive targets for social engineering. Any organization that holds information that …
If You Got a “Your Bill Is Paid For” Text, You’re Part of a Massive T-Mobile Texting Scam
The latest scam targeting T-Mobile customers impersonating T-Mobile and focused on collecting your personal data by tempting you with free …
LinkedIn is the Most Impersonated Brand in Phishing Attacks
Social media companies, particularly LinkedIn, are now the most impersonated brands in phishing campaigns, researchers at Check Point have …
New Phishing Attack Targets MetaMask Users for their Crypto Wallet Private Keys
A new phishing campaign impersonates MetaMask, informs victims their cryptocurrency wallets aren’t “verified” and threatens suspension.
UK Information Commissioner: Many Cybersecurity Incidents are “Preventable”
In a recent article about the largest cyberthreats currently facing the UK, John Edwards – the UK’s newly-appointed information commissioner- …
Critical: CISA Warns of Potential Attacks on Infrastructure by Russian State-Sponsored and Criminal Cyber Gangs
In a joint multi-country cybersecurity advisory (CSA), governments are warning their respective critical infrastructure organizations to be …
TraderTraitor: When States do Social Engineering
North Korea’s Lazarus Group is using social engineering attacks to target users of cryptocurrency, according to a joint advisory from the US …
Ransomware Attacks Show Temporary Slowing but are Expected to Increase in 2022 [Graphs]
New data from Recorded Future shows how the war in Ukraine is causing a brief slowdown of ransomware attacks on healthcare, governments and …
Only Half of All Organizations Have Refreshed Their Security Strategy Based on the Pandemic
A new study published by Ponemon Institute shows that a material portion of organizations are still using pre-pandemic security processes and …
FBI Warns of Bank Fraud Phishing Campaign
The FBI has warned of a smishing campaign that’s targeting people in the US with phony bank fraud notifications. The text messages inform …
Social Engineering Campaign against African Banks
A phishing campaign is targeting African banks with a technique called “HTML smuggling” to bypass security filters, according to threat …
“Being Annoying” as a Social Engineering Approach
Attackers are spamming multifactor authentication (MFA) prompts in an attempt to irritate users into approving the login, Ars Technica …
Q1 2022 Report: Holiday-Themed Phishing Emails Get Employees to Click
KnowBe4's latest quarterly report on top-clicked phishing email subjects is here. We analyze the top categories, general subjects (in both the…
Storytelling to Improve Your Organization's Security Culture [PODCAST]
The latest podcast episode of Security Masterminds features our special guest Jim Shields, Creative Director at KnowBe4. He sat down with our …
Reduce Your Chances of Getting Scammed
In today's connected world, nearly everyone has a story where they have been targeted by a scam and either that person or someone they know …
Strategies to Achieve Compliance and Real Risk Reduction at the Same Time
Organizations like yours use regulatory guides and compliance frameworks as the foundation of their list of controls. You can easily have many…
Small and Medium Businesses Account for Nearly Half of all Ransomware Victim Organizations
As ransomware costs increase, along with the effectiveness and use of extortions, smaller businesses are paying the price, according to new …
One in Three U.K. Businesses Experience Cyber Attacks Weekly
New data from the U.K. Government’s Cyber Security Breaches Survey 2022 report shows that a material portion of businesses and charities are …
Meta Stops Three Cyber Espionage Groups Targeting Critical Industries
Impersonating legitimate companies and using a complex mix of fake personas across Facebook, Telegram, and other platforms, these groups used …
Smishing Scams Abuse Name of Legitimate Ukrainian Charity
Researchers at Trend Micro have spotted yet another scam taking advantage of the crisis in Ukraine by impersonating a legitimate charity. In …
CyberheistNews Vol 12 #15 [Heads Up] Hard-boiled Social Engineering by a Fake "Emergency Data Request"
CyberheistNews Vol 12 #15 | Apr. 12th., 2022 [Heads Up] Hard-boiled Social Engineering by a Fake "Emergency Data …
Business Email Compromise (BEC): the Costliest Cybercrime
Organizations in the US lost $2.4 billion to business email compromise (BEC) scams (also known as CEO fraud) last year, according to Alan …
Microsoft Azure's Static Web Apps Service Becomes the New Home for Phishing Attacks
Taking advantage of the value of a legitimate web service, along with a valid SSL certificate, a new campaign of phishing attack targeting …
KnowBe4 Named a Leader in the Spring 2022 G2 Grid Report for Security Awareness Training
We are thrilled to announce that KnowBe4 has been named a leader in the latest G2 Grid Report that compares Security Awareness Training (SAT) …
KnowBe4's PhishER Platform Named a Leader in the Spring 2022 G2 Grid Report for Security Orchestration, Automation, and Response (SOAR)
We are excited to announce that KnowBe4 has been named a leader in the Spring 2022 G2 Grid Report for Security Orchestration, Automation, and …
The Ransomware Hostage Rescue Checklist: Your Step-by-Step Guide to Preventing and Surviving an Ransomware Attack
Skyrocketing attack rates, double and triple extortion, increasing ransom demands… cybercriminals are inflicting pain in every way imaginable …
Phishbait Invokes Russia's Ministry of Internal Affairs (Road Safety Division)
A phishing campaign impersonating WhatsApp has targeted more than 27,000 mailboxes, according to researchers at Armorblox. It’s not clear who …
“Human Error” Ranked as the Top Cybersecurity Threat While Budgets Remain Misaligned
New insights into the state of data security show a clear focus on the weakest part of your security stance – your users – and organizations …
Multi-Million Dollar Scam Call Center Shut Down by Multinational Police Efforts
Last month, Latvian and Lithuanian police – in conjunction with Europol – coordinated a raid on 3 call centers responsible for an …
Mailchimp Phishing Attack Results in Potential Hit on 100K Trezor Crypto Wallets
Stolen client data from Mailchimp put customers of the cryptocurrency hardware wallets on notice of potential social engineering attacks …
“Europol Calling” (Not Necessarily)
Scammers are impersonating Europol with fraudulent phone calls in an attempt to steal personal and financial information, according to …
Microsoft Warns of Lapsus$ “Targeting Organizations for Data Exfiltration and Destruction”
The group behind the recent attacks on Okta, NVIDIA, and Microsoft may be moving on to less-prominent organizations, using their data …
Info Stealer Malware Vidar Uses Microsoft Help Files to Launch Attacks
It appears that the use of Microsoft CHM files is gaining popularity, and from the way this latest attack works, it’s a rather ingenious and …
Ransomware Victims See Ransom Demands and Payments Increase as The Number of Published Data Victims Spikes
Cybercriminals Groups and “as a Service” threat actor affiliates alike seem to be doing well, according to a new report on the state of …
Social Engineering from Tehran
Social engineering continues to be a core component of the Iranian government’s hacking operations, according to researchers at Recorded Future.
CyberheistNews Vol 12 #14 [EYE OPENER] A Lack of Employee Cyber Hygiene is the Next Big Threat
[EYE OPENER] A Lack of Employee Cyber Hygiene is the Next Big Threat Email not displaying? | View Knowbe4 Blog …
Social Engineering by "Emergency Data Request"
Bloomberg has reported that forged "Emergency Data Requests" last year induced Apple and Meta to surrender "basic subscriber details, such as …
Your KnowBe4 Fresh Content Updates from March 2022
Check out the 74 new pieces of training content added in March, alongside the always fresh content update highlights and new features.
Simple Facebook Phishing Scam Takes an Unexpected Turn to Throw Potential Victims Off the Scent
Rather than take the usual path of sending an email and linking to a spoofed logon page, this attack takes a different set of actions that at …
Cisco: Web 3.0 Will be the Next Frontier for Social Engineering and Phishing Attacks
A look at what makes up Web 3.0 and how it may be used includes insight into what kinds of cyberattacks may plague it, as cybercriminals look …
Cost of Internet Crimes in 2021 Increase 64% Exceeding $6.9 Billion
New data from the FBI’s Internet Crime Complaint Center (IC3) shows a massive increase in the cost of internet crimes, with phishing and BEC …
Obvious Phishbait, But Someone Will Bite
A widespread phishing scam is circulating in Facebook Messenger, according to Jeff Parsons at Metro. The phishing messages simply contain the …
FBI Warns of Phishing Attacks Targeting Election Officials
The FBI has issued a Private Industry Notification warning of phishing emails designed to steal login credentials from election officials. The…
A Lack of Employee Cyber Hygiene is the Next Big Threat
A new report suggests that everything from endpoints, to passwords, to training, to security policies, to a lack of awareness is all …
Ransomware Attack Volume Increases by 18% As the Number of Variants Jumps to 34 in Only One Quarter
A new report reviewing ransomware activity in 2021 shows an impressive uptick in the number of targeted attacks in Q4 of 2021 to 772 as more …
Mobile Device Usage Have Led to Security Incidents in Nearly Half of Organizations
The shift in devices used by today’s workforce has resulted in increases in cybersecurity concerns and incidents, despite a majority of orgs …
CyberheistNews Vol 12 #13 [Heads Up] Published Zelenskyy Deepfake Video Demonstrates the Modern War is Online
[Heads Up] Published Zelenskyy Deepfake Video Demonstrates the Modern War is Online Email not displaying? | View Knowbe4 Blog …
Email Conversation Hacking to Distribute Malware
Researchers at Intezer warn that attackers are hijacking email conversations to distribute the IcedID banking Trojan. This technique makes the…
Making Better Push-Based MFA
I used to be a huge fan of Push-Based Multifactor Authentication (MFA), but real-world use has shown that most of today’s most popular …
Buy Now, Pay Later Scams
Fraudsters are taking advantage of the buy-now, pay-later (BNPL) payment model, according to Jim Ducharme, COO of Outseer. On the CyberWire’s …
WIRED: "A Mysterious Satellite Hack Has Victims Far Beyond Ukraine"
WIRED wrote: "More than 22,000 miles above Earth, the KA-SAT is locked in orbit. Traveling at 7,000 miles per hour, in sync with the planet’s …
Fidelity: "Why cybersecurity is material to all industries"
Fidelity just published an article titled "Cybersecurity: A growing risk". They note that the threat of Russian cyberattacks highlights …
Repertoire of Ukraine Charity Phishing Scams
Scammers continue to exploit the crisis in Ukraine, according to researchers at Bitdefender. Over the past week, the researchers believe the …
Initial Access Broker Group Relies on Social Engineering
Google’s Threat Analysis Group (TAG) describes a cybercriminal group it calls “EXOTIC LILY” that acts as an initial access broker for numerous…
Try the New Compliance Audit Readiness Assessment Today for the SSAE18 Framework
When it's time to complete a compliance audit, are you thinking, "Ugh, is it that time again?" And, as more organizations demand proof that …
Number of Phishing Attacks Hits an All-Time High in 2021, Tripling That of Early 2020
New data from the Anti-Phishing Working Group shows cybercriminals are stepping on the gas, focusing phishing attacks on credential theft and …
Phishing Attack-Turned-Wire Fraud Case Sees a Win for the Policyholder
In an unusual turn of events, a recent court decision sided with the policyholder, despite specific policy language that probably should have …
QakBot Banking Trojan Evolves and Now Takes Over Email Conversations to Spread Malware
As if stealing all your credentials, cookies, and email wasn’t bad enough, this new version of QakBot inserts itself into your emails, …
Phishing Scam with Fraudulent Invoice Costs City of Fresno Over $600,000
This simple invoice scam appears to be a part of a much broader campaign targeting municipalities, posing as existing subcontractors.
Exploiting Trust in reCAPTCHA
Researchers at Avanan warn that attackers are using reCAPTCHAs on their phishing sites to avoid detection by security scanners.
Published Zelenskyy Deepfake Video Demonstrates the Modern War is Online
The video uploaded to a hacked Ukrainian news website shows how far the technology has come, how it can be used in social engineering, as well…
SMBs Are 350% More Likely to Experience Social Engineering Attacks Via Phishing
New data shows phishing, social engineering, and impersonation dominate as cybercriminals are becoming more frequent and successful with their…
CyberheistNews Vol 12 #12 [New White House Alert] Train Your Users Against Threat of Russian Cyberattacks
[New White House Alert] Train Your Users Against Threat of Russian Cyberattacks Email not displaying? | View Knowbe4 Blog …
[BREAKING] White House warns Russia is prepping possible cyberattacks against US
With the recent cyber-attacks between Russia and Ukraine and the current intelligence coming from the US Government, organizations want to …
Chameleons Phish, Too
One of the challenges cyber criminals face is that their scams often have a relatively short shelf-life. Once they’ve been used, the gaff is …
[Heads Up] New Evil Ransomware Feature: Disk Wiper if You Don't Pay
There is a new ransomware-as-a-service (RaaS) strain called LokiLocker, researchers at Blackberry warn. The malware uses rare code obfuscation…
KnowBe4 Named a Leader in The Forrester Wave for Security Awareness and Training Solutions
We’re thrilled to announce that KnowBe4 has been named a Leader in The Forrester WaveTM : Security Awareness and Training Solutions, Q1 2022 …
Ransomware-Related Data Leaks Increase 82% as the Number of Cybercriminal Groups Nearly Triples
New insight into the state of the attacks and threats paints a picture where the cybercriminals are growing in number, sophistication and …
Backups Become the Focus as Three-Fourths of Organizations Experienced Ransomware Attacks
New data puts the spotlight on how most organizations unable to completely recover their data after a ransomware attack, making the case for …
New Phishing Method Uses VNC to Bypass MFA Measures and Gives Cybercriminals Needed Access
Despite cloud vendors like Google detecting reverse proxies or man-in-the-middle (MiTM) attacks and halting logons to thwart malicious …
[Eye Opener] Ukraine Is Now Being Hit With 4 Different Strains Of Wiper Malware
Newly discovered data-destroying malware was found this week in attacks targeting Ukrainian organizations and deleting data across systems on …
We Are In The First Open Source Intelligence War
I am a member of OODA loop. They are a great team that keeps me up to date about InfoSec issues. Their site always has interesting articles …
CyberheistNews Vol 12 #11 [Heads Up] FBI: Ransomware Gang Breached 52 U.S. Critical Infrastructure Orgs
[Heads Up] FBI: Ransomware Gang Breached 52 US Critical Infrastructure Orgs Email not displaying? | View Knowbe4 Blog …
Shipping Fraud Rises Nearly 800% in 2021
Shipping fraud had a global increase of nearly 800% over the course of 2021, according to TransUnion’s 2022 Global Digital Fraud Trends Report.
Cybercrime-as-a-Service: Its Evolution and What You Can Do to Fight Back
The cybercrime market has skyrocketed in a frightening way. With threats such as ransomware to Business Email Compromise (BEC), the stakes are…
Social Engineering through Contact Form
Email is the familiar form of phishing, but there’s an ongoing criminal campaign that follows a different, arguably subtler avenue of …
Email-Based Vishing Attacks Skyrocket 554% as Phishing, Social Media, and Malware Attacks Are All on the Rise
New analysis of attacks in 2021 show massive increases across the board, painting a very concerning picture for this year around cyberattacks …
“Warm Greetings” (or not) : Saudi Aramco Impersonation
Researchers at Malwarebytes warn of a phishing campaign that’s targeting the oil and gas industry by impersonating Saudi Aramco.
Phishing and Scam Pages Increase by 153% as Cybercriminals Seek to Establish Credibility
As part of either impersonating known brands or simply leveraging credible cloud services, the use of a web page as part of an attack has …
Passwords are Reused 64% of the Time as the Number of Passwords to Remember Reaches Over 100
New data focusing on user cyber hygiene around password use shows users are repeatedly reusing passwords across multiple applications and …
KnowBe4's Position On Recent Russian Aggression
The unprovoked attack on the Ukrainian people, and subsequent humanitarian crisis it has caused, is an unacceptable act of aggression by the …
83% of all Successful Ransomware Attacks Featured Double and Triple Extortion
With 2021 being the “testing ground” for ransomware extortion, 2022 is showing signs of ransomware gangs settling in on proven extortion …
Social Engineering a Major Factor in Cyberattack on Camera Maker Axis Communications
As details of the February attack continue to be divulged, it becomes evident that cybercriminals were able to get past both users and …
Up and To the Right: Ransomware Attacks Grow by 105% in 2021
New data from Sonicwall shows the numbers of nearly every type of attack growing in 2021, with concerns by organizations about attacks and …
Domains Associated with Phishing Directed Against Ukraine
Researchers from Secureworks’ Counter Threat Unit (CTU) are tracking phishing domains used by the “MOONSCAPE” threat actor to target users in …
Phishing Impersonation and Attack Trends in 2021
Facebook overtook Microsoft as the most impersonated brand in phishing attacks last year, according to a new report from Vade Secure.
CyberheistNews Vol 12 #10 [Heads Up] A New Phishing Attack Warns About A Suspicious Russian Login
[Heads Up] A New Phishing Attack Warns About A Suspicious Russian Login Email not displaying? | View Knowbe4 Blog …
[World Premiere] KnowBe4’s New Season 4 of Netflix-Style Security Awareness Video Series - ‘The Inside Man’
We’re thrilled to announce the long-awaited fourth season of the award-winning KnowBe4 Original Series - ‘The Inside Man’ is now available in …
FBI: Ransomware gang breached 52 US critical infrastructure orgs
The US Federal Bureau of Investigation (FBI) says the Ragnar Locker ransomware gang has breached the networks of at least 52 organizations …
By the Way, There's No Draft - Smishing Campaign Alert
Scammers are sending phony text messages (aka Smishing or SMS Phishing) informing people in the US that they’ve been drafted by the US Army, …
Log4j - Kevin Mitnick Explains One of the Most Serious Vulnerabilities in the Last Decade
The Log4j vulnerability caused widespread panic for IT professionals when it was uncovered. Sleepless nights followed for many. But a …
The Recent Log4J Vulnerability Equation: Remote Code Execution (RCE) + National Vulnerability Database (NVD) = 10.0
RCE. These three letters add increased levels of stress to cybersecurity professionals regarding vulnerabilities against their hardware or …
According to KnowBe4 Research's Q1 2022 Report: Shadow IT Is Real
Imagine needing to share a large PDF non-confidential document with a customer. It is too large to send via email, and recently you started …
Phishing Attacks Impersonating LinkedIn are up 232% in the Last Month Alone!
During the period the world has dubbed “the great resignation”, phishing scammers are shifting tactics to take advantage of those looking for …
FBI: Scammers Take Business Email Compromise Attacks to Virtual Meeting Platforms
In a new twist on an old scam, BEC attacks switch from email to a virtual meeting where social engineering tactics are used to further …
CISA: 2021 Cyberattack Trends Indicate Increases in Global Ransomware Attacks
New advisory sees critical infrastructure once again in the crosshairs and makes critical recommendations to both protect against ransomware …
Your KnowBe4 Fresh Content Updates from February 2022
Check out the 28 new pieces of training content added in February, alongside the always fresh content update highlights and new features.
What It's Like to Be the Face of Romance (Scams)
A real US Army colonel named Daniel Blackmon is being impersonated in hundreds or even thousands of romance scams, according to Haley Britzky …
Gain Insight into Where Your Organization Stands with the Security Culture Maturity Model
We’re thrilled to introduce the Security Culture Maturity Model, the industry’s first maturity model specifically geared to measure security …
Data Breach Volumes in the U.S. Grow by 10% in 2021
New data shows despite decreases in global data breach levels (-5%) in 2021, the U.S. experienced proportionally more data breaches than in …
Timely “Help Ukraine” Online Crypto Scams Take in Millions
A new series of "help Ukraine" donation posts have sprouted up across the Internet, but are really a cryptocurrency scam enticing users send …
FBI: SIM Swapping Attacks See More Than 500% Increases in The Number of Attacks and Monetary Losses
With mobile devices used as secondary authentication, threat actors have been stepping up activity, looking for ways to transfer phone numbers…
UK ICO Sees a Massive Increase in Targeted Email Attacks
New data obtained from the UK’s Information Commissioner’s Office by think tank Parliament Street shows an unprecedented rise in attacks …
Phishing Emails Warn of a Suspicious Login From Russia
Researchers at Malwarebytes warn that a phishing campaign is informing users that someone logged into their account from an IP address in …
CyberheistNews Vol 12 #09 [Heads Up] The Ukraine War Started A New Wiper Malware Spillover Risk
[Heads Up] The Ukraine War Started A New Wiper Malware Spillover Risk Email not displaying? | View Knowbe4 Blog …
Scammers Will Take Advantage of New IRS Rules
New IRS requirements will soon be used as phishbait, according to Gene Marks, owner of Marks Group PC and a columnist for the Guardian.
Russia Could “Absolutely” Lash Out at US Through Cyber, Lawmaker Warns
NextGov reports: "Chairman Sen. Mark Warner, D-Va, gives an opening statement as FireEye CEO Kevin Mandia, SolarWinds CEO Sudhakar …
[Heads Up] There Is A Whole New Type of Blockchain Scam Called "Ice phishing"
In a post Wednesday last week, Microsoft issued a warning that they are seeing a brand new type of blockchain-centric attack aimed at web3 -- …
Wartime Suffering as Phishbait
It’s easy to forget, when a hybrid war like the one currently raging in Ukraine is occupying so much attention, that ordinary criminal …
Conti Ransomware Attacks Reap in $180 Million in 2021 as Average Ransomware Payments Rise by 34%
New analysis of ransomware attacks shows growth in the number of active strains, ransoms collected, and use of third-party services all adding…
[EYES OPEN] The Kremlin Propaganda Machine Now Works Overtime. INFOGRAPHIC
With an ongoing land war in Ukraine, everyone needs to be alert for the Kremlin's parallel disinformation campaigns. Many people simply are …
Coinbase’s QR Code Superbowl Ad Only Helps Normalize QR-Based Scams
Use of QR codes is becoming a mainstream part of advertising, but also is getting the attention of scammers intent on redirecting you to a …
[Heads Up] The Ukraine War Started A New Wiper Malware Spillover Risk
The war in Ukraine increases the risk of wiper malware to spill over. I'm sure you remember NotPetya, which caused billions of dollars of …
Scammers Use a Mix of Stolen Credentials, Inbox Rules, and a Rogue Outlook Client Install to Phish Internal and External Victims
Organizations that are not using Microsoft’s multi-factor authentication are finding themselves victims of credential attacks that involve …
When the Phishers Want a Reply, not a Click
A sextortion phishing campaign is targeting French speakers accusing them of viewing child abuse content, according to Paul Ducklin at Naked …
Traits of Most Scams
There are a lot of scams in the world, and they seem to be proliferating at an exponential rate. My Facebook friend’s accounts are compromised…
CyberheistNews Vol 12 #08 [Eye Opener] Here Are the 4 Traits of Most Scams
CyberheistNews Vol 12 #08 | Feb. 22nd., 2022 [Eye Opener] Here Are the 4 Traits of Most Scams Written by Roger …
Phishing Attacks on Social Media Doubled Over 2021
Phishing attacks on social media doubled over the course of 2021, according to a new report from PhishLabs by HelpSystems. Most (68%) of these…
20 Year-Old “Right-to-Left Override” Functionality Used in Attacks to Trick Microsoft 365 Users Out of Credentials
Used to disguise malicious file extensions, this legacy functionality is being repurposed in attacks to obfuscate attachment types and steal …
New QBot Attack Only Takes 30 Minutes to Elevate Privileges and Steal Data
This banking trojan-turned-information-stealer has been around for nearly 15 years. But its latest iteration – seen even in the past few weeks…
New Phishing Campaign Angles for Monzo Banking Customers
A phishing campaign is targeting users of the UK-based digital banking company Monzo, BleepingComputer reports. Security researcher William …
Meta Files Lawsuit Over Phishing Attacks
Meta (Facebook’s corporate parent) and the digital banking company Chime have filed a joint lawsuit against two Nigerian citizens for …
CyberheistNews Vol 12 #07 [Heads Up] FBI Warns Against New Criminal QR Code Scams
[Heads Up] FBI Warns Against New Criminal QR Code Scams Email not displaying? | View Knowbe4 Blog CyberheistNews Vol …
Incredible Email Hacks You'd Never Expect and How You Can Stop Them
If you think the only way your network and devices can be compromised via email is phishing, think again!
Phishing Campaign Targets NFT Speculators
Scams follow fashion because money follows fashion. So it’s no surprise that non-fungible tokens (NFTs), which have become a hot speculative …
FBI: Scammers Exploit Job Posting Sites with Fake Jobs to Steal Money and Personal Information
In the wake of the great reset, cybercriminals are finding success posing as legitimate companies in job postings seeking new hires on …
Why multicloud environments can help improve security and redundancy
Read More Single-cloud environments are said to be redundant. One expert disagrees and explains why. The post Why multicloud environments can help …
Cyber threat intelligence is a great way for a company to improve its security
Read More Get to know the ins and outs of cyber threat intelligence and how your company's security can be can be strengthened by putting threat …
How to protect yourself against website trackers in Firefox
Read More If you'd like a little more privacy when surfing the web, Firefox offers a few different options to defend yourself against trackers. The …
How to generate secure passwords for your accounts
Read More A password generator can help when you need a strong and complex password to protect an account. The post How to generate secure passwords…
Cyberattack threat: Corporate users infected via Microsoft Teams
Read More Corporate users are more aware of phishing attacks in their mailboxes. Yet they are not used to being targeted via other systems like …
How to add notes to iCloud passwords in macOS 12.3 and iOS 15.4
Read More Learn how to securely store notes along with your account credentials with iCloud Keychain and sync them to all of your Apple devices. The…
INDUSTRIAL CYBERSECURITY: Monitoring & Anomaly Detection
Read More To build an effective ICS cybersecurity strategy, it is crucial to identify the security events that are most likely to occur. This will …
Whitepaper: Dell Technologies How Intrinsic Security Protects Against Business Disruption
Read More When it comes to IT, disruption is just another day at the office. From fending off cyberattacks to incorporating leading-edge …
Whitepaper: Dell Technologies Securing Endpoints Amit New Threats
Read More Giving employees the flexibility to be fully productive while working remotely makes it critical that businesses have endpoint security …
Don’t browse on public Wi-Fi without a VPN
Read More Cybersecurity is critical in today's online world. Whether you're a business or a private individual, you need a VPN. Try this one while …
Metaverse companies face 60% more attacks last year, and 5 other online fraud statistics
Read More It was a banner year for online fraudsters. Almost every industry saw an attack spike, with online fraud jumping 85% year over year in …
Report: Pretty much every type of cyberattack increased in 2021
Read More The only category to decrease was malware attacks, but SonicWall said in its report that even that number was deceptive. The post Report:…
How to choose the right data privacy software for your business
Read More Data privacy software can help protect your employees, customers and organization by ensuring data is protected and handled appropriately …
Brand Impersonation and the Healthcare Sector
The healthcare sector is particularly vulnerable to phishing attacks, according to Mike Azzara at Mimecast. Employees in the healthcare …
Introducing the New 'Security Masterminds' Podcast
We're excited to announce that we have launched a new podcast called "Security Masterminds”! This podcast covers a range of topics in …
Updated Ransomware Hostage Rescue Manual
Ransomware is one of the most damaging types of cyber attacks of all time, and the one feared the most by business owners and cybersecurity …
New Cyberattack Campaign Delivers Multiple RATs via Trusted Cloud Services
Abusing cloud providers including Microsoft Azure and AWS, cybercriminals are setting up malicious infrastructure to hide their operations and…
Engaging Your Remote Workforce: Go Beyond Compliance with Training
Even after the pandemic ends, many employees say they want to stay home and continue to work remotely. A recent study by the Mckinsey & …
Guide for comparison of cloud security solutions (German)
Read More In 2021, securing your network is more challenging than ever – you need to secure users, devices, apps, and data at the point of access, …
Blackberry report reveals SMBs face increased threat of cyber crime
Read More Blackberry details a number of different threats of concern for enterprises to be aware of in the year ahead. The post Blackberry report …
Researchers discover common threat actor behind aviation and defense malware campaigns
Read More Dubbed TA2541 by Proofpoint researchers, the group has been attacking targets in several critical industries since 2017 with phishing …
Dell Technologies Securing Endpoints Amit New Threats
Read More Giving employees the flexibility to be fully productive while working remotely makes it critical that businesses have endpoint security …
Dell Technologies How Intrinsic Security Protects Against Business Disruption
Read More When it comes to IT, disruption is just another day at the office. From fending off cyberattacks to incorporating leading-edge …
FBI: Criminals escalating SIM swap attacks to steal millions of dollars
Read More The federal agency says hundreds of victims have lost money due to scams over a two-year span. The post FBI: Criminals escalating SIM swap…
iOS users: Patch now to avoid falling prey to this WebKit vulnerability
Read More iPhones, iPads and the iPod Touch are all at risk, and it doesn’t matter what web browser you use: All of them could let an attacker …
Hybrid work and the Great Resignation lead to cybersecurity concerns
Read More Code42’s study goes into detail about the risks facing cybersecurity leaders and practitioners in the wake of the Great Resignation. The …
Why a safe metaverse is a must and how to build welcoming virtual worlds
Read More Virtual worlds need strong and enforceable rules to avoid the harassment and stalking so common on social media platforms. The post Why a …
How to enable end-to-end encryption in Facebook Messenger
Read More To keep your Facebook Messenger conversations private and secured, you should start using the new end-to-end encryption feature. Jack …
Top 5 alternatives to Chrome
Read More Tom Merritt offers five great options if you’re ready to dump Google Chrome for good. The post Top 5 alternatives to Chrome appeared first…
5 password manager deals you don’t want to miss
Read More Stay safe online while simplifying your life with a password manager. Here are some to try at great prices. The post 5 password manager …
Reduce your network’s attack surface with Zero Trust Network Access
Read More Perimeter 81’s cloud-delivered, user-friendly platform offers a seamless SaaS interface with a feature-rich experience including built-in …
Hackers have begun adapting to wider use of multi-factor authentication
Read More Proofpoint researchers have found that “phish kits” available for purchase online are beginning to adapt to MFA by adding transparent …
10 best practices for Windows workstation password changes over a VPN
Read More Remote password changes on company-issued workstations can sometimes yield chaotic results. Follow these best practices to help ensure you…
Electronic Data Disposal Policy
Read More Electronic data is likely to be more prevalent in today’s organizations than physical printed data. Reams worth of documents can now be …
Imperva fellow explains why data privacy is about much more the breaches and just knowing where your data is
Read More What does data security really mean? Terry Ray, SVP and fellow with Imperva, talks about how companies need to think about data privacy in…
5 services and tools helping companies with digital safety
Read More We often hear and read about digital security, but digital safety concerns have also become a key issue for online platforms, creating a …
GitLab on how DevSecOps can help developers provide security from end-to-end
Read More GitLab's VP of security talks about the efficiencies that DevSecOps brings to developers and the software development process. The post …
5 ways to improve the governance of unstructured data
Read More Bringing big data governance and security up to the level of practice applied to structured data is critical. Here are five ways to get …
How to use DuckDuckGo on your PC and mobile devices
Read More You can use the privacy-oriented search tool through desktop browser extensions and a mobile app. The post How to use DuckDuckGo on your …
Collaborate with portions of your Bitwarden Vault with Organizations
Read More Bitwarden makes it easy to share items from within the password manager to teams and other groups of users. Jack Wallen shows you how to …
IBM and Snyk: Developers must lead the charge on cybersecurity
Read More IBM developer advocate and the founder of Snyk talk about changing the way developers think about cybersecurity. The post IBM and Snyk: …
Secureworks Threat Intelligence Executive Report 2021 Vol 6
Read More The Secureworks Counter Threat Unit™ (CTU) research team analyses security threats and helps organizations protect their systems. During …
XDR Buyer’s Guide
Read More The XDR market is confusing, as is often the case with new security technologies Don’t wait to be proactive about your organisation’s …
Roaming Mantis mobile smishing campaign spreads, gets updated features
Read More First spotted targeting APAC countries in 2018, Roaming Mantis recently received updates allowing it to steal more data and has begun …
2021 State of the Threat Report: A year in Review
Read More Ransomware remains the number one threat for most organisations. This report comprehensively examines the adversary’s ongoing innovation …
Are IT and OT losing the ransomware battle?
Read More A report from Claroty finds ransomware attacks against critical infrastructures rampant, and paying ransoms often results in less downtime…
Kaspersky: Many wearables and healthcare devices are open to attack due to vulnerable data transfer protocol
Read More Security analysts found 33 weak points in MMQT, a frequently used protocol that rarely involves authentication or encryption. The post …
Symantec finds evidence of continued Russian hacking campaigns in Ukraine
Read More APT group Armageddon was identified as acting against Ukraine late last year, and Symantec’s own data backs up that presented by The …
Bring a burner to the Olympics, and other mobile device travel safety tips
Read More Those traveling to China for the 2022 Winter Olympics have been advised to bring burner phones. Here’s how to use travel tips like that …
Report: Data breach numbers may not actually be declining, and reporting them is getting slower
Read More Flashpoint and Risk Based Security’s report found that, despite early reports, the total number of breaches is likely much higher than …
What your organization can learn from the $324 million Wormhole blockchain hack
Read More The hacker that made off with millions from blockchain bridge service Wormhole exploited an incredibly common coding error that could be …
Cybersecurity incident response: The 6 steps to success
Read More Cybersecurity incident response is not only about handling an incident – it’s also about preparing for any possible incident and learning …


